
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Tag: private-investigator hacking|hacker
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > private-investigator hacking|hacker
FBI: End-of-lifestyles routers hacked for cybercrime proxy networks
OSINT The FBI warns that chance actors are deploying malware on quit-of-lifestyles (EoL) routers to convert them into proxies sold on the 5Socks and Anyproxy networks. These devices, which were launched decades inspire and no longer salvage safety updates from their vendors, are liable to exterior attacks leveraging publicly on hand exploits to inject power malware. […]
May
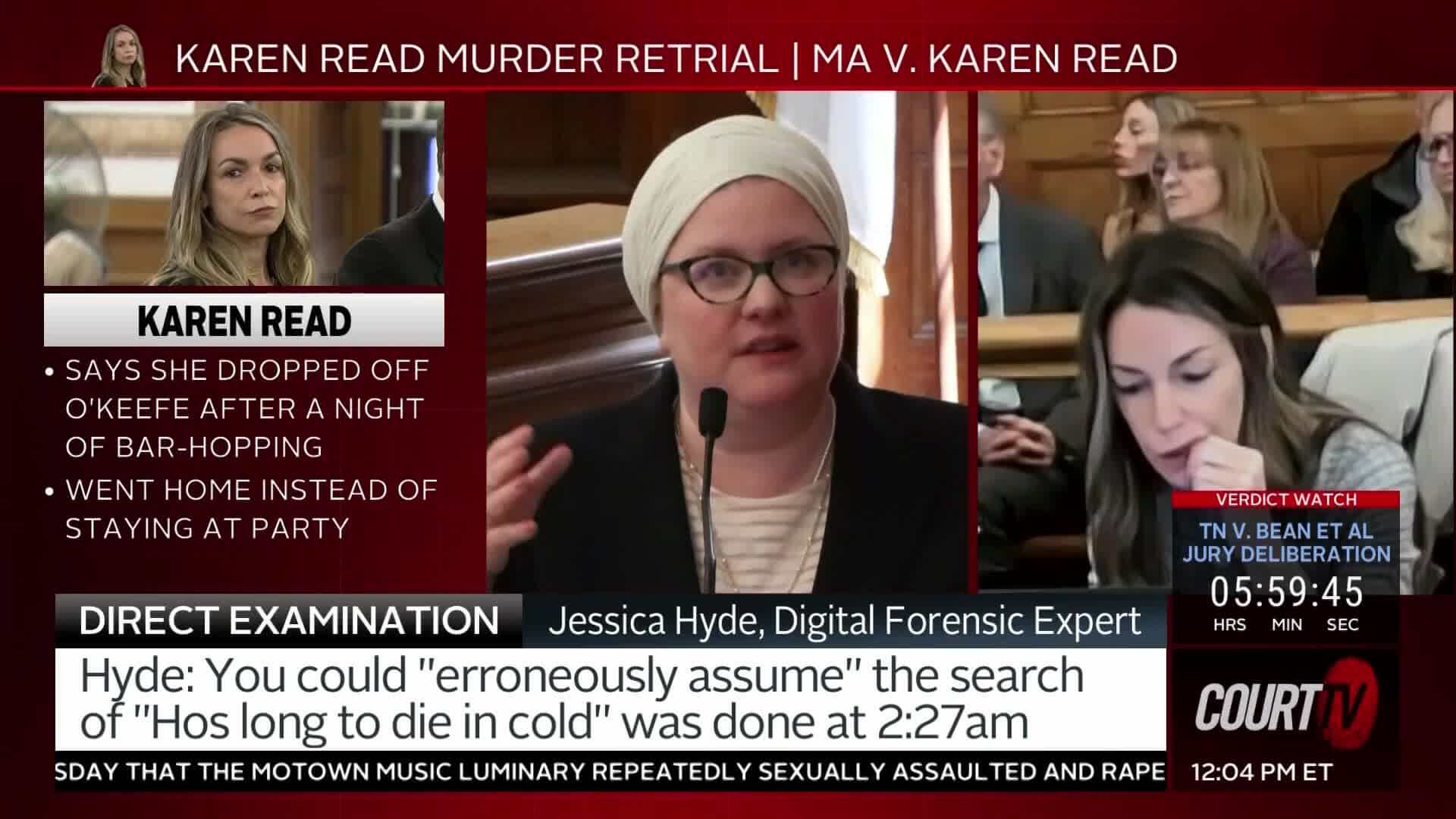
Expert: 2:27am ‘Hos Long…’ Timestamp Does No longer Mean Search Took effect Then
Private detective Digital Forensics Expert Jessica Hyde acknowledged 2:27am timestamp for Jen McCabe googling “Hos long to die in cold” doesn’t imply search definitively came about then attributable to a tab turn into opened at that time, and that tab turn into old fashioned for a pair of searches. (5/7/25…Be taught Extra

May
Hackers exploit OttoKit WordPress plugin flaw to have the ability to add admin accounts
Scam detection Hackers are exploiting a main unauthenticated privilege escalation vulnerability within the OttoKit WordPress plugin to murder rogue admin accounts on centered web sites. OttoKit (previously SureTriggers) is a WordPress automation and integration plugin utilized in over 100,000 web sites, permitting users to connect their web sites to Third-celebration providers and automate workflows. Patchstack […]

May
Samsung MagicINFO 9 Server RCE flaw now exploited in assaults
Cyber investigation Hackers are exploiting an unauthenticated far away code execution (RCE) vulnerability in the Samsung MagicINFO 9 Server to hijack devices and deploy malware. Samsung MagicINFO Server is a centralized recount material administration device (CMS) aged to remotely manage and withhold an eye on digital signage displays made by Samsung. It is aged by […]
Shahzaib Shah: The Pakistani Moral Hacker Shaping the Future of World Cyber Protection
Scam detection Balakot, Pakistan, Might seemingly just 06, 2025 –(PR.com)– A Rising Cybersecurity Visionary from Northern PakistanIn an international an increasing form of dependent on digital infrastructure, cybersecurity is never any longer non-compulsory — it’s important. And on the intersection of innovation, ethics, and resilience stands Syed Shahzaib Shah, a young cybersecurity researcher who has long […]

May
Shahzaib Shah: The Pakistani Moral Hacker Shaping the Diagram forward for World Cyber Protection
Private eye Balakot, Pakistan, Can even 06, 2025 –(PR.com)– A Rising Cybersecurity Visionary from Northern PakistanIn an world an increasing number of dependent on digital infrastructure, cybersecurity is now not now not mandatory — it’s essential. And at the intersection of innovation, ethics, and resilience stands Syed Shahzaib Shah, a young cybersecurity researcher who has long […]

May
From Bitcoin Scam to True-World Kidnapping: The $243M Crypto Heist and Its Lethal Aftermath
Internet investigation That it’s likely you’ll presumably be right here: Dwelling / Recordsdata / Crypto Scam / From Bitcoin Scam to True-World Kidnapping: The $243M Crypto Heist and Its Lethal Aftermath Teen Hackers Take 4,100 Bitcoin payment $243M The use of Social Engineering Potential Per week after pulling the heist, the hackers kidnapped Veer Chetal’s […]

May
Luna Moth extortion hackers pose as IT aid desks to breach US companies
Digital forensics The records-theft extortion team identified as Luna Moth, aka Quiet Ransom Neighborhood, has ramped up callback phishing campaigns in assaults on moral and financial institutions in the US. In line with EclecticIQ researcher Arda Büyükkaya, the final design of these assaults is records theft and extortion. Luna Moth, identified internally as Quiet Ransom […]
May
AI and Blockchain Explorers: Arkham and Blockchair Reshape Onchain Visibility
Internet investigation AI and Blockchain Explorers: Arkham and Blockchair Reshape Onchain Visibility â Crypto Info Bitcoin Info You should per chance also should enable JavaScript to flee this app. Read More

May
Crypto Scams Soar in Nebraska as Romance Ruses Drain Financial savings
Cybersecurity expert Crypto Scams Soar in Nebraska as Romance Ruses Drain Financial savings â Featured Bitcoin News You wish to enable JavaScript to bolt this app. Read More
Recent Posts
- Trump’s FBI says ‘Epstein’ penal advanced postcard to pedophile Larry Nassar is FAKE
- Epstein’s brother’s wild converse that Trump authorized his homicide is unearthed in DOJ files
- Informant steered FBI that Jeffrey Epstein had a ‘non-public hacker’
- Fireblocks CEO says North Korea-linked job recruitment scam centered LinkedIn profiles
- How Criminal Millions Sprinted Via Binance, OKX, and Thoroughly different High Crypto Exchanges
Recent Comments
Categories
Recent Posts



