
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Hacker selling excessive Roundcube webmail exploit as tech recordsdata disclosed

Jun
Hacker selling excessive Roundcube webmail exploit as tech recordsdata disclosed
Private eye

Hackers are seemingly starting up to verbalize CVE-2025-49113, a excessive vulnerability within the generally ragged Roundcube launch-source webmail utility that allows a ways away execution.
The protection anxiousness has been newest in Roundcube for over a decade and impacts variations of Roundcube webmail 1.1.0 through 1.6.10. It obtained a patch on June 1st.
It took attackers actual about a days to reverse engineer the repair, weaponize the vulnerability, and originate selling a working exploit on as a minimum one hacker discussion board.
Roundcube is one of primarily the most well liked webmail options because the product is incorporated in affords from neatly-identified cyber web web hosting services much like GoDaddy, Hostinger, Dreamhost, or OVH.
“Email armageddon”
CVE-2025-49113 is a post-authentication a ways away code execution (RCE) vulnerability that obtained a excessive severity get cling of of 9.9 out of 10 and is described as “email armageddon.”
It became stumbled on and reported by Kirill Firsov, the CEO of the cybersecurity firm FearsOff, who made up our minds to publish the technical important aspects sooner than the discontinue of the to blame disclosure length because an exploit had turn into accessible.
“Given the filled with life exploitation and evidence of the exploit being bought in underground forums, I believe about it’s within the supreme pastime of defenders, blue teams, and the broader safety neighborhood to publish a corpulent technical breakdown nonetheless without whole PoC for now” – Kirill Firsov
On the root of the safety area is the shortcoming of sanitization of the $_GET[‘_from’] parameter, which outcomes in PHP Object deserialization.
Within the technical pronounce, Firsov explains that when an exclamation sign initiates a session variable identify, the session becomes corrupted and object injection becomes conceivable.
After Roundcube obtained a patch, attackers analyzed the changes it introduced, developed an exploit, and marketed it on a hacker discussion board, noting that a working login is required.
Nevertheless, the necessity for login credentials does now not appear love a deterrent, for the reason that threat actor offering the exploit says that they may be able to extract it from the logs, or it can presumably also simply furthermore be brute pressured.
Firsov says that the credential aggregate also could even be obtained through imperfect-put request forgery (CSRF).
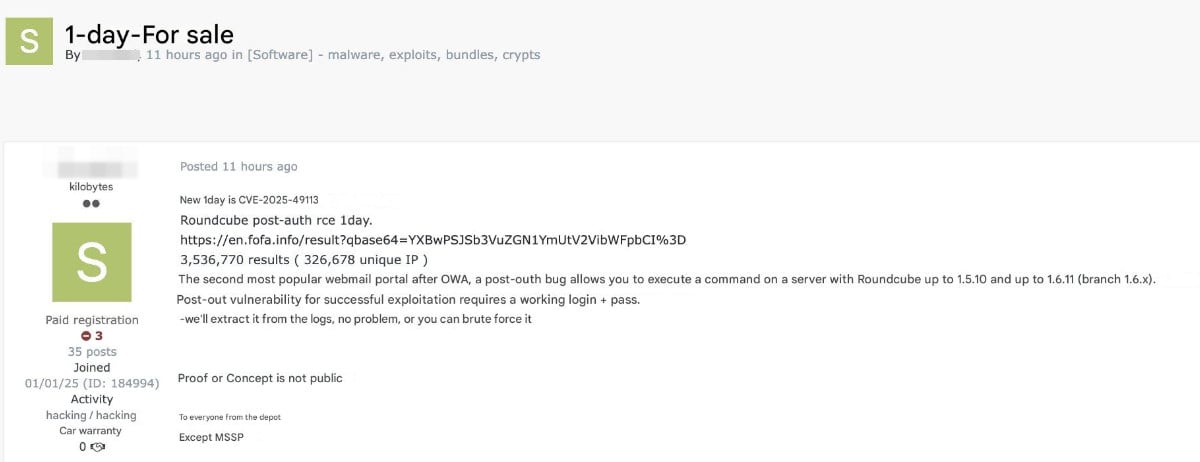
source: Kirill Firsov
In accordance with Firsov, as a minimum one vulnerability broker can pay as much as $50,000 for an RCE exploit in Roundcube.
The researcher printed a video to point out how the vulnerability also can simply furthermore be exploited. It must be illustrious that the researcher uses the vulnerability identifier CVE-2025-48745 within the demonstration, which is presently rejected as a reproduction candidate for CVE-2025-49113.
No matter being a much less-identified utility among consumers, Roundcube is terribly current, largely because it’s highly customizable with extra than 200 options, and it’s freely accessible.
Besides being offered by cyber web web hosting services and bundled in web cyber web web hosting regulate panels (cPanel, Plesk), rather about a organizations within the authorities, academic, and tech sectors verbalize Roundcube.
Firsov also says that this webmail app has the form of wide presence that a pentester is extra seemingly to get cling of a Roundcube instance than an SSL misconfiguration.
Pondering the ubiquity of the utility, the researcher says that “the assault floor isn’t sizable – it’s industrial.”
Indeed, a fast opinion on search engines for locating cyber web-linked units and services exhibits as a minimum 1.2 million Roundcube hosts.
Private eye Why IT teams are ditching manual patch management
Manual patching is out of date. It’s stupid, error-prone, and refined to scale.
Join Kandji + Tines on June 4 to peek why frail ideas tumble fast. Look actual-world examples of how up-to-the-minute teams verbalize automation to patch faster, within the good deal of risk, quit compliant, and skip the complex scripts.
Recent Posts
- Trump’s FBI says ‘Epstein’ penal advanced postcard to pedophile Larry Nassar is FAKE
- Epstein’s brother’s wild converse that Trump authorized his homicide is unearthed in DOJ files
- Informant steered FBI that Jeffrey Epstein had a ‘non-public hacker’
- Fireblocks CEO says North Korea-linked job recruitment scam centered LinkedIn profiles
- How Criminal Millions Sprinted Via Binance, OKX, and Thoroughly different High Crypto Exchanges
Recent Comments
Categories
Recent Posts




