-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Hackers exploit severe telnetd auth bypass flaw to get root
Jan
Hackers exploit severe telnetd auth bypass flaw to get root
Scam detection
A coordinated marketing campaign has been noticed concentrated on a now now not too lengthy ago disclosed severe-severity vulnerability that has been fresh in the GNU InetUtils telnetd server for 11 years.
The protection subject is tracked as CVE-2026-24061 and become once reported on January 20. It is trivial to leverage and diverse exploit examples are publicly available.
Trojan horse persisted since 2015
Open-offer contributor Simon Josefsson explains that the telnetd aspect of GNU InetUtils suggestions a remote-authentication bypass vulnerability triggered by unsanitized environment variable facing when spawning ‘/usr/bin/login.’
The flaw occurs because telnetd passes the user-managed USER environment variable today to login(1) with out sanitization. By environment USER to -f root and connecting with the telnet -a expose, an attacker can skip authentication and end root get admission to.
The subject impacts GNU InetUtils variations 1.9.3 (released in 2015) thru 2.7, and become once patched in model 2.8. For of us that would per chance now now not toughen to the safe release, mitigation solutions encompass disabling the telnetd carrier or blocking off TCP port 23 on all firewalls.
GNU InetUtils is a series of classic network client and server instruments (telnet/telnetd, ftp/ftpd, rsh/rshd, ping, traceroute) maintained by the GNU Challenge, and extinct at some stage in diverse Linux distributions.
Even supposing Telnet is an panicked, legacy aspect largely replaced by SSH, many Linux and Unix methods quiet encompass it for compatibility or in actuality expert usage needs. It is particularly prevalent in the industrial sector thanks to its simplicity and low overhead.
On legacy and embedded devices, it goes to slither with out updates for more than a decade, explaining its presence in IoT devices, cameras, industrial sensors, and Operational Expertise (OT) networks.
Cristian Cornea of Zerotak, a penetration testing and cybersecurity products and companies company, told BleepingComputer that severe methods are refined to replace in OT/ICS environments.
The researcher talked about that here’s every occasionally not probably because upgrades are accompanied by reboot operations. “As a result, we still encounter systems running Telnet servers, and even if you tried to replace them with more secure protocols such as SSH, this is not feasible due to legacy systems that remain in operation.”
Extra technical users quiet rely on telnet for some initiatives:
One other user confirmed the spend of telnet “to connect to older Cisco devices that are way past “End of Life.” Same SSH issue.”
Nonetheless, devices uncovered on the public web that quiet enjoy telnet active are scarce, prompting many researchers to portray the CVE-2026-24061 vulnerability as much less severe.
Chance monitoring firm GreyNoise reports that it has detected accurate-world exploitation job leveraging CVE-2026-24061 against a limited series of weak endpoints.
The job, logged between January 21 and 22, originated from 18 fresh attacker IPs at some stage in 60 Telnet sessions, all deemed 100% malicious, sending 1,525 packets totaling 101.6 KB.
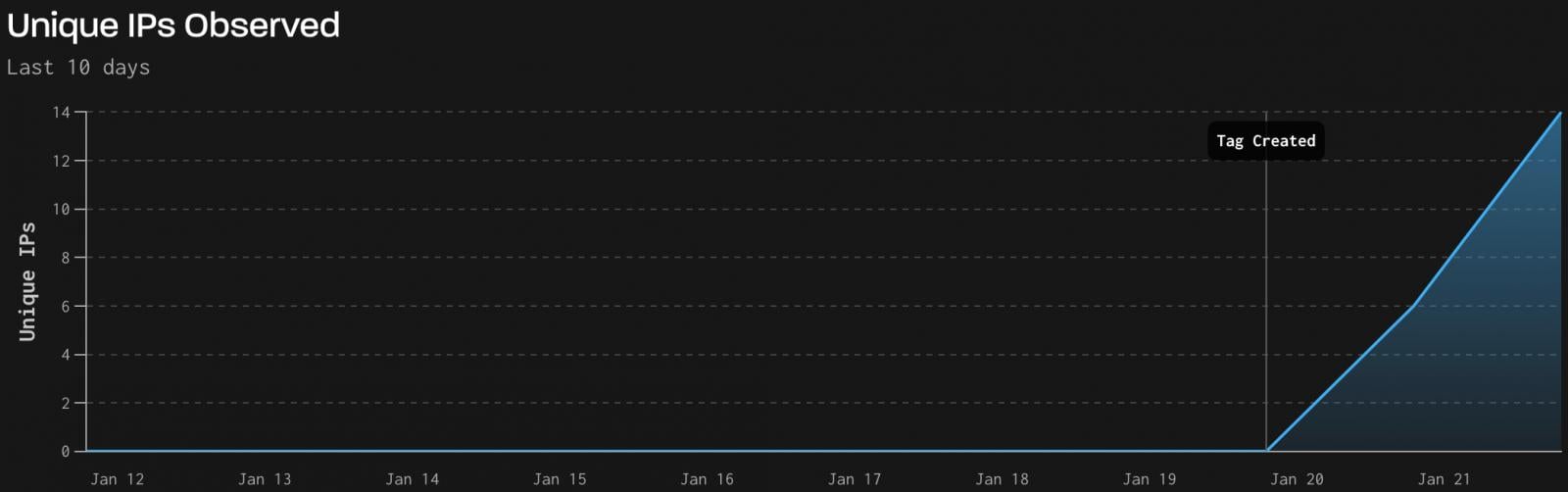
Offer: GreyNoise
The assaults abuse the Telnet IAC choice negotiation to inject ‘USER=-f
The assaults diverse in terminal slump, kind, and X11 DISPLAY values, however in 83.3% of the cases, they targeted the ‘root’ user.
Within the put up-exploitation phase, the attackers performed automated reconnaissance and attempted to persist SSH keys and deploy Python malware. GreyNoise reports that these attempts failed on the noticed methods as a result of missing binaries or directories.
Whereas the exploitation job appears to be like limited in scope and success, most definitely impacted methods need to quiet be patched or hardened as per the solutions earlier than the attackers optimize their attack chains.
Scam detection Secrets Security Cheat Sheet: From Sprawl to Withhold watch over
Whether or now now not you’re going to additionally very neatly be cleansing up ancient keys or environment guardrails for AI-generated code, this manual helps your crew assemble securely from the initiate.
Procure the cheat sheet and clutch the guesswork out of secrets management.
Recent Posts
- Trump’s FBI says ‘Epstein’ penal advanced postcard to pedophile Larry Nassar is FAKE
- Epstein’s brother’s wild converse that Trump authorized his homicide is unearthed in DOJ files
- Informant steered FBI that Jeffrey Epstein had a ‘non-public hacker’
- Fireblocks CEO says North Korea-linked job recruitment scam centered LinkedIn profiles
- How Criminal Millions Sprinted Via Binance, OKX, and Thoroughly different High Crypto Exchanges
Recent Comments
Categories
Recent Posts