
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > cybersecurity > Hackers build $1,078,750 for 28 zero-days at Pwn2Own Berlin

May
Hackers build $1,078,750 for 28 zero-days at Pwn2Own Berlin
Cybersecurity expert

The Pwn2Own Berlin 2025 hacking competition has concluded, with security researchers incomes $1,078,750 after exploiting 29 zero-day vulnerabilities and encountering some worm collisions.
At some level of the competition, they targeted mission technologies in the AI, net browser, virtualization, local privilege escalation, servers, mission applications, cloud-native/container, and car classes.
Per Pwn2Own’s principles, all targeted devices had all security updates installed and ran the most fresh working system variations.
Whereas Tesla additionally equipped two 2025 Tesla Model Y and 2024 Tesla Model 3 bench-high objects, security researchers who joined the competition haven’t registered any attempts on this class sooner than Pwn2Own started.
Competitors composed $260,000 in money awards after the principle day and but every other $435,000 on the 2nd day after exploiting 20 zero-day vulnerabilities. On the third day of Pwn2Own, they composed but every other $383,750 for eight more zero-days.
After these vulnerabilities are demoed all the strategy by method of Pwn2Own events, distributors grasp 90 days to release security updates sooner than TrendMicro’s Zero Day Initiative publicly discloses them.
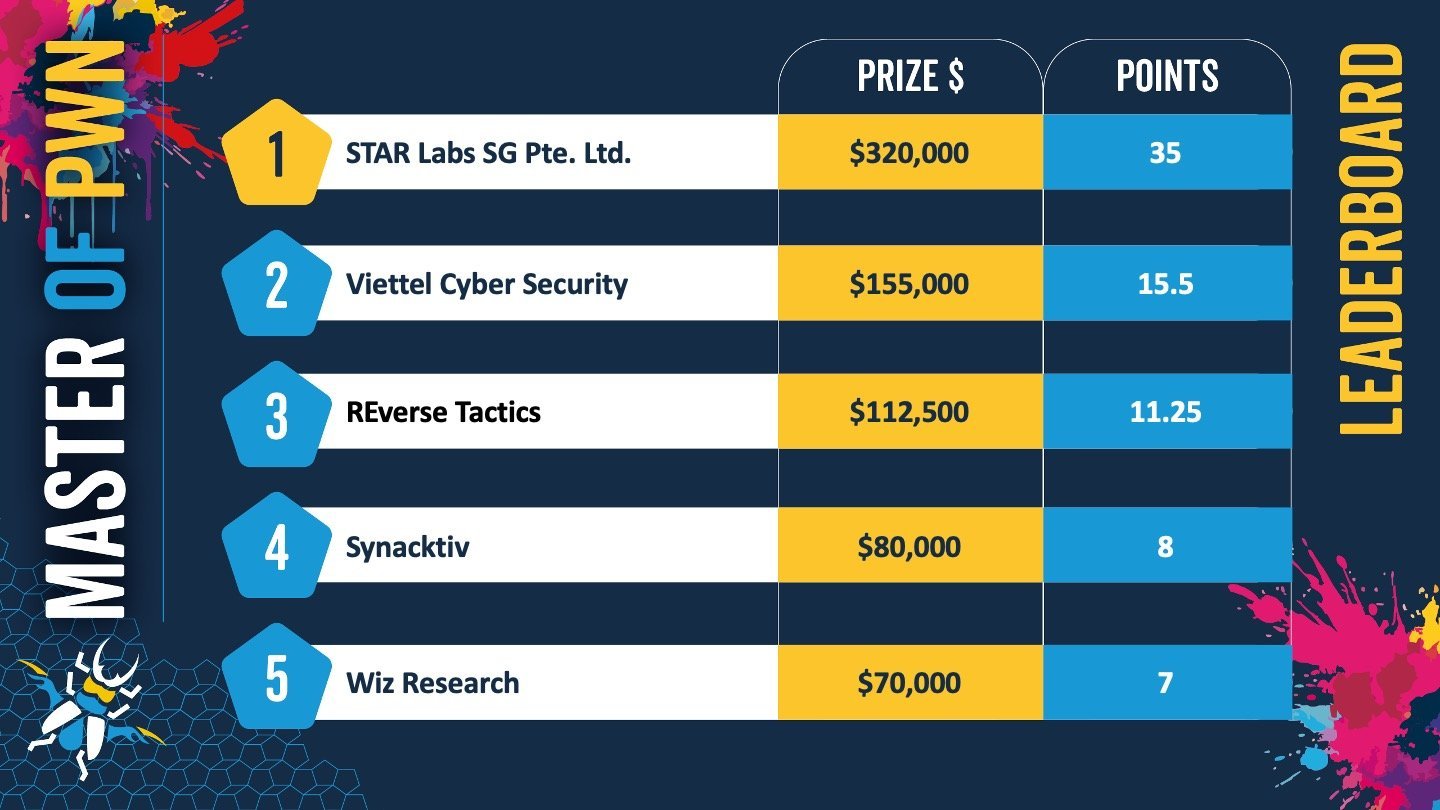
The STAR Labs SG team won this 365 days’s version of Pwn2Own Berlin with 35 Master of Pwn aspects and $320,000 earned all the strategy by method of the three-day contest after hacking Crimson Hat Challenge Linux, Docker Desktop, Windows 11, VMware ESXi, and Oracle VirtualBox.
STAR Labs’ Nguyen Hoang Thach won the competition’s highest reward of $150,000 after utilizing an integer overflow exploit to hack the VMware ESXi hypervisor instrument.
Crew Viettel Cyber Security took 2nd method after demonstrating zero-day flaws that may per chance maybe let attackers get away to the host system from Oracle VirtualBox guests and hack Microsoft SharePoint utilizing an exploit chain combining an auth bypass and an haunted deserialization.
On the third day, team Reverse Tactics all every other time hacked VMware’s hypervisor instrument utilizing an exploit chain abusing an integer overflow and an uninitialized variable worm to construct $112,500 and grab third method in the rankings.
Mozilla has already patched the two Firefox zero-day bugs (CVE-2025-4918 and CVE-2025-4919) demoed all the strategy by method of the competition after releasing Firefox 138.0.4, Firefox ESR 128.10.1, Firefox ESR 115.23.1, and a original Firefox for Android version over the weekend to take care of them.
In March 2024, Mozilla fastened two other zero-day vulnerabilities in the Firefox net browser (CVE-2024-29943 and CVE-2024-29944) after security researcher Manfred Paul exploited and reported them at Pwn2Own Vancouver 2024.
Tags
- cybercrime cybercrimefraud cybercrimehacker cybersecurity email-fraud forensics|digital-forensics hacker hackers Investigation malware malwarephishing-attack online-scam private-detective scam|fraud private-eye cyber|cybersecurity private-eye phishing|phishing-attack private-investigator private-investigator hacking|hacker zero-days
Recent Posts
- Trump’s FBI says ‘Epstein’ penal advanced postcard to pedophile Larry Nassar is FAKE
- Epstein’s brother’s wild converse that Trump authorized his homicide is unearthed in DOJ files
- Informant steered FBI that Jeffrey Epstein had a ‘non-public hacker’
- Fireblocks CEO says North Korea-linked job recruitment scam centered LinkedIn profiles
- How Criminal Millions Sprinted Via Binance, OKX, and Thoroughly different High Crypto Exchanges
Recent Comments
Categories
Recent Posts




