-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Hackers now attempting out ClickFix assaults against Linux targets

May
Hackers now attempting out ClickFix assaults against Linux targets
Scam detection

A brand contemporary advertising and marketing campaign the usage of ClickFix assaults has been spotted concentrating on each and each Windows and Linux programs the usage of instructions that make infections on either working device possible.
ClickFix is a social engineering tactic the effect faux verification programs or application errors are frail to trick web space guests into working console instructions that set up malware.
These assaults bask in traditionally targeted Windows programs, prompting targets to withhold out PowerShell scripts from the Windows Escape picture, main to data-stealer malware infections and even ransomware.
Nonetheless, a 2024 advertising and marketing campaign the usage of bogus Google Meet errors also targeted macOS customers.
Scam detection ClickFix concentrating on Linux customers
A more most contemporary advertising and marketing campaign spotted by Hunt.io researchers closing week is without doubt one of many many first to adapt this social engineering technique for Linux programs.
The attack, which is attributed to the Pakistan-linked possibility neighborhood APT36 (aka “Transparent Tribe”), makes use of a web space that impersonates India’s Ministry of Defence with a link to an allegedly legitimate press release.
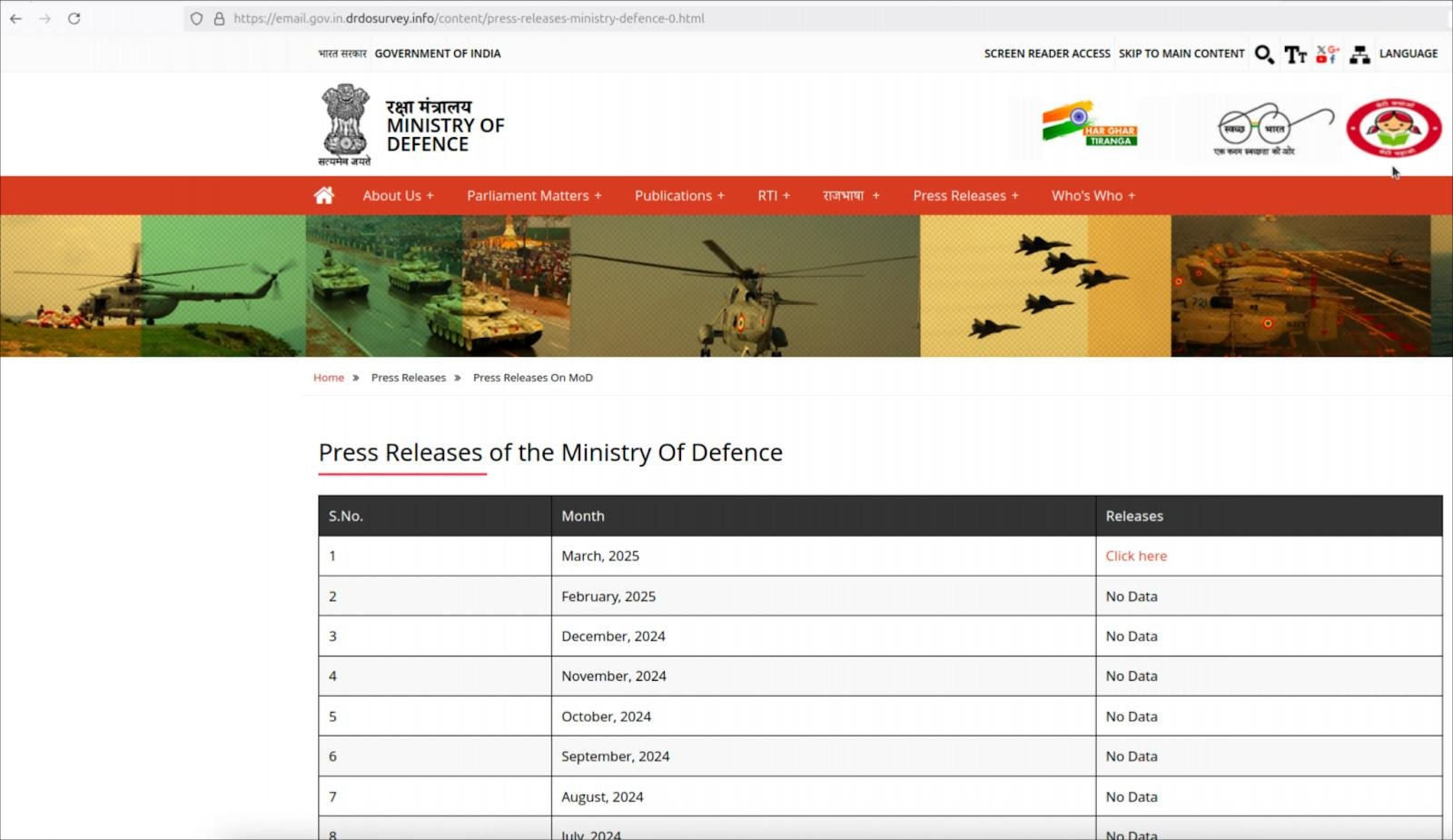
Source: Hunt.io
When guests click on this web space link, they’re profiled by the platform to search out out their working device, after which redirected to the very most life like attack circulation.
On Windows, victims are served a fat-conceal page warning them of restricted announce usage rights. Clicking on ‘Continue’ triggers JavaScript that copies a malicious MSHTA picture to the sufferer’s clipboard, who is recommended to paste and carry out it on the Windows terminal.
This launches a .NET-essentially essentially based loader which connects to the attacker’s take care of, while the client sees a decoy PDF file to make all the pieces appear official and as expected.
On Linux, victims are redirected to a CAPTCHA page that copies a shell picture to their clipboard when clicking the “I’m not a robot button.”
The sufferer is then guided to press ALT+F2 to originate a Linux plug dialog, paste the picture into it, after which press Enter to withhold out it.
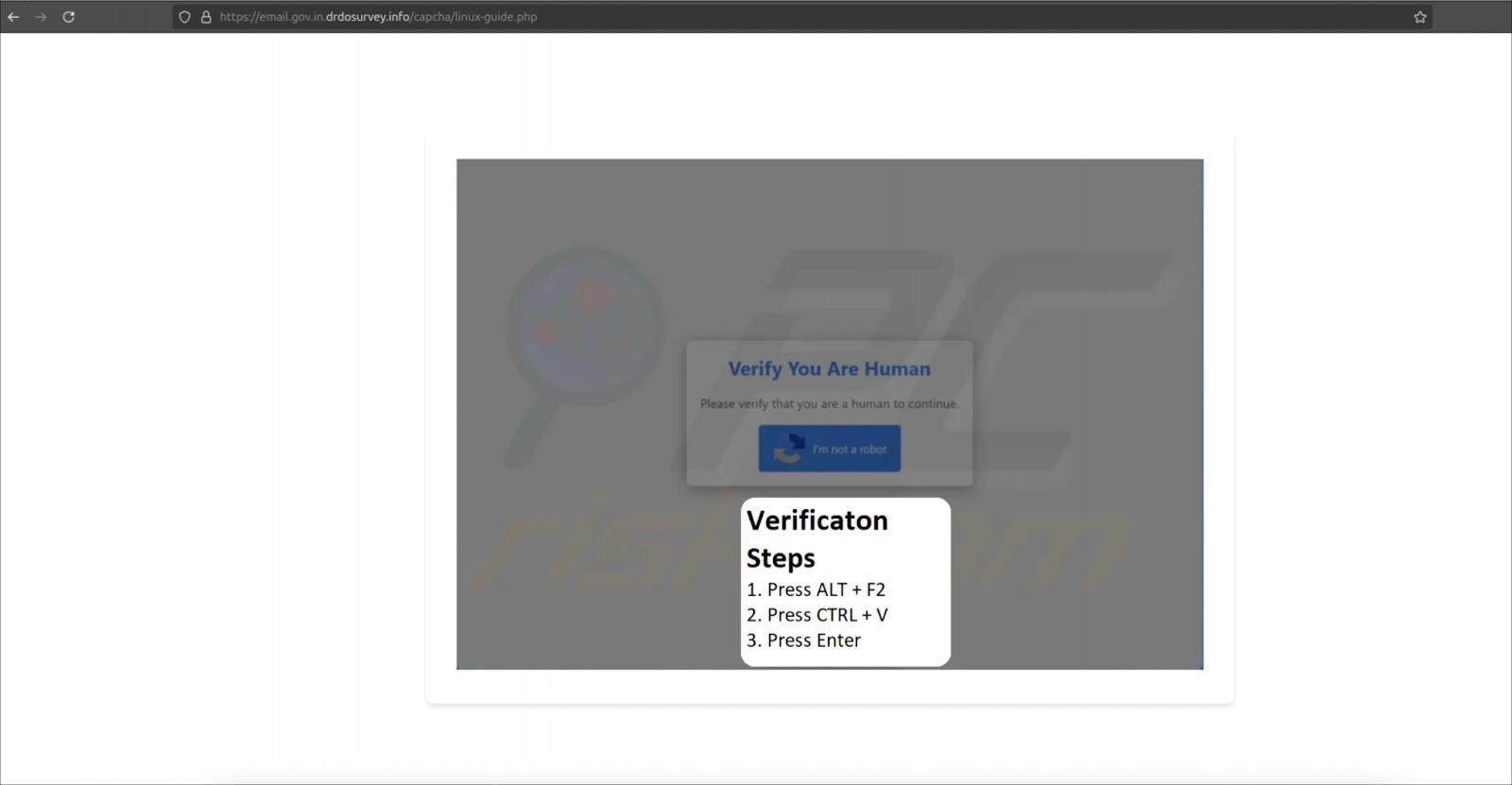
Source: Hunt.io
The picture drops the ‘mapeal.sh’ payload on the goal’s device, which, per Hunt.io, doesn’t beget any malicious actions in its most contemporary model, restricted to fetching a JPEG image from the attacker’s server.
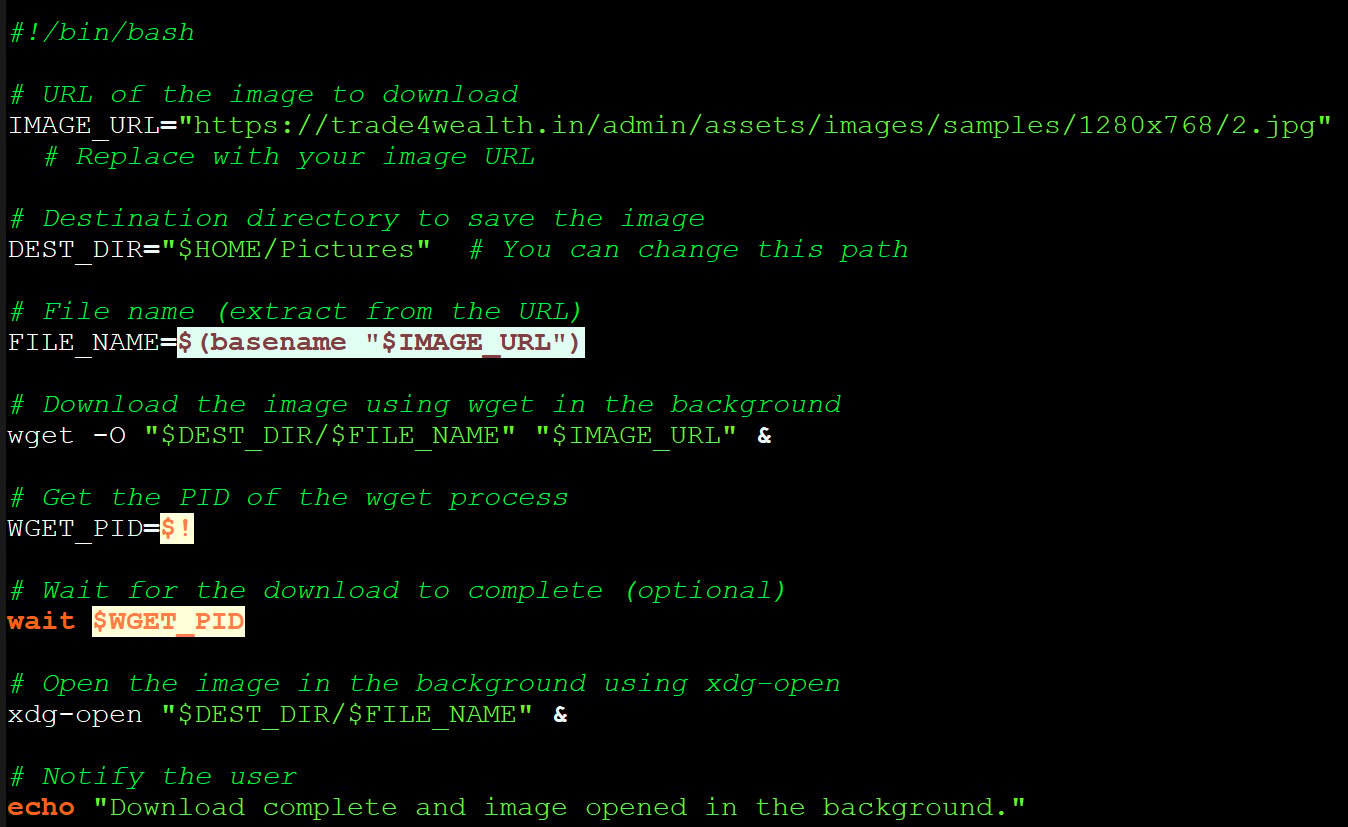
Source: BleepingComputer
“The script downloads a JPEG image from the same trade4wealth[.]in directory and opens it in the background,” explains Hunt.io.
“No additional activity, such as persistence mechanisms, lateral movement, or outbound communication, was observed during execution.”
Nonetheless, it is possible that APT36 is for the time being experimenting to search out out the effectiveness of the Linux an infection chain, as they would neutral correct must swap out the image for a shell script to set up malware or beget diversified malicious exercise.
The adaptation of ClickFix to execute assaults on Linux is one other testament to its effectiveness, because the attack form has now been frail against all three predominant desktop OS platforms.
As a customary protection, customers must always aloof no longer copy and paste any instructions into Escape dialogs without incandescent exactly what the picture does. Doing so very most life like increases the possibility of a malware an infection and theft of sensitive data.
Recent Posts
- Hong Kong small print investigations into online food complaints
- Republican Secretary of Inform Brad Raffensperger Names Jason Doss as Investigative Agent in First Liberty Fallout
- Exposed MongoDB cases soundless centered in records extortion assaults
- I invited hackers to attack my dwelling server, and the outcomes had been a warning sign
- I watched the Georgia 2020 divulge. Here’s what the FBI raid in Fulton County is de facto about.



