
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > cybersecurity > Microsoft: Russian hackers utilize ISP access to hack embassies in AiTM assaults

Jul
Microsoft: Russian hackers utilize ISP access to hack embassies in AiTM assaults
Cyber investigation

Microsoft warns that a cyber-espionage neighborhood linked to Russia’s Federal Safety Provider (FSB) is targeting diplomatic missions in Moscow the usage of local web provider services.
The hacking neighborhood tracked by Microsoft as Secret Blizzard (furthermore called Turla, Waterbug, and Venomous Bear) has been noticed exploiting its adversary-in-the-center (AiTM) dispute at the get provider provider (ISP) level to contaminate the systems of diplomatic missions with customized ApolloShadow malware.
To attain this, they redirect targets to captive portals, tricking them into downloading and executing a malware payload disguised as a Kaspersky antivirus update, which installs a relied on root certificate.
As soon as deployed, ApolloShadow helps trick compromised devices into recognizing malicious websites as legitimate, allowing threat actors to retain long-term access for intelligence gathering after infiltrating diplomatic systems.
“This is the first time Microsoft can confirm Secret Blizzard’s capability to conduct espionage at the ISP level, meaning diplomatic personnel using local internet providers and telecommunications in Russia are at high risk of being targets of Secret Blizzard’s AiTM position within those services,” Microsoft acknowledged.
“This campaign, which has been ongoing since at least 2024, poses a high risk to foreign embassies, diplomatic entities, and other sensitive organizations operating in Moscow, particularly to those entities who rely on local internet providers.”
Whereas Microsoft first detected the assaults in February 2025, the company believes this cyber-espionage marketing campaign has been piquant since at the least 2024.
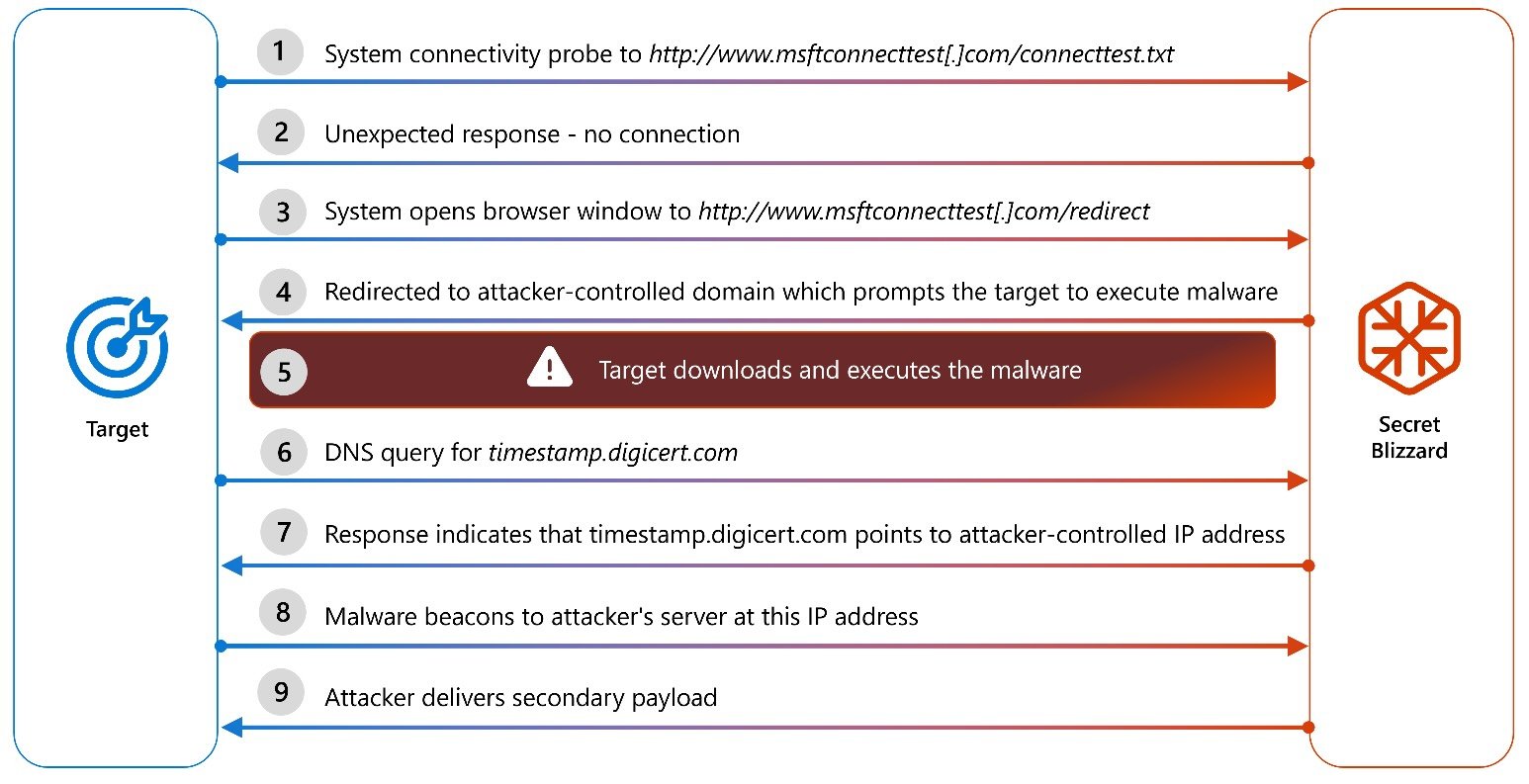
Secret Blizzard hackers are furthermore taking revenue of Russia’s domestic interception systems, including the Procedure for Operative Investigative Actions (SORM), to attain their clear-scale AiTM campaigns.
Cyber investigation Unorthodox cyberspies centered on high-profile targets
Turla has been orchestrating cyber-espionage and info theft campaigns targeting embassies, governments, and be taught facilities across over 100 international locations since at the least 1996.
Two years previously, CISA linked the neighborhood to Center 16 of Russia’s Federal Safety Provider (FSB) and a be taught-to-be taught (P2P) community of computers infected with Snake cyber-espionage malware that was as soon as later taken down in a joint ride gripping Five Eyes cybersecurity and intelligence companies.
These Russian dispute-backed hackers are furthermore the major suspects at the abet of assaults targeting the U.S. Central Expose, NASA, the Pentagon, a pair of Jap European Ministries of International Affairs, the Finnish International Ministry, and EU governments and embassies.
This threat neighborhood is acknowledged for its unconventional ways, including the defend an eye on of malware by comments on Britney Spears’ Instagram photos and the utilize of backdoor trojans with their have faith APIs.
Turla furthermore utilized the hijacked infrastructure and malware of the Iranian APT OilRig of their have faith campaigns to lie to and deceive defenders into attributing their assaults to Iranian dispute hackers.
Most just no longer too long previously, they’ve furthermore been spotted hijacking the infrastructure of Pakistani threat actor Storm-0156 to try Ukrainian navy devices linked by Starlink.
Recent Posts
- Bond Rees Launches Cohabitation Investigation Provider to Reinforce Just and Monetary Cases
- Dwelling Republicans originate push to withhold Clintons in contempt of Congress over Epstein probe
- FBI’s Washington Submit Investigation Reveals How Your Printer Can Snitch on You
- Dignitas publicizes emergency subs following FBI and IgNar visa disorders
- We ran excessive-stage US civil war simulations. Minnesota is exactly how they birth | Claire Finkelstein
Recent Comments
Categories
Recent Posts




