-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > WordPress Motors theme flaw mass-exploited to hijack admin accounts

Jun
WordPress Motors theme flaw mass-exploited to hijack admin accounts
Cybersecurity expert

Hackers are exploiting a severe privilege escalation vulnerability within the WordPress theme “Motors” to hijack administrator accounts and construct complete benefit watch over of a centered dwelling.
The malicious job changed into once noticed by Wordfence, which had warned closing month in regards to the severity of the flaw, tracked beneath CVE-2025-4322, urging customers to upgrade at once.
Motors, developed by StylemixThemes, is a WordPress theme in vogue among car-linked websites. It has 22,460 gross sales on the EnvatoMarket and is backed by an active community of customers.
The privilege escalation vulnerability changed into once found out on Would possibly well perhaps maybe 2, 2025, and first reported by Wordfence on Would possibly well perhaps maybe 19, impacting all variations sooner than and including 5.6.67.
The flaw arises from an corrupt particular person identification validation at some point soon of password updating, permitting unauthenticated attackers to change administrator passwords at will.
StylemixThemes launched Motors model 5.6.68, which addresses CVE-2025-4322, on Would possibly well perhaps maybe 14, 2025, but many customers failed to have a look on the change by Wordfence’s disclosure and got exposed to elevated exploitation effort.
As Wordfence confirms in a brand current writeup, the assaults began on Would possibly well perhaps maybe 20, handiest a day after they publicly disclosed the particulars. Wide-scale assaults were noticed by June 7, 2025, with Wordfence reporting blockading 23,100 makes an wrestle its customers.
.jpg)
Supply: Wordfence
Cybersecurity expert Assault course of and signs of breach
The vulnerability is within the Motors theme’s “Login Register” widget, including password restoration functionality.
The attacker first locates the URL where this widget is placed by probing /login-register, /myth, /reset-password, /signin, etc., with specially crafted POST requests till they fetch a success.
The build a query to comprises invalid UTF-8 characters in a malicious ‘hash_check’ value, inflicting the hash comparison within the password reset logic to be successful incorrectly.
The POST body comprises a ‘stm_new_password’ value that resets the particular person password, concentrated on particular person IDs that on the total correspond to administrator customers.
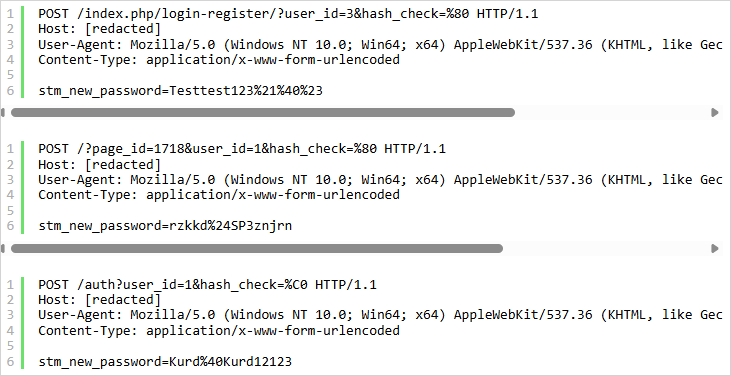
Supply: Wordfence
Attacker-home passwords noticed within the assaults up to now comprise:
- Testtest123!@#
- rzkkd$SP3znjrn
- Kurd@Kurd12123
- owm9cpXHAZTk
- db250WJUNEiG
Once fetch admission to is obtained, the attackers log into the WordPress dashboard as administrators and accomplish current admin accounts for persistence.
The surprising appearance of such accounts mixed with current administrators being locked out (passwords now no longer working) are signs of CVE-2025-4322 exploitation.
Wordfence has also listed loads of IP addresses that initiate these assaults within the yarn, which WordPress dwelling homeowners are suggested to placed on their block listing.
Cybersecurity expert Why IT teams are ditching handbook patch management
Patching historical to signify complex scripts, prolonged hours, and never-ending fireplace drills. No longer anymore.
On this current information, Tines breaks down how as a lot as date IT orgs are leveling up with automation. Patch faster, decrease overhead, and focal point on strategic work — no complex scripts required.
Tags
- cybercrime cybercrimephishing-attack cybersecurity email-fraud forensics|digital-forensics hacker Investigation malware Motors online-scam private-detective scam|fraud private-eye cyber|cybersecurity private-eye phishing|phishing-attack private-investigator private-investigator hacking|hacker WordPress
Recent Posts
- US Fatherland Safety Investigates Whether Bovino Made Disparaging Comments About Jewish Faith
- Missing Lady Last Seen Stressful To Bag Out Family’s Car Is Found Ineffective in Yard Days Later
- Rhode Island Priests Abused A total bunch of Adolescents Over A protracted time, Document Finds – The Unusual York Conditions
- FBI seizes LeakBase cybercrime forum, files of 142,000 members
- The TikTokers Discovering out the Epstein Recordsdata So You Don’t Like To



