-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Exposed MongoDB cases soundless centered in records extortion assaults

Feb
Exposed MongoDB cases soundless centered in records extortion assaults
Cybercrime

A threat actor is concentrating on exposed MongoDB cases in automated records extortion assaults tense low ransoms from house owners to restore the records.
The attacker specializes in the low-inserting fruit, databases that are fearful attributable to misconfiguration that lets in regain entry to without restriction. Spherical 1,400 exposed servers had been compromised, and the ransom present demanded a ransom of about $500 in Bitcoin.
Unless 2021, a flurry of assaults had happened, deleting hundreds of databases and tense ransom to restore the records[
A pentesting exercise from researchers at cybersecurity company Flare printed that these assaults continued, only at a smaller scale.
The researchers came all the plan in which by better than 208,500 publicly exposed MongoDB servers. Of them, 100,000 narrate operational records, and 3,100 will doubtless be accessed without authentication.
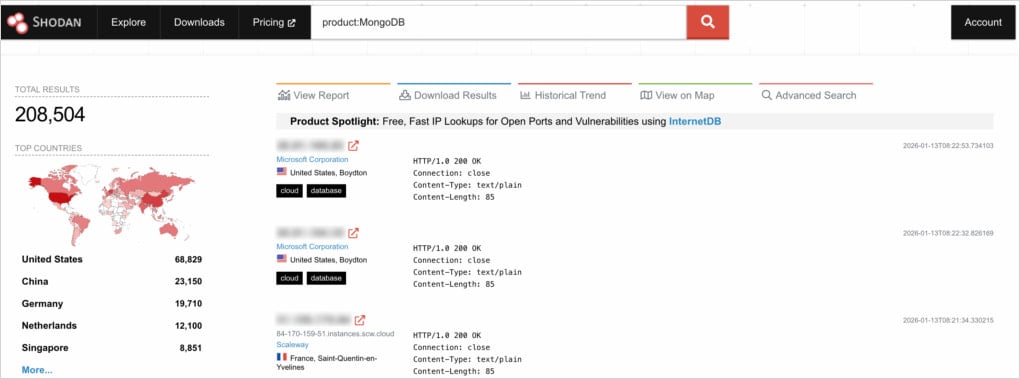
Supply: Flare
Practically half (Forty five.6%) of those with unrestricted regain entry to had already been compromised when Flare examined them. The database had been wiped, and a ransom present became left.
An diagnosis of the ransom notes showed that virtually all of them demanded a fee of 0.005 BTC internal forty eight hours.
“Threat actors quiz fee in Bitcoin (in most cases around 0.005 BTC, equivalent at the moment time to $500-600 USD) to a specified wallet contend with, promising to restore the records,” reads the Flare sage.
“Nevertheless, there would possibly be no longer any such thing as a guarantee the attackers delight in the records, or will provide a working decryption key if paid.”
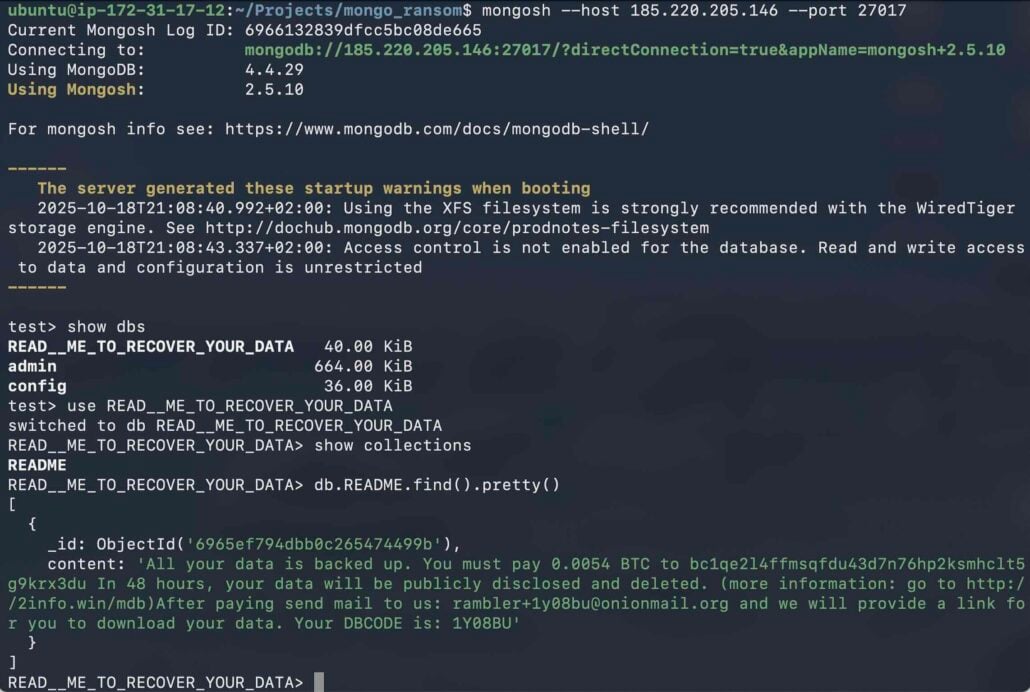
Supply: Flare
There had been only five distinct wallet addresses all the plan in which by the dropped ransom notes, and one of them became prevalent in about 98% of the situations, indicating a single threat actor focusing on these assaults.
Flare moreover comments on the closing exposed cases that didn’t seem to had been hit, even supposing they had been exposed and poorly secured, hypothesizing that those also can delight in already paid a ransom to the attackers.
As well to unhappy authentication measures, the researchers moreover came all the plan in which by that practically half (95,000) of all cyber web-exposed MongoDB servers trudge older variations that are inclined to n-day flaws. Nevertheless, the aptitude of most of those became restricted to denial-of-service assaults, no longer offering a ways off code execution.
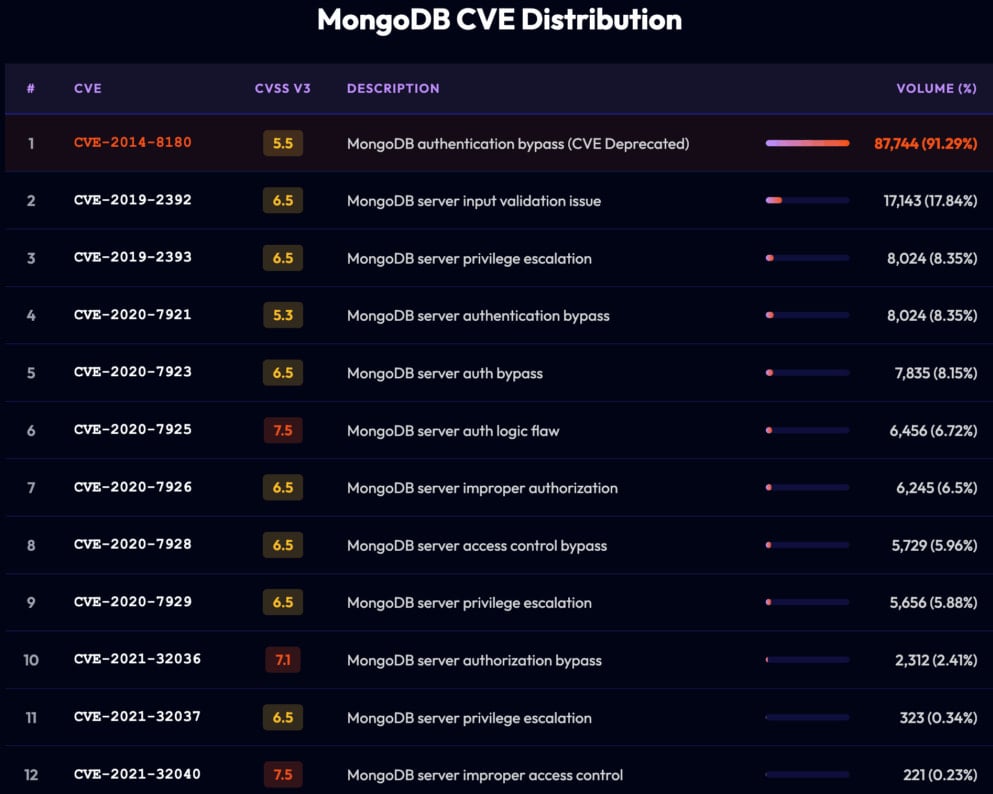
Supply: Flare
Flare suggests that MongoDB administrators steer determined of exposing cases to the final public until it’s completely needed, exercise sturdy authentication, put in force firewall principles and Kubernetes community insurance policies that enable only depended on connections, and steer determined of copying configurations from deployment guides.
MongoDB need to be up to this point to essentially the most modern version and repeatedly monitored for exposure. Within the case of exposure, credentials need to be rotated and logs examined for unauthorized exercise.
Cybercrime The manner forward for IT infrastructure is right here
Widespread IT infrastructure moves faster than manual workflows can contend with.
In this fresh Tines records, learn how your crew can decrease hidden manual delays, give a boost to reliability by automated response, and regain and scale piquant workflows on high of tools you already exercise.
Recent Posts
- Hong Kong small print investigations into online food complaints
- Republican Secretary of Inform Brad Raffensperger Names Jason Doss as Investigative Agent in First Liberty Fallout
- Exposed MongoDB cases soundless centered in records extortion assaults
- I invited hackers to attack my dwelling server, and the outcomes had been a warning sign
- I watched the Georgia 2020 divulge. Here’s what the FBI raid in Fulton County is de facto about.




