
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Discord flaw lets hackers reuse expired invites in malware advertising campaign

Jun
Discord flaw lets hackers reuse expired invites in malware advertising campaign
Private eye

Hackers are hijacking expired or deleted Discord invite links to redirect users to malicious web sites that raise far away obtain admission to trojans and facts-stealing malware.
The advertising campaign relies on a flaw within the Discord invitation blueprint to leverage multi-stage infections that evade multiple antivirus engines.
Private eye “Reviving” expired Discord invites
Discord invite links are URLs that allow someone to affix a particular Discord server. They respect an invite code, which is a gripping identifier that grants obtain admission to to a server and is also transient, permanent, or custom – arrogance links on hand to ‘level 3’ servers paying for particular perks.
As part of the perks for level 3 Discord servers, administrators can manufacture a personalised invite code. For fashioned servers, Discord generates random invite links robotically and the likelihood of one repeating itself is terribly low.
Nonetheless, hackers noticed that after a level 3 server loses its boost notify, the custom invite code becomes on hand and is also reclaimed by one other server.
Researchers at cybersecurity firm Take a look at Level snarl that right here’s moreover proper within the case of expired transient invites or deleted permanent invitation links.
They snarl that “the mechanism for creating custom invite links surprisingly lets you reuse expired temporary invite codes, and, in some cases, deleted permanent invite codes.”
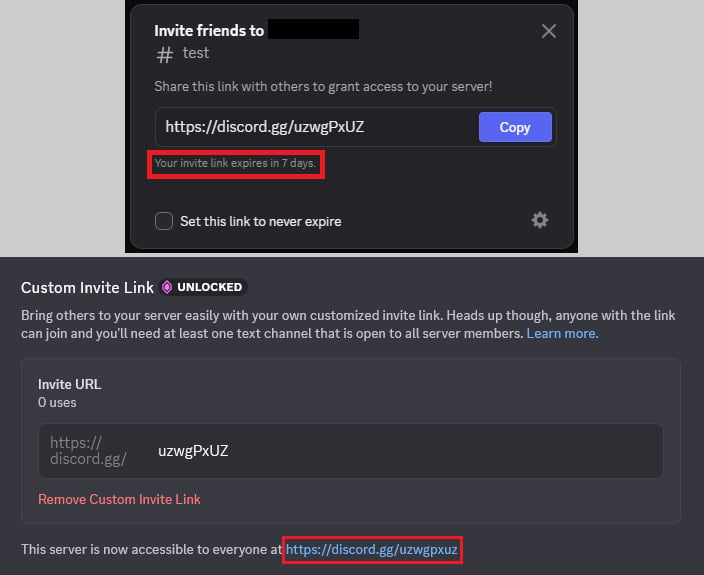
Source: Take a look at Level
Furthermore, the researchers snarl that Discord’s wicked mechanism would no longer regulate the expiration time of an already generated transient invitation code when reusing it as a permanent invitation hyperlink.
“Users often mistakenly believe that by simply checking this box, they have made the existing invite permanent (and it was this misunderstanding that was exploited in the attack we observed)” – Take a look at Level
An invite code with lowercase letters and digits can not be registered as long as it’s miles active. Nonetheless, if the code has uppercase letters, it’s miles also reused in arrogance links with lowercase, even when the distinctive remains to be accurate.
Take a look at Level researchers display that right here’s seemingly ensuing from Discord stores and compares arrogance links in lowercase. As a result, the identical code with decrease and uppercase letters is accurate for 2 separate servers on the identical time.
Redirecting to malicious servers
Attackers are monitoring deleted or expired Discord invitations and use them in a advertising campaign that has impacted 1,300 users within the US, UK, France, the Netherlands, and Germany, per Take a look at Level’s acquire depend of the malicious payloads.
The researchers snarl that cybercriminals are hijacking Discord invite links from legitimate communities, and share them on social media or respectable comunity web sites. So that you simply may perhaps add credibility to the deceit, hackers create the malicious servers to move looking out legitimate.
The malicious Discord servers excellent present a single channel to the visitor, #take a look at, and a bot prompts the particular person to move thru a verification process.
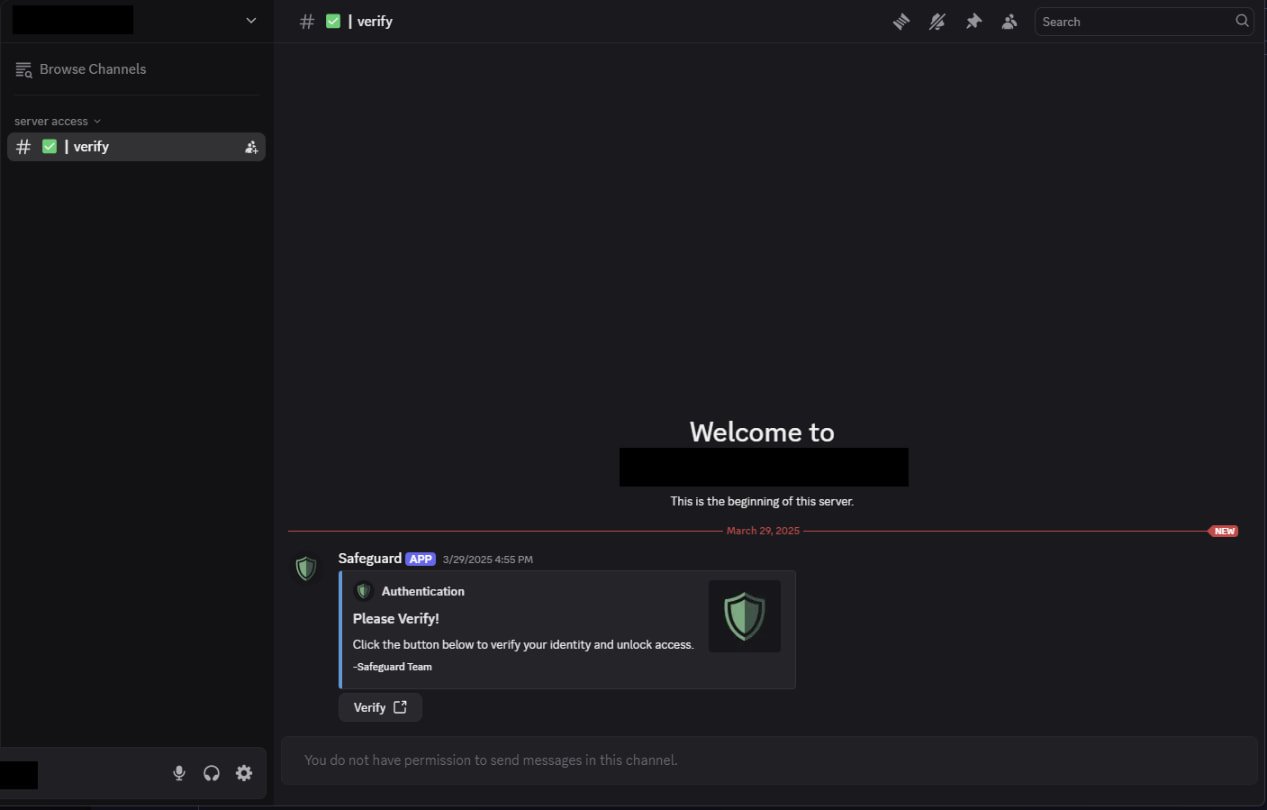
Source: Take a look at Level
Attempting to realize so launches a identical old ‘ClickFix’ assault the assign the particular person is redirected to a web dwelling that mimics the Discord UI and pretends that the CAPTCHA didn’t load.
The users are tricked into manually opening the Windows Tear dialog and pasting a PowerShell say, which they had already copied to the clipboard for execution.
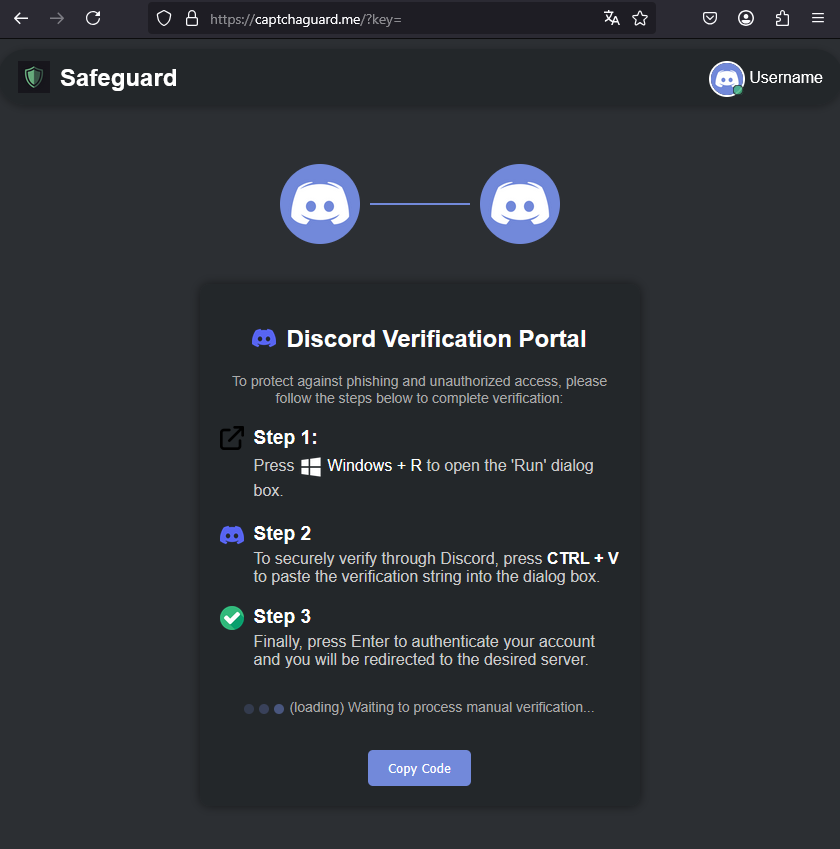
Source: Take a look at Level
Doing so triggers a multi-stage infection involving PowerShell downloaders, obfuscated C++ loaders, and VBScript recordsdata.
The final payloads are downloaded from the legitimate Bitbucket instrument collaboration and file web hosting service, and consist of:
- AsyncRAT: Delivered as ‘AClient.exe,’ right here’s version 0.5.8 of the malware that makes use of Pastebin to acquire its C2 deal with dynamically. Its capabilities consist of file operations, keylogging, and webcam/microphone obtain admission to
- Skuld Stealer: Delivered as ‘skul.exe,’ right here’s an facts-stealer that targets browser credentials, cookies, Discord tokens, and cryptocurrency wallet facts (injects JS to snatch mnemonic phrases and passwords the utilization of Discord webhooks)
- ChromeKatz: A custom version of the the start-source tool, delivered as ‘cks.exe’, that would perhaps well grab cookies and passwords
A scheduled job is moreover added on the host to re-bustle the malware loader every 5 minutes, the researchers came upon.
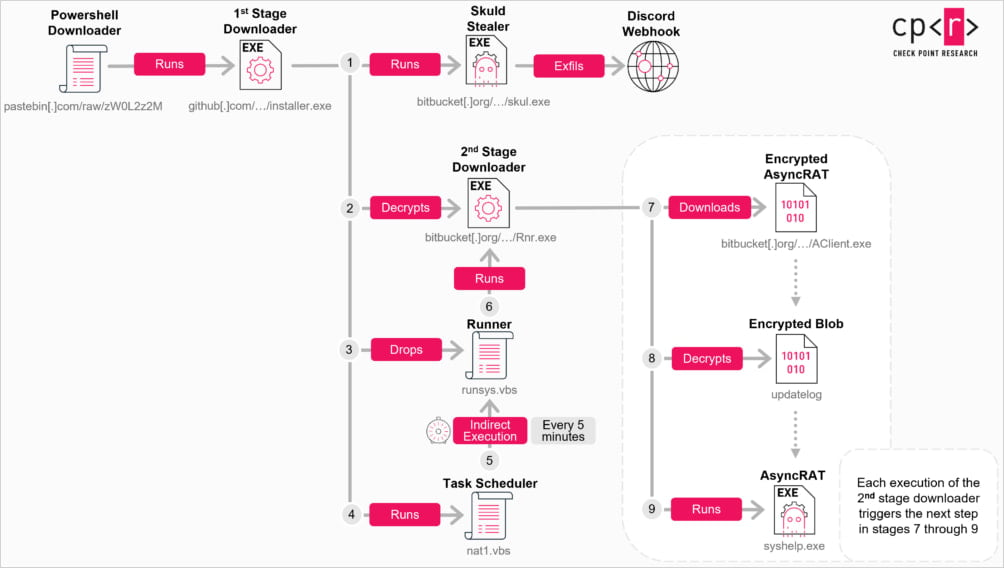
Source: Take a look at Level
To defend in opposition to this possibility, it’s urged that Discord users respect far from trusting used invite links, in particular those from months-used posts, deal with “verification” requests with additional caution, and never bustle copied PowerShell commands that you simply don’t fully realize.
Furthermore, Discord server administrators are urged to use permanent invites, that are more complicated to hijack.
Private eye Why IT teams are ditching manual patch management
Patching dilapidated to mean advanced scripts, long hours, and unending fireplace drills. No longer anymore.
In this original facts, Tines breaks down how original IT orgs are leveling up with automation. Patch sooner, decrease overhead, and focal level on strategic work — no advanced scripts required.
Recent Posts
- Broker who supplied malware to the FBI space for sentencing
- How ex-Prince Andrew dragged the Queen, Charles, William — and even Harry — into his dark shadows
- Original Documents Present a Controversial Vaccine Glimpse’s Distinctive Path to CDC Approval
- Angry Trump indicators global 10% responsibility after supreme courtroom points tariff blow
- Officials examine deadly California avalanche for doubtless prison negligence



