
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Interlock ransomware adopts FileFix manner to raise malware

Jul
Interlock ransomware adopts FileFix manner to raise malware
Private investigator

Hackers hang adopted the unique design called ‘FileFix’ in Interlock ransomware attacks to topple a far away gather entry to trojan (RAT) on focused systems.
Interlock ransomware operations hang elevated all by means of the final months because the threat actor started the spend of the KongTuke web injector (aka ‘LandUpdate808’) to raise payloads by means of compromised web sites.
This shift in modus operandi became seen by researchers at The DFIR Document and Proofpoint since Can also fair. Reduction then, guests of compromised sites had been brought about to pass a counterfeit CAPTCHA + verification, and then paste into a Bolt dialog issue material robotically saved to the clipboard, a tactic per ClickFix attacks.
The trick led users to compose a PowerShell script that fetched and launched a Node.js-essentially based completely variant of the Interlock RAT.
In June, researchers chanced on a PHP-essentially based completely variant of Interlock RAT historical in the wild, which became delivered the spend of the identical KongTuke injector.
Earlier this month, a first-rate commerce in the provision wrapper took place, with Interlock now switching to the FileFix variation of the ClickFix manner because the most fashioned offer manner.
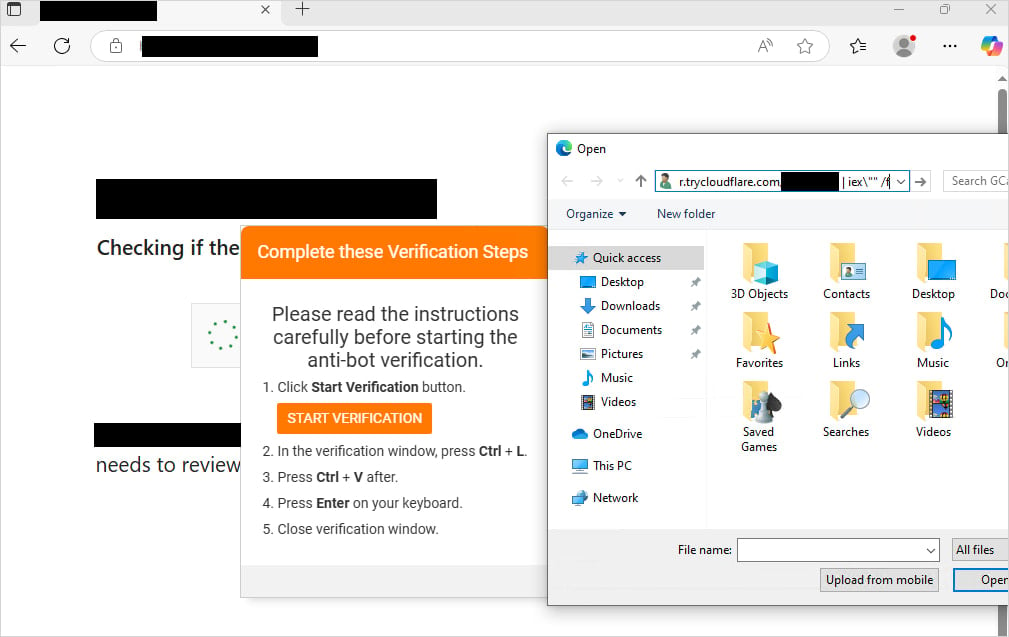
Source: The DFIR Document
FileFix is a social engineering assault design developed by security researcher mr.d0x. Or no longer it’s an evolution of the ClickFix assault, which turned certainly among the crucial broadly employed payload distribution techniques all by means of the final year.
Within the FileFix variation, the attacker weaponizes trusted Home windows UI ingredients, corresponding to File Explorer and HTML Applications (.HTA), to trick users into executing malicious PowerShell or JavaScript code with out displaying any security warnings.
Users are brought about to “open a file” by pasting a copied string into File Explorer’s take care of bar. The string is a PowerShell expose disguised to stare like a file path the spend of comment syntax.
Within the unique Interlock attacks, targets are requested to paste a expose disguised with a counterfeit file path onto File Explorer, leading to the downloading of the PHP RAT from ‘trycloudflare.com’ and its execution on the machine.
Post-an infection, the RAT executes a sequence of PowerShell commands to acquire machine and community records and exfiltrates this records as structured JSON to the attacker.
The DFIR Document additionally mentions proof of interactive activity, together with Exciting Itemizing enumeration, checking for backups, navigating native directories, and inspecting enviornment controllers.
The expose and inspire a watch on (C2) server can send shell commands for the RAT to compose, introduce unique payloads, add persistence by a Registry flee key, or pass laterally by far away desktop (RDP).
Interlock ransomware launched in September 2024, claiming essential victims like the Texas Tech College, DaVita, and Kettering Neatly being.
The ransomware operation leveraged ClickFix to contaminate targets, however its pivoting to FileFix indicates that the attacker is like a flash to adapt to stealthier assault techniques.
That is the first public affirmation of FileFix being historical in genuine cyberattacks. It’s doubtless to acquire more reputation as threat actors explore techniques to encompass it into their assault chains.
Private investigator 8 Total Threats in 2025
While cloud attacks could be rising more sophisticated, attackers collected prevail with surprisingly simple ways.
Drawing from Wiz’s detections all by means of thousands of organizations, this document unearths 8 key ways historical by cloud-fluent threat actors.
Recent Posts
- Broker who supplied malware to the FBI space for sentencing
- How ex-Prince Andrew dragged the Queen, Charles, William — and even Harry — into his dark shadows
- Original Documents Present a Controversial Vaccine Glimpse’s Distinctive Path to CDC Approval
- Angry Trump indicators global 10% responsibility after supreme courtroom points tariff blow
- Officials examine deadly California avalanche for doubtless prison negligence



