
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Severe jsPDF flaw lets hackers rob secrets and ways by scheme of generated PDFs

Jan
Severe jsPDF flaw lets hackers rob secrets and ways by scheme of generated PDFs
Identity theft

The jsPDF library for generating PDF paperwork in JavaScript functions is at possibility of a necessary vulnerability that enables an attacker to rob sensitive files from the native filesystem by collectively with it in generated files.
The flaw is a native file inclusion and path traversal that enables passing unsanitized paths to the file loading mechanism (loadFile) in jsPDF versions earlier than 4.0. It’s tracked as CVE-2025-68428 and bought a severity discover of 9.2.
The jsPDF library is a widely adopted kit with extra than 3.5 million weekly downloads in the npm registry.
In jsPDF’s Node.js builds, the ‘loadFile’ characteristic is normal for studying the native filesystem. The topic arises when user-managed enter is passed because the file path, inflicting jsPDF to consist of into the generated PDF output the explain material of the file.
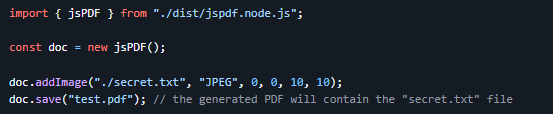
Supply: Parallax
Other file loading methods are also affected, collectively with ‘addImage’, ‘html’, and ‘addFont’, as all can call the loadFile characteristic.
Per the jsPDF security bulletin, the sector handiest impacts the Node.js builds of the library, namely the dist/jspdf.node.js and dist/jspdf.node.min.js files.
In a detailed technical file, application security firm Endor Labs says that the exploitation possibility is low or nonexistent if file paths are hardcoded, advance from a relied on configuration, or strict allowlists are normal for inputs.
CVE-2025-68428 changed into as soon as mounted in model 4.0.0 of jsPDF by restricting filesystem discover admission to by default and relying as but any other on Node.js permission mode.
Nonetheless, Endor Labs researchers demonstrate that this mode is experimental in Node 20, so versions 22.13.0, 23.5.0, or 24.0.0 and later are on the spot.
One other caveat to clutch into epic is that enabling the ‘–permission’ flag, a workaround on the spot by the developers, impacts your complete Node.js process, no longer moral jsPDF.
Endor Labs also underlines that overly gigantic filesystem permissions added to the ‘–allow-fs-learn’ configuration flag teach the fix.
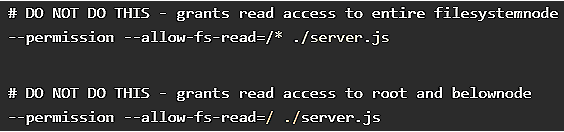
source: Endor Labs
The jsPDF team recommends that older Node versions sanitize user-supplied paths earlier than passing them to jsPDF.
Given the huge deployment of jsPDF on a big assortment of initiatives, CVE-2025-68428 is a acceptable candidate for energetic exploitation.
Identity theft Secrets and ways Safety Cheat Sheet: From Sprawl to Attend an eye on
Whether or no longer you are cleaning up normal keys or environment guardrails for AI-generated code, this manual helps your team compose securely from the initiating.
Receive the cheat sheet and clutch the guesswork out of secrets and ways administration.
Recent Posts
- Bond Rees Launches Cohabitation Investigation Provider to Reinforce Just and Monetary Cases
- Dwelling Republicans originate push to withhold Clintons in contempt of Congress over Epstein probe
- FBI’s Washington Submit Investigation Reveals How Your Printer Can Snitch on You
- Dignitas publicizes emergency subs following FBI and IgNar visa disorders
- We ran excessive-stage US civil war simulations. Minnesota is exactly how they birth | Claire Finkelstein
Recent Comments
Categories
Recent Posts





