
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Hackers flip ScreenConnect into malware the utilization of Authenticode stuffing

Jun
Hackers flip ScreenConnect into malware the utilization of Authenticode stuffing
Cyber investigation

Threat actors are abusing the ConnectWise ScreenConnect installer to have signed a ways-off access malware by modifying hidden settings all the way thru the patron’s Authenticode signature.
ConnectWise ScreenConnect is a a ways-off monitoring and management (RMM) machine that enables IT admins and managed carrier companies (MSPs) to troubleshoot devices remotely.
When a ScreenConnect installer is built, it can possibly also be customized to incorporate the a ways-off server the patron ought to connect with, what text is shown in the dialog bins, and logos that ought to be displayed. This configuration info is saved all the way thru the file’s authenticode signature.
This technique, called authenticode stuffing, enables for the insertion of information into a certificate table whereas keeping the digital signature intact.
Cyber investigation ScreenConnect abused for preliminary access
Cybersecurity firm G DATA noticed malicious ConnectWise binaries with the same hash values across all file sections rather then for the certificate table.
The correct contrast was as soon as a modified certificate table containing novel malicious configuration knowledge whereas smooth permitting the file to stay signed.
G DATA says the first samples had been discovered in the BleepingComputer forums, the build contributors reported being contaminated after falling for phishing assaults. An identical assaults had been reported on Reddit.
These phishing assaults utilized either PDFs or intermediary Canva pages that linked to executables hosted on Cloudflare’s R2 servers (r2.dev).
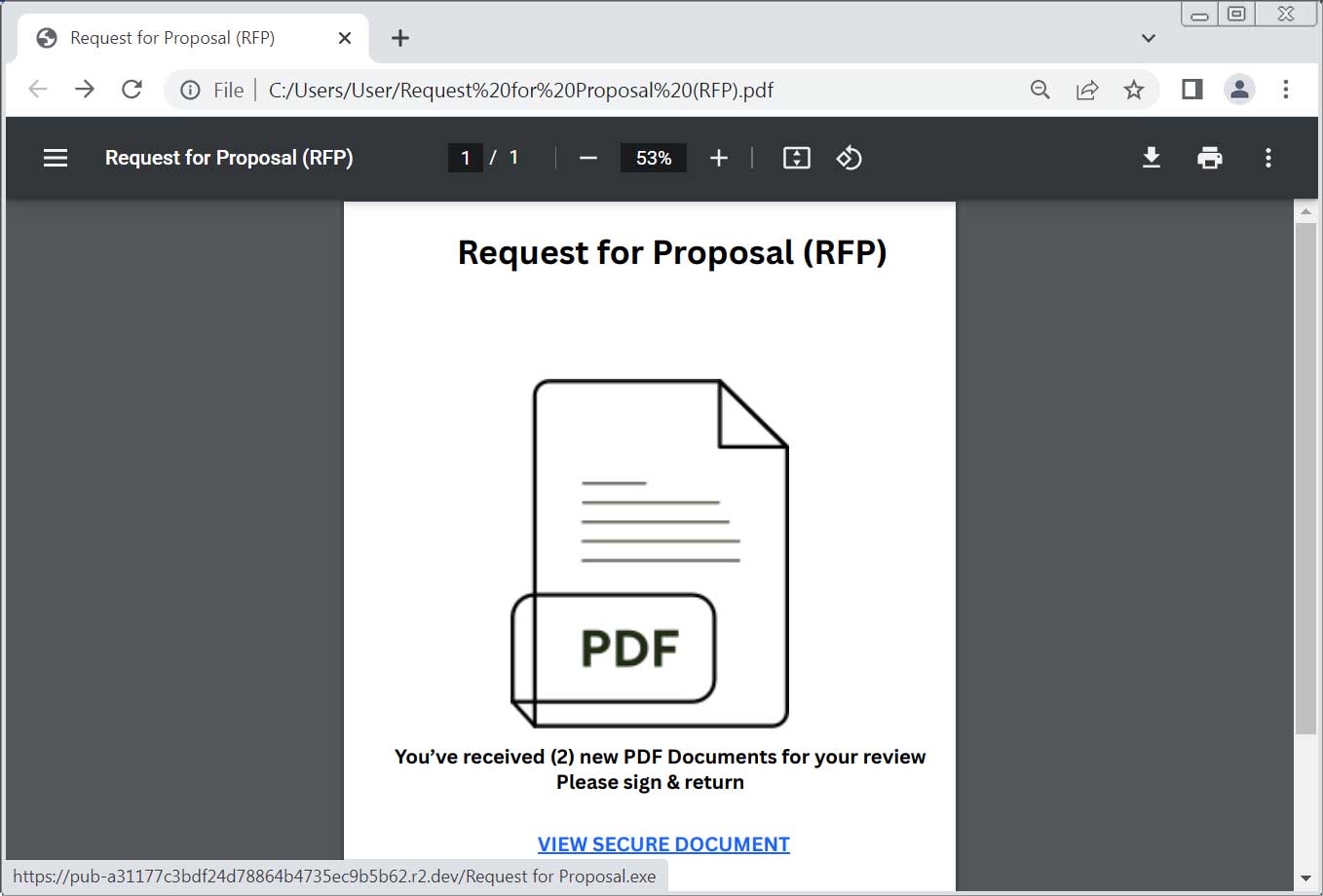
Source: BleepingComputer
The file, called “Request for Proposal.exe,” considered by BleepingComputer, is a malicious ScreenConnect client[
G DATA built a tool to extract and overview the settings discovered in these campaigns, the build the researchers discovered foremost changes, comparable to changing the installer’s title to “Windows Update” and changing the background with a wrong Windows Update image shown beneath.
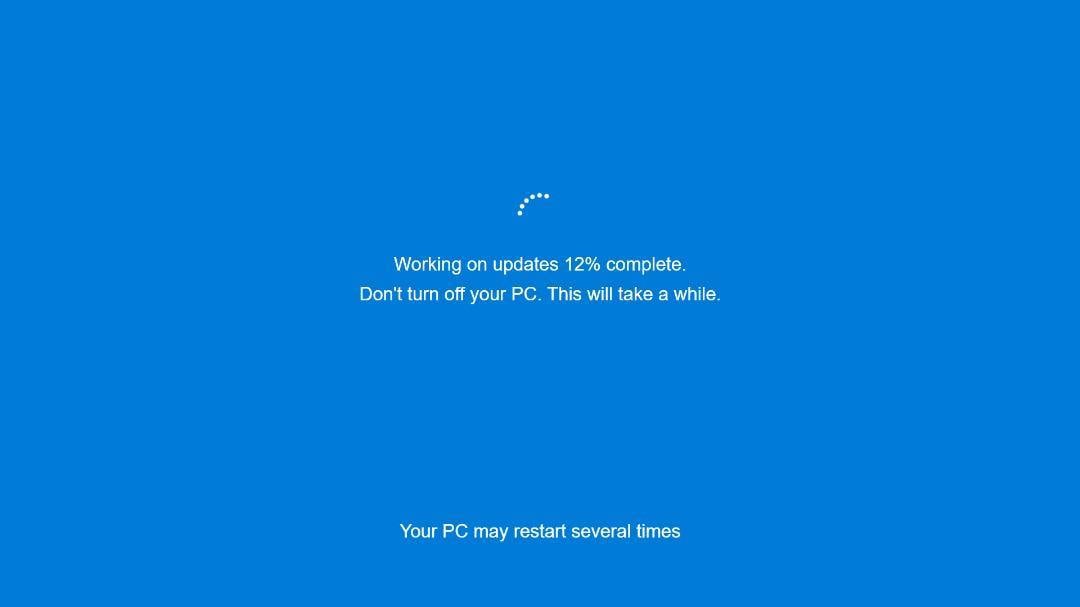
Source: G DATA
Truly, the threat actors converted the reliable ConnectWise ScreenConnect client into malware that enables them to stealthily effect access to contaminated devices.
After contacting G DATA, ConnectWise revoked the certificate worn in these binaries, and G DATA is now flagging these samples as Win32.Backdoor.EvilConwi.* and Win32.Riskware.SilentConwi.*.
G DATA says they by no formulation got a answer from ConnectWise about this marketing and marketing campaign and their file.
Any other marketing and marketing campaign shall be enterprise machine, this time distributing trojanized variations of the SonicWall NetExtender VPN client to steal usernames, passwords, and domain knowledge.
In response to an advisory from SonicWall, these modified variations ship captured credentials to an attacker-controlled server, making it foremost for customers ultimate to manufacture machine purchasers from first rate websites.
Cyber investigation Why IT teams are ditching handbook patch management
Patching worn to point out advanced scripts, lengthy hours, and never-ending fire drills. No longer anymore.
In this novel manual, Tines breaks down how up to the moment IT orgs are leveling up with automation. Patch faster, decrease overhead, and focal level on strategic work — no advanced scripts required.
Recent Posts
- Broker who supplied malware to the FBI space for sentencing
- High college senior going through extra than 300 prison fees in alleged sextortion map focusing on minors: reports
- 12 Delivery air Energy Tools You Can also objective accrued Appreciate In Your Garage Sooner than Spring Will get Right here
- How the FBI tracked down a Maryland man allegedly in the support of a secret-filming YouTube channel
- Hackers Raise The Fear About Discord’s Most recent Age-Verification Accomplice



