
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Phishers abuse Google OAuth to spoof Google in DKIM replay assault
Apr
Phishers abuse Google OAuth to spoof Google in DKIM replay assault
Cyber investigation
In a moderately artful assault, hackers leveraged a weakness that allowed them to ship a false electronic mail that gave the influence delivered from Google’s methods, passing all verifications nonetheless pointing to a untrue page that serene logins.
The attacker leveraged Google’s infrastructure to trick recipients into accessing a sound-attempting “toughen portal” that asks for Google myth credentials.
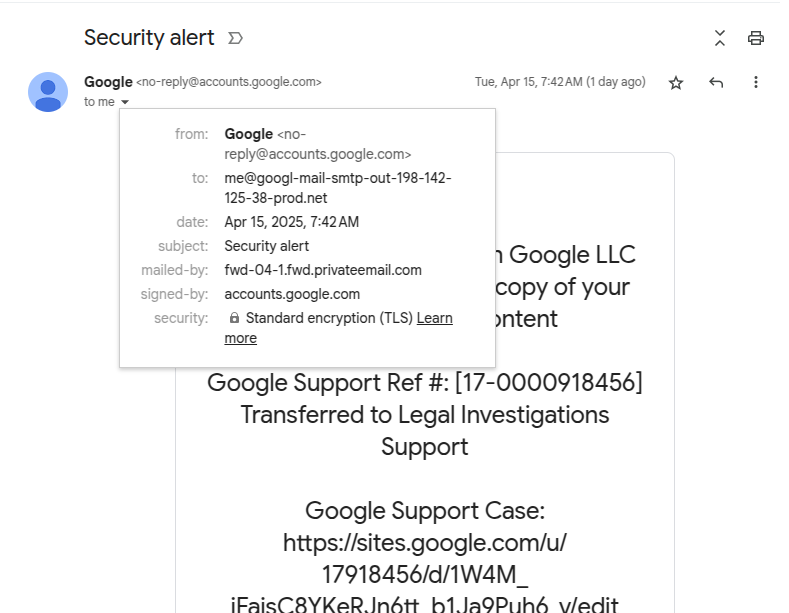
The untrue message perceived to come from “no-acknowledge@google.com” and passed the DomainKeys Known Mail (DKIM) authentication strategy nonetheless the loyal sender modified into once diversified.
False electronic mail with Google’s DKIM put
Prick Johnson, the lead developer of the Ethereum Identify Carrier (ENS), bought a security alert that perceived to be from Google, informing him of a subpoena from a law enforcement authority soliciting for his Google Epic content.
Almost all the pieces seemed legitimate and Google even placed it with other legitimate security signals, which could possibly presumably possibly presumably seemingly trick much less technical customers that don’t know the assign to uncover for the indicators of fraud.
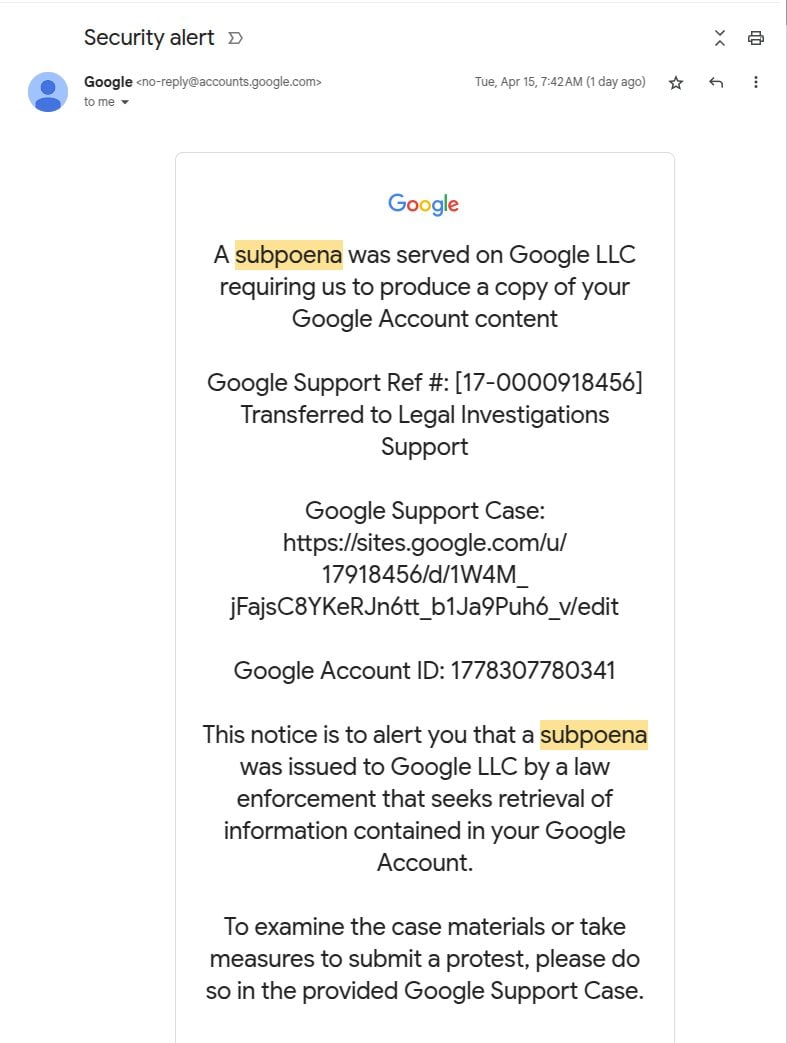
offer: Prick Johnson
Nonetheless, Johnson’s keen spy seen that the false toughen portal in the electronic mail modified into once hosted on websites.google.com – Google’s free web-constructing platform, which raised suspicion.
Being on a Google domain, the percentages of the recipient to esteem they’re being focused are lower.
Johnson says the false toughen portal modified into once “an proper replica of the loyal suppose” and “the proper designate it be a phish is that it be hosted on websites.google.com as another of accounts.google.com.”
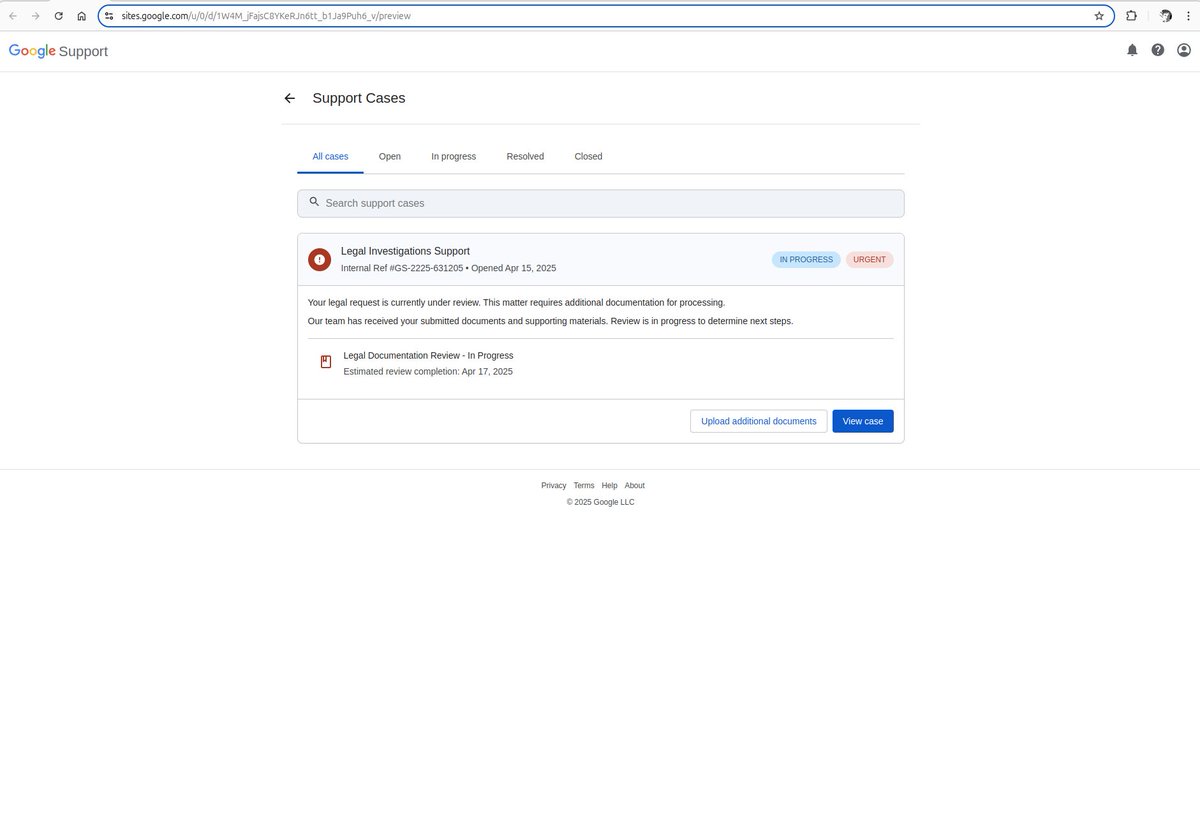
offer: Prick Johnson
The developer believes that the motive of the untrue residing modified into once to rep credentials to compromise the recipient’s myth.
The false portal is easy to point to in the rip-off nonetheless the artful fragment is popping in a message that looks to fill passed Google’s DKIM verification in what is named a DKIM replay phishing assault.
A more in-depth uncover on the electronic mail indispensable solutions unearths that the mailed-by header exhibits a odd take care of than Google’s no-acknowledge and the recipient is a me@ take care of at a domain made to uncover esteem it’s managed by Google.
On the opposite hand, the message modified into once signed and delivered by Google.
offer: Prick Johnson
Johnson establish the clues together and discovered the fraudster’s tricks.
“First, they register a domain and develop a Google myth for me@domain’. The domain is not that indispensable nonetheless it helps if [sic] looks esteem some more or much less infra. The replacement of ‘me’ for the username is artful,” the developer explains.
The attacker then created a Google OAuth app and aged for its name the final phishing message. At one point, the message contained plenty of whitespace to create it uncover esteem it ended and to separate it from Google’s notification about having receive entry to to the attacker’s me@domain electronic mail take care of.
When the attacker granted their OAuth app receive entry to to their electronic mail take care of in Google Workspace, Google automatically despatched a security alert to that inbox.
“Since Google generated the electronic mail, it be signed with a legitimate DKIM key and passes the final exams,” Johnson says, adding that the final step modified into once to ahead the safety alert to victims.
The weakness in Google’s methods is that DKIM exams most attention-grabbing the message and the headers, with out the envelope. Thus, the false electronic mail passes signature validation and looks legitimate in the recipient’s inbox.
Furthermore, by naming the untrue take care of me@, Gmail will suppose the message as if it modified into once delivered to the sufferer’s electronic mail take care of.
EasyDMARC, an electronic mail authentication firm, also detailed the DKIM replay phishing assault Johnson described and supplied technical explanations for each and every step.
PayPal choice abused in the the same come
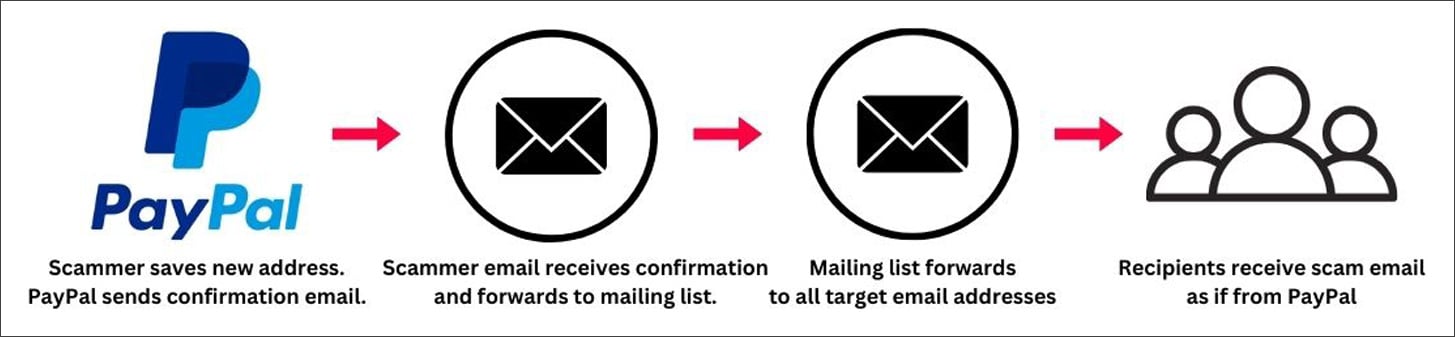
A identical trick has been tried on other platforms than Google. In March, a campaign focusing on PayPal customers relied on the the same strategy, the assign untrue messages originated from the financial firm’s mail servers and passed DKIM security exams.
BleepingComputer’s tests printed that the attacker aged the “gift take care of” choice to link a novel electronic mail to their PayPal myth.
There are two fields when adding a novel take care of and the attacker stuffed one with an electronic mail and pasted the phishing message into the 2d.
PayPal automatically sends a confirmation to the attacker’s take care of, which forwards it to a mailing checklist that relays it to the final in all probability victims in the group.
offer: BleepingComputer
BleepingComputer reached out to PayPal regarding the discipline nonetheless by no plan bought a response.
Johnson also submitted a bug yarn to Google and the firm’s preliminary acknowledge modified into once that the strategy modified into once working as intended.
Nonetheless, Google later reconsidered the discipline, recognizing it as a possibility to its customers, and is currently working to repair the OAuth weakness.
Recent Posts
- ‘Nip/Tuck,’ ‘FBI: Most Wanted’ superstar Julian McMahon tiring at 56
- Julian McMahon, ‘Implausible Four,’ ‘Nip/Tuck’ and ‘FBI: Most Wished’ Star, Dies at 56
- Julian McMahon Dies: ‘Nip/Tuck’, ‘Improbable Four’, ‘FBI: Most Wanted’ Well-known person Used to be 56
- Hackers In the help of $140M Brazil Banking Heist Turn to Crypto to Launder Their Loot
- Cyberattacks might per chance exploit house photograph voltaic panels to disrupt energy grids


