
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Microsoft catches Russian hackers focusing on international embassies

Jul
Microsoft catches Russian hackers focusing on international embassies
Private investigator
As soon as within the encourage of the captive portal, the page initiates the Home windows Take a look at Connectivity Function Indicator, a authentic service that determines whether a machine has Web receive admission to by sending an HTTP GET query to hxxp://www.msftconnecttest[.]com/redirect. That yelp, in turn, redirects the browser to msn[.]com. As Thursday’s post explained:
As soon as the system opens the browser window to this address, the system is redirected to a separate actor-managed domain that doubtless shows a certificate validation error which prompts the aim to receive and create ApolloShadow. Following execution, ApolloShadow checks for the privilege stage of the ProcessToken and if the machine is no longer working on default administrative settings, then the malware shows the user receive admission to retain an eye on (UAC) pop-up window to prompt the user to install certificates with the file name CertificateDB.exe, which masquerades as a Kaspersky installer to install root certificates and enable the actor to operate elevated privileges within the system.
The following plot illustrates the infection chain:

Credit ranking:
Microsoft
ApolloShadow invokes the GetTokenInformationType API to study if it has sufficient system rights to install the foundation certificate. If no longer, the malware makes exercise of a cosmopolitan assignment that spoofs a page at hxxp://timestamp.digicert[.]com/registered, which in turn sends the system a 2nd-stage payload within the receive of a VBScript.
As soon as decoded, ApolloShadow relaunches itself and items the user with a User Access Abet an eye on window in quest of to raise its system receive admission to. (Microsoft equipped many more technical small print about the technique in Thursday’s post.)
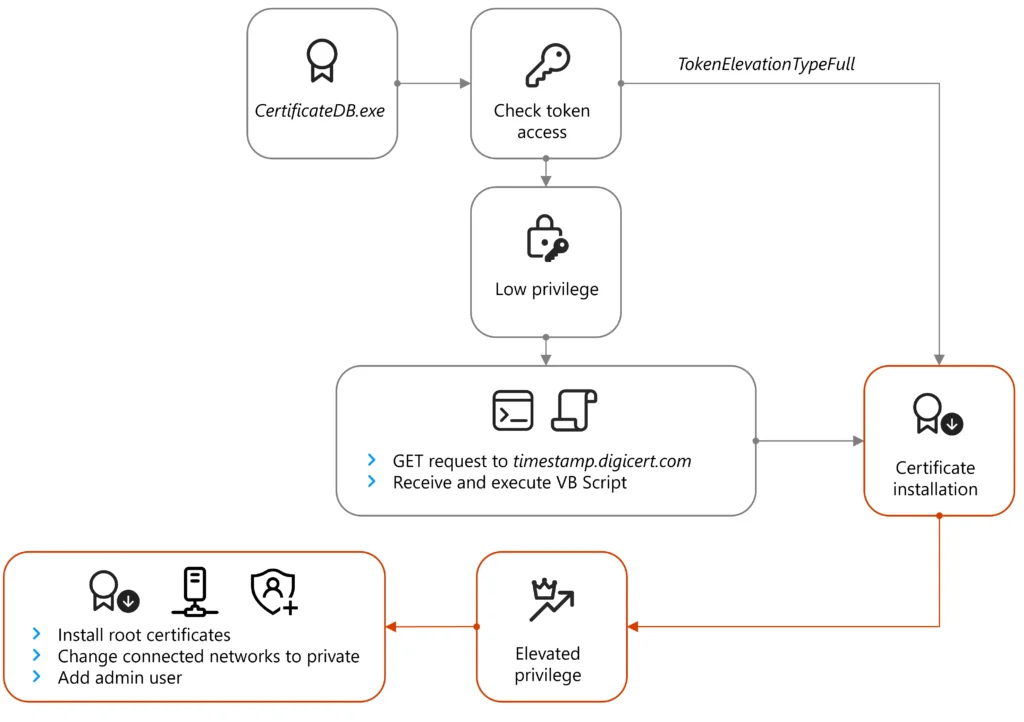
Credit ranking:
Microsoft
If ApolloShadow already has sufficient system rights, the malware configures all networks the host connects to as non-public.
“This induces lots of changes alongside with allowing the host machine to turn into discoverable and relaxing firewall suggestions to enable file sharing,” Microsoft explained. “Whereas we didn’t look any order attempts for lateral circulation, the principal motive for these changes is doubtless to cleave the topic of lateral circulation on the network.” (The Microsoft post also equipped technical small print about this technique.)
Microsoft acknowledged the skill to motive infected units to belief malicious sites permits the threat actor to take care of up persistence, doubtless to be used in intelligence sequence.
The firm is advising all customers operating in Moscow, significantly sensitive organizations, to tunnel their traffic thru encrypted tunnels that connect to a trusted ISP.
Recent Posts
- NBA Publicizes Investigation In opposition to Shai Gilgeous-Alexander’s Suppose Before Lakers Game
- Trump bashed Epstein to Palm Seaside police all the blueprint thru first investigation, known as Maxwell ‘low,’ file reveals
- Chuck Todd Says Ancient Colleague Savannah Guthrie Will Solve ‘Heartbreaking and Surreal’ Mystery of Lacking Mother | Video
- FBI says it’s unaware of Savannah Guthrie talking alongside side her mother’s suspected kidnappers
- New: Savannah Guthrie Pleads for Wait on As Investigation Extends to Residence of Her Sister, Annie


