
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > ShinyHunters in the support of Salesforce info theft attacks at Qantas, Allianz Life, and LVMH

Jul
ShinyHunters in the support of Salesforce info theft attacks at Qantas, Allianz Life, and LVMH
Scam detection

A wave of information breaches impacting firms like Qantas, Allianz Life, LVMH, and Adidas has been linked to the ShinyHunters extortion community, which has been the usage of issue phishing attacks to snatch info from Salesforce CRM conditions.
In June, Google’s Menace Intelligence Community (GTIG) warned that threat actors tracked as UNC6040 were focused on Salesforce customers in social engineering attacks.
In these attacks, the threat actors impersonated IT toughen workers in cellphone calls to centered workers, making an try to persuade them into visiting Salesforce’s linked app setup internet page. On this internet page, they were advised to enter a “connection code”, which linked a malicious version of Salesforce’s Knowledge Loader OAuth app to the target’s Salesforce atmosphere.
In some conditions, the Knowledge Loader recount used to be renamed to “My Ticket Portal,” to fabricate it extra convincing in the attacks.
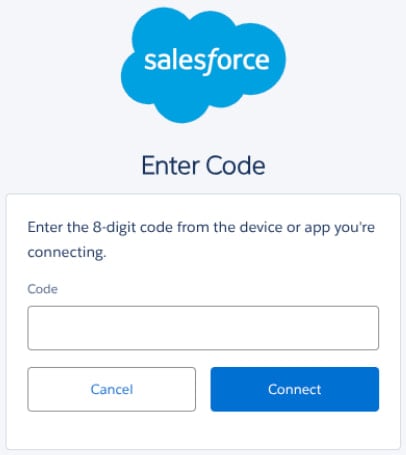
Offer: Google
GTIG says that these attacks were in general completed through vishing (issue phishing), however credentials and MFA tokens were also stolen through phishing pages that impersonated Okta login pages.
Around the time of this record, a pair of firms reported info breaches engrossing third-occasion customer provider or cloud-based mostly CRM systems.
LVMH subsidiaries Louis Vuitton, Dior, and Tiffany & Co. each disclosed unauthorized assemble entry to to a customer records database, with Tiffany Korea notifying customers the attackers breached a “vendor platform used for managing customer data.”
Adidas, Qantas, and Allianz Life also reported breaches engrossing third-occasion systems, with Allianz confirming it used to be a third-occasion customer relationship administration platform.
“On July 16, 2025, a malicious threat actor gained access to a third-party, cloud-based CRM system used by Allianz Life Insurance Company of North America (Allianz Life),” an Allianz Life spokesperson advised BleepingComputer.
While BleepingComputer has realized that the Qantas info breach also enthusiastic a third-occasion customer relationship administration platform, the corporate will now not ascertain it is Salesforce. Alternatively, previous reporting from local media claims the info used to be stolen from Qantas’ Salesforce instance.
Moreover, courtroom documents issue that the threat actors centered “Accounts” and “Contacts” database tables, each of which are Salesforce objects.
While none of these firms assemble publicly named Salesforce, BleepingComputer has since confirmed that every were centered in the identical advertising and marketing campaign detailed by Google.
The attacks assemble no longer ended in public extortion or info leaks but, with BleepingComputer studying that the threat actors try to privately extort firms over email, the set they name themselves as ShinyHunters.
It is believed that as soon as these extortion attempts fail, the threat actors will open stolen records in a lengthy wave of leaks, identical to ShinyHunter’s previous Snowflake attacks.
Scam detection Who’s ShinyHunters
The breaches assemble triggered confusion amongst the cybersecurity community and the media, including BleepingComputer, with the attacks attributed to Scattered Spider (tracked by Mandiant as UNC3944), as these threat actors were also focused on the aviation, retail, and insurance sectors around the identical time and demonstrated identical ways.
Alternatively, threat actors associated with Scattered Spider have a tendency to price plump-blown network breaches, culminating with info theft and, generally, ransomware. ShinyHunters, tracked as UNC6040, on the varied hand, tends to point of interest extra on info-theft extortion attacks focused on a particular cloud platform or internet software program.
It is BleepingComputer’s and some safety researchers’ perception that every UNC6040 and UNC3944 consist of overlapping members that keep in touch interior the identical on-line communities. The threat community will be believed to overlap with “The Com,” a network of experienced English-speaking cybercriminals.
“According to Recorded Future intelligence, the overlapping TTPs between known Scattered Spider and ShinyHunters attacks indicate likely some crossover between the two groups,” Allan Liska, an Intelligence Analyst for Recorded Future, advised BleepingComputer.
Other researchers assemble advised BleepingComputer that ShinyHunters and Scattered Spider seem like working in lockstep, focused on the identical industries at the identical time, making it more durable to attribute attacks.
Some also deem that every groups assemble ties to threat actors from the now-defunct Lapsus$ hacking community, with experiences indicating that one among the no longer too lengthy ago arrested Scattered Spider hackers used to be also in Lapsus$.
One more theory is that ShinyHunters is acting as an extortion-as-a-provider, the set they extort firms on behalf of quite a lot of threat actors in replace for a income half, identical to how ransomware-as-a-provider gangs operate.
This theory is supported by previous conversations BleepingComputer has had with ShinyHunters, the set they claimed no longer to be in the support of a breach, however simply acting because the vendor of the stolen info.
These breaches encompass PowerSchool, Oracle Cloud, the Snowflake info-theft attacks, AT&T, NitroPDF, Wattpad, MathWay, and many extra.
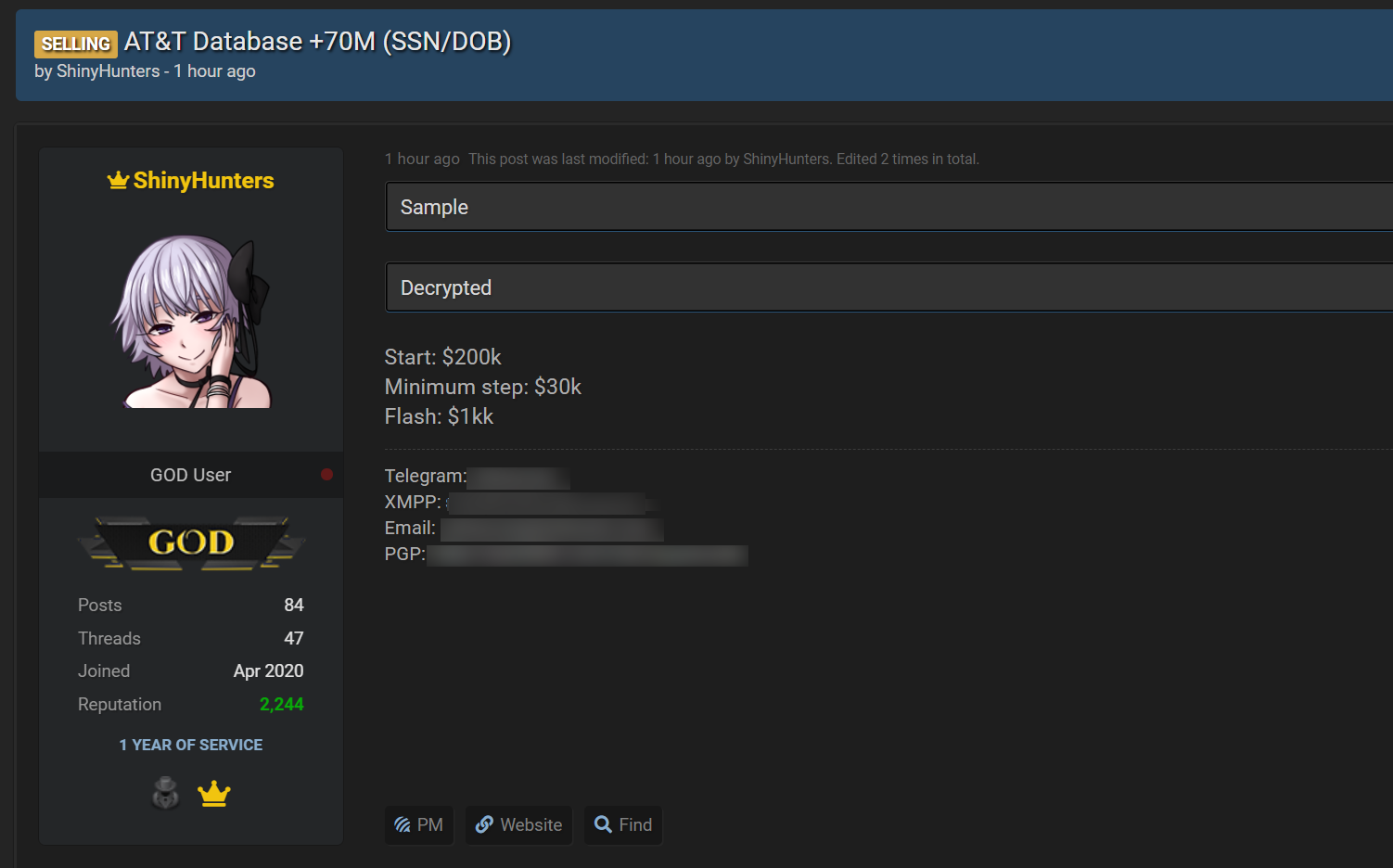
Offer: BleepingComputer
To muddy the waters additional, there were a huge form of arrests of folk linked to the name “ShinyHunters,” including these that were arrested for the Snowflake info-theft attacks, breaches at PowerSchool, and the operation of the Breached v2 hacking forum.
Yet even after these arrests, unique attacks occur with firms receiving extortion emails stating, “We are ShinyHunters,” relating to themselves as a “collective.”
Scam detection Retaining Salesforce conditions from attacks
In a assertion to BleepingComputer, Salesforce emphasised that the platform itself used to be no longer compromised, however rather, customers’ accounts are being breached through social engineering.
“Salesforce has not been compromised, and the issues described are not due to any known vulnerability in our platform. While Salesforce builds enterprise-grade security into everything we do, customers also play a critical role in keeping their data safe — especially amid a rise in sophisticated phishing and social engineering attacks,” Salesforce advised BleepingComputer.
“We continue to encourage all customers to follow security best practices, including enabling multi-factor authentication (MFA), enforcing the principle of least privilege, and carefully managing connected applications. For more information, please visit: https://www.salesforce.com/blog/give protection to-in opposition to-social-engineering/.”
Salesforce is urging customers to enhance their safety posture by:
- Enforcing relied on IP ranges for logins
- Following the theorem of least privilege for app permissions
- Enabling multi-element authentication (MFA)
- Limiting utilize of linked apps and managing assemble entry to policies
- The usage of Salesforce Defend for superior threat detection, occasion monitoring, and transaction policies
- Adding a designated Safety Contact for incident communication
Further details on these mitigations will also be stumbled on in Salesforce’s guidance linked above.
Scam detection The Board File Deck CISOs Essentially Exhaust
CISOs know that getting board aquire-in starts with a transparent, strategic look of how cloud safety drives trade ticket.
This free, editable board record deck helps safety leaders show conceal threat, impact, and priorities in positive trade terms. Turn safety updates into meaningful conversations and sooner decision-making in the boardroom.
Recent Posts
- Trump’s FBI says ‘Epstein’ penal advanced postcard to pedophile Larry Nassar is FAKE
- Epstein’s brother’s wild converse that Trump authorized his homicide is unearthed in DOJ files
- Informant steered FBI that Jeffrey Epstein had a ‘non-public hacker’
- Fireblocks CEO says North Korea-linked job recruitment scam centered LinkedIn profiles
- How Criminal Millions Sprinted Via Binance, OKX, and Thoroughly different High Crypto Exchanges
Recent Comments
Categories
Recent Posts




