-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Tag: hacker

Jul
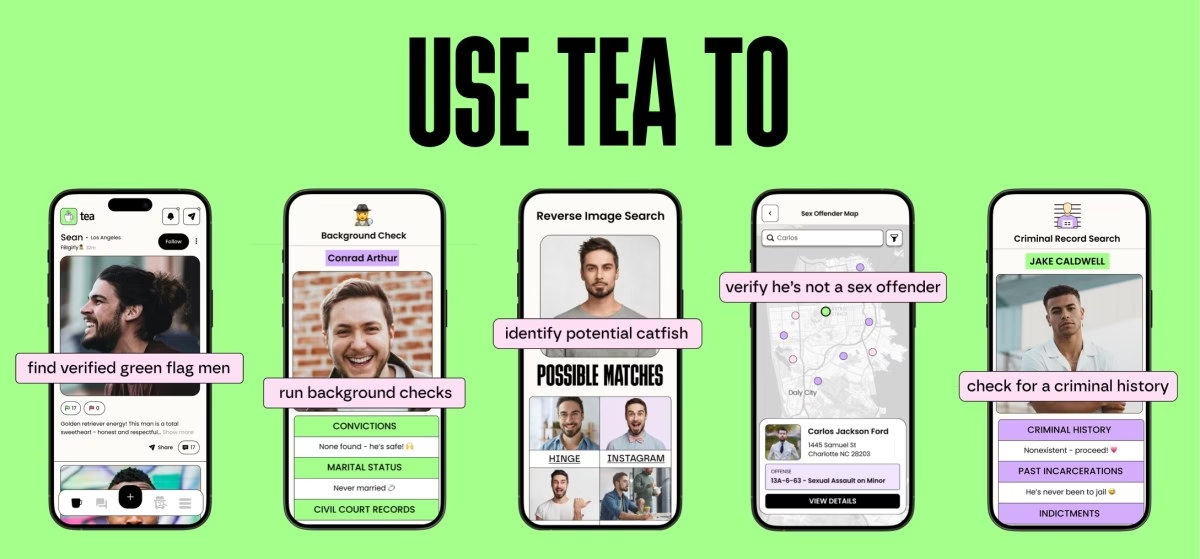
The Tea app used to be supposed to aid ladies date safely. Then hackers leaked 72,000 photos on-line, including users’ selfies
Cybercrime Tea, a interesting dating app designed to let ladies anonymously inquire of or warn every other about men they’d encountered, rocketed to the pause jam on the U.S. Apple App Retailer this week. On Friday, the firm within the back of the app confirmed it had been hacked: Hundreds of photos, including selfies, had been leaked on-line. […]
Jul
Relationship security app Tea breached, exposing 72,000 user photos
Cybercrime In Transient Posted: 9:40 AM PDT · July 26, 2025 Image Credits:Tea Tea, an app that enables ladies folk to put up nameless feedback about males they’ve supposedly dated, introduced Friday that it has suffered an recordsdata breach, with hackers having entry to 72,000 photos. That quantity entails 13,000 selfies and photo IDs submitted […]

Jul
Post SMTP plugin flaw exposes 200K WordPress web sites to hijacking assaults
Cybersecurity expert Bigger than 200,000 WordPress web sites are the utilization of a inclined version of the Post SMTP plugin that allows hackers to rob retain a watch on of the administrator narrative. Post SMTP is a popular email shipping plugin for WordPress that counts bigger than 400,000 energetic installations. It’s marketed as a replacement […]

Jul
Allianz Lifestyles says ‘majority’ of clients’ personal info stolen in cyberattack
Mobile forensics U.S. insurance protection wide Allianz Lifestyles has confirmed to TechCrunch that hackers stole the non-public info of the “majority” of its customers, monetary consultants, and employees all over a mid-July info breach. When reached by TechCrunch, Allianz Lifestyles spokesperson Brett Weinberg confirmed the breach. “On July 16, 2025, a malicious threat actor won […]

Jul
North Korean hackers ran US-essentially based “pc farm” from Arizona lady’s home
Private eye As the preference of computers mounted, Chapman started stacking them on shelves spherical her verbalize, labeling them with sticky notes so she might perchance well perchance have in mind which “worker” and company controlled which machine. When Chapman’s home became searched, FBI agents took photographs of her setup, which is… something to gape, […]

Jul
Microsoft reputedly confirms Chinese language hackers on the aid of SharePoint server attacks
Online fraud (Image credit rating: Getty Photos) Microsoft names three Chinese language hacking groups it claims were abusing fair currently stumbled on flaws in SharePoint Hackers were it looks in a disclose to fetch entry to gorgeous knowledge The corporate is confident the attacks will abet coming until the techniques are patched No longer now […]

Jul
CISA and FBI warn of escalating Interlock ransomware assaults
Cybersecurity expert CISA and the FBI warned on Tuesday of elevated Interlock ransomware exercise concentrating on companies and serious infrastructure organizations in double extortion assaults. On the present time’s advisory changed into as soon as jointly authored with the Division of Health and Human Companies (HHS) and the Multi-Advise Knowledge Sharing and Prognosis Heart (MS-ISAC) […]

Jul
SharePoint vulnerability with 9.8 severity ranking under exploit sooner or later of globe
Internet investigation Skip to articulate material Ongoing attacks are allowing hackers to clutch credentials giving privileged access. Authorities and researchers are sounding the alarm over the active mass exploitation of a excessive-severity vulnerability in Microsoft SharePoint Server that’s allowing attackers to fabricate off with sensitive company data, including authentication tokens historic to access programs inside […]

Jul
16 Billion Passwords Leaked — Can Bitwarden Preserve Yours Safe? I Examined It
Cyber investigation Key Takeaways: Password breaches are frequent: The most modern files leak uncovered 16 billion passwords. Hackers can employ these leaked credentials to derive correct of entry to your emails, monetary institution accounts, and other sensitive files. Hackers contain some ways to snatch your passwords: They rely on phishing scams, keyloggers, brute-force attacks, […]

Jul
CoinDCX Replace Hacked for $44 Million
Private detective By Philip Maina 2 days within the pastMon Jul 21 2025 10:47:21 Studying Time: 2 minutes Crypto exchange CoinDCX has confirmed shedding over $44 million in a hack Hackers compromised the exchange’s inner yarn shared with a companion exchange CoinDCX talked about that no particular person funds possess been misplaced Crypto exchange CoinDCX […]
Recent Posts
- US Fatherland Safety Investigates Whether Bovino Made Disparaging Comments About Jewish Faith
- Missing Lady Last Seen Stressful To Bag Out Family’s Car Is Found Ineffective in Yard Days Later
- Rhode Island Priests Abused A total bunch of Adolescents Over A protracted time, Document Finds – The Unusual York Conditions
- FBI seizes LeakBase cybercrime forum, files of 142,000 members
- The TikTokers Discovering out the Epstein Recordsdata So You Don’t Like To


