
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > ShinyHunters issue to be in the back of SSO-account facts theft assaults

Jan
ShinyHunters issue to be in the back of SSO-account facts theft assaults
Identity theft

The ShinyHunters extortion gang claims it is in the back of a wave of ongoing divulge phishing assaults focusing on single imprint-on (SSO) accounts at Okta, Microsoft, and Google, enabling threat actors to breach corporate SaaS platforms and clutch firm facts for extortion.
In these assaults, threat actors impersonate IT give a increase to and talk to employees, tricking them into coming into their credentials and multi-ingredient authentication (MFA) codes on phishing web sites that impersonate firm login portals.
Once compromised, the attackers create rep entry to to the sufferer’s SSO account, which will provide rep entry to to assorted connected enterprise capabilities and services.
SSO services from Okta, Microsoft Entra, and Google enable corporations to hyperlink third-event capabilities into a single authentication lope alongside with the circulation, giving employees rep entry to to cloud services, internal instruments, and industry platforms with a single login.
These SSO dashboards in general list all connected services, making a compromised account a gateway into corporate methods and facts.
Platforms steadily connected by SSO consist of Salesforce, Microsoft 365, Google Workspace, Dropbox, Adobe, SAP, Slack, Zendesk, Atlassian, and a total lot of others.

Source: Microsoft
Identity theft Vishing assaults historic for facts theft
As first reported by BleepingComputer, threat actors were accomplishing these assaults by calling employees and posing as IT crew, the spend of social engineering to persuade them to log into phishing pages and entire MFA challenges in true time.
After having rep entry to to a sufferer’s SSO account, the attackers browse the list of connected capabilities and originate harvesting facts from the platforms on hand to that particular person.
BleepingComputer is mindful of more than one corporations focused in these assaults that own since bought extortion requires signed by ShinyHunters, indicating that the crew turned into once in the back of the intrusions.
BleepingComputer contacted Okta earlier this week referring to the breaches, however the firm declined to observation on the solutions theft assaults.
Then all yet again, Okta launched a describe the day gone by describing the phishing kits historic in these divulge-based assaults, which match what BleepingComputer has been knowledgeable.
Essentially based on Okta, the phishing kits consist of a web-based control panel that enables attackers to dynamically change what a sufferer sees on a phishing site whereas talking to them on the phone. This enables threat actors to manual victims by each and each step of the login and MFA authentication process.
If the attackers enter stolen credentials into the true service and are brought on for MFA, they’ll picture unique dialog bins on the phishing site in true time to issue a sufferer to approve a push notification, enter a TOTP code, or make assorted authentication steps.
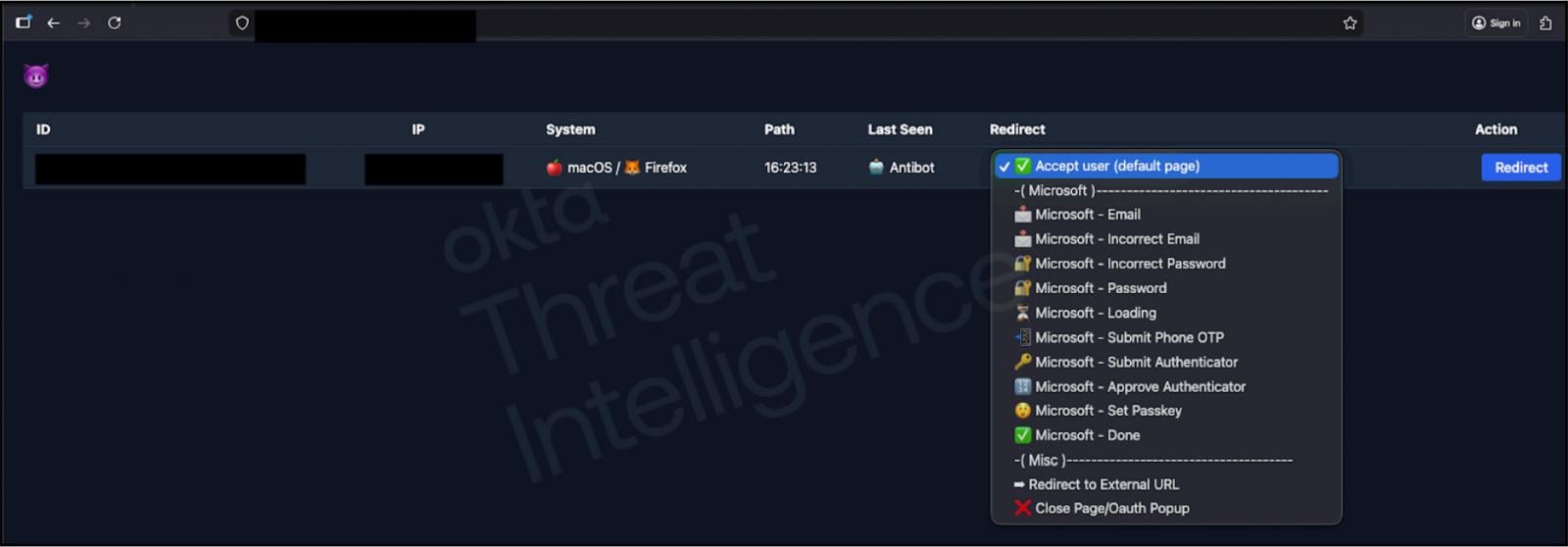
Source: Okta
ShinyHunters issue duty
Whereas ShinyHunters declined to observation on the assaults remaining night, the crew confirmed to BleepingComputer this morning that it is to blame for a couple of of the social engineering assaults.
“We confirm we are behind the attacks,” ShinyHunters knowledgeable BleepingComputer. “We are unable to share further details at this time, besides the fact that Salesforce remains our primary interest and target, the rest are benefactors.”
The crew furthermore confirmed assorted aspects of BleepingComputer’s reporting, alongside side exiguous print referring to the phishing infrastructure and domains historic in the campaign. Then all yet again, it disputed that a screenshot of a phishing kit issue-and-control server shared by Okta turned into once for its platform, claiming as an alternative that theirs turned into once constructed in-residence.
ShinyHunters claimed it is focusing on now now not finest Okta however furthermore Microsoft Entra and Google SSO platforms.
Microsoft talked about it has nothing to section at the moment, and Google talked about it had no evidence its merchandise were being abused in the campaign.
“At this time, we have no indication that Google itself or its products are affected by this campaign,” a Google spokesperson knowledgeable BleepingComputer.
ShinyHunters claims to be the spend of facts stolen in earlier breaches, such because the in style Salesforce facts theft assaults, to title and talk to employees. This facts comprises phone numbers, job titles, names, and diverse exiguous print historic to manufacture the social-engineering calls more convincing.
Closing night, the crew relaunched its Tor facts leak site, which for the time being lists breaches at SoundCloud, Betterment, and Crunchbase.
SoundCloud beforehand disclosed a facts breach in December 2025, whereas Betterment confirmed this month that its email platform had been abused to ship cryptocurrency scams and that facts turned into once stolen.
Crunchbase, which had now now not beforehand disclosed a breach, confirmed this day that facts turned into once stolen from its corporate network.
“Crunchbase detected a cybersecurity incident where a threat actor exfiltrated certain documents from our corporate network,” a firm spokesperson knowledgeable BleepingComputer. “No business operations have been disrupted by this incident. We have contained the incident and our systems are secure.”
“Upon detecting the incident we engaged cybersecurity experts and contacted federal law enforcement. We are reviewing the impacted information to determine if any notifications are required consistent with applicable legal requirements.”
Identity theft The 2026 CISO Budget Benchmark
It be funds season! Over 300 CISOs and safety leaders own shared how they’re planning, spending, and prioritizing for the 300 and sixty five days ahead. This describe compiles their insights, allowing readers to benchmark methods, title emerging traits, and evaluate their priorities as they head into 2026.
Learn the style prime leaders are turning investment into measurable influence.
Recent Posts
- Trump’s FBI says ‘Epstein’ penal advanced postcard to pedophile Larry Nassar is FAKE
- Epstein’s brother’s wild converse that Trump authorized his homicide is unearthed in DOJ files
- Informant steered FBI that Jeffrey Epstein had a ‘non-public hacker’
- Fireblocks CEO says North Korea-linked job recruitment scam centered LinkedIn profiles
- How Criminal Millions Sprinted Via Binance, OKX, and Thoroughly different High Crypto Exchanges
Recent Comments
Categories
Recent Posts





