
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > cybersecurity > Russian hackers bypass Gmail MFA the spend of stolen app passwords

Jun
Russian hackers bypass Gmail MFA the spend of stolen app passwords
Scam detection

Russian hackers bypass multi-ingredient authentication and accumulate admission to Gmail accounts by leveraging app-converse passwords in evolved social engineering assaults that impersonate U.S. Department of Declare officers.
The threat actor focused effectively-identified lecturers and critics of Russia in what’s described as a “refined and personalized glossy social engineering assault” that did no longer scuttle the persons of hobby into taking motion.
Between April and early June, the hackers delivered meticulously developed phishing messages geared against convincing recipients to raze and portion app-converse passwords that would provide accumulate admission to to their Gmail accounts.
An app-converse password is designed to allow third-occasion apps (e.g. an electronic mail client) that are realizing of as much less actual or older purposes permission to construct up admission to your Google Fable if two-ingredient authentication (2FA) is involving.
Security researchers at Google Possibility Intelligence Team notice the cyber actor as UNC6293. They assume they are utter-backed and may perhaps doubtless maybe very effectively be connected to APT29, a threat neighborhood beneath Russia’s Foreign Intelligence Provider (SVR).
APT29 is tracked beneath extra than one names (NobleBaron, Nobelium, Cozy Get, CozyDuke, Middle of the evening Blizzard) and has been working since a minimal of 2008.
Its targets include authorities networks, evaluate institutes, and direct tanks.
Plain-paced phishing
Academic evaluate neighborhood The Citizen Lab investigated an incident from UNC6293’s spearphishing campaign that focused Russian details operations educated Keir Giles.
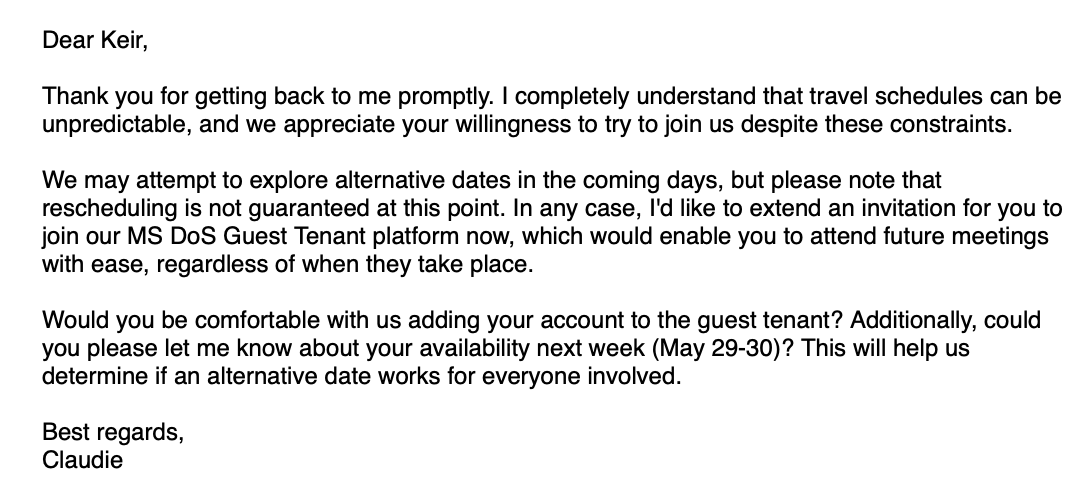
The assault starts with an electronic mail signed by Claudie S. Weber, allegedly from the U.S. Declare Department, though-provoking Giles to “a non-public online dialog.”
Though the message is delivered from a Gmail legend, extra than one @utter.gov electronic mail addresses are present in the carbon reproduction (CC) line, including one for Claudie S. Weber, making it extra credible that the communication became once official.
The researchers voice that they may perhaps maybe doubtless maybe no longer gather any proof of a “Claudie S. Weber” being employed by the U.S. Declare Department.
“We assume that the attacker is conscious that the Declare Department’s electronic mail server is it appears configured to accept all messages and does no longer emit a ‘leap’ response even when the take care of does no longer exist” – The Citizen Lab
After a entire lot of electronic mail exchanges where Giles expressed hobby nonetheless disclosed that they may perhaps maybe doubtless maybe no longer be on hand on the indicated day, the threat actor invited him to affix the Declare Department’s “MS DoS Visitor Tenant” platform, “which may perhaps doubtless doubtless lend a hand you to lend a hand future meetings with ease, regardless once they happen.”
provide: The Citizen Lab
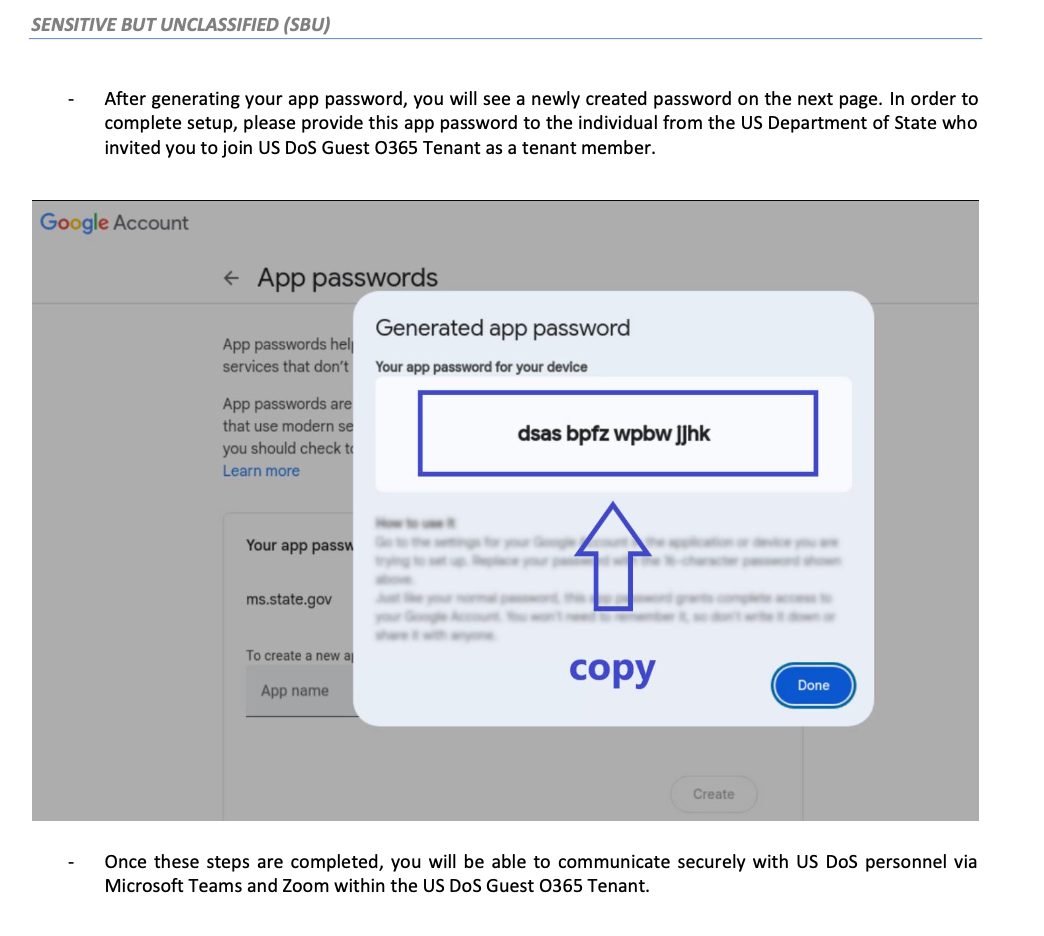
Giles authorized and became once sent a PDF file detailing raze an app-converse password on a Google legend, which became once main for enrolling on the alleged platform as a guest user.
A later step in the deceit exciting sharing the app-converse passcode “with US DoS directors in an effort to add the external user to the Visitor O365 Tenant.”
An clarification for this became once outlined in the instructions, announcing that it’s a long way an different resolution that facilitates actual communication over the platform between U.S. DoS workers and external customers with Gmail accounts.
While the aim believes that they’re constructing and sharing an app-converse password to construct up admission to a Declare Department platform in a actual manner, they are giving the attacker elephantine accumulate admission to to their Google legend, The Citizen Lab researchers insist.
provide: The Citizen Lab
Google Possibility Intelligence Team (GTIG) researchers sure that this spearphishing campaign started in a minimal of April and persevered thru the starting of June.
For the length of this era, they acknowledged two campaigns, one counting on themes connected to the U.S. Department of Declare and one other that historical lures connected to Ukraine and Microsoft.
Both campaigns included residential proxies (91.190.191[.]117) and digital inner most servers (VPS) servers in the infrastructure, allowing the threat actor to live anonymous when logging into compromised electronic mail accounts.
The two social engineering campaigns observed by The Citizen Lab and GTIG believe been skilfully crafted and relied on extra than one fraudulent identities, accounts, and pretty a pair of supplies designed in an effort to add to the deception.
Users focused with evolved phishing tactics are usually folks closely fascinated with high-profile concerns connected to conflicts, litigation, or advocacy.
To preserve them actual from educated attackers, Google recommends enrolling into its Developed Safety Program, which elevates security features on the legend and does no longer allow constructing an app-converse password, or log in with out offering a obvious passkey.
Scam detection Why IT teams are ditching manual patch administration
Patching historical to mean advanced scripts, long hours, and unending fire drills. Not anymore.
On this glossy e-book, Tines breaks down how as much as date IT orgs are leveling up with automation. Patch quicker, minimize overhead, and take care of strategic work — no advanced scripts required.
Tags
- cybercrime cybercrimephishing-attack cybersecurity email-fraud forensics|digital-forensics hacker hackers Investigation malware online-scam private-detective scam|fraud private-eye cyber|cybersecurity private-eye phishing|phishing-attack private-investigator private-investigator hacking|hacker Russian
Recent Posts
- Broker who supplied malware to the FBI space for sentencing
- High college senior going through extra than 300 prison fees in alleged sextortion map focusing on minors: reports
- 12 Delivery air Energy Tools You Can also objective accrued Appreciate In Your Garage Sooner than Spring Will get Right here
- How the FBI tracked down a Maryland man allegedly in the support of a secret-filming YouTube channel
- Hackers Raise The Fear About Discord’s Most recent Age-Verification Accomplice



