
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Author: ForensicsS
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > Articles by: ForensicsS

Feb
Chuck Todd Says Ancient Colleague Savannah Guthrie Will Solve ‘Heartbreaking and Surreal’ Mystery of Lacking Mother | Video
Mobile forensics Chuck Todd turned emotional and stumbled over his phrases as he weighed in on frail co-host Savannah Guthrie’s quest to earn her lacking mother. The duo co-anchored the MSNBC demonstrate “The Every day Rundown” from its inception in 2010. CNN’s “The Enviornment” host Kasie Hunt asked Todd what his tips were as the Guthries enter […]

Feb
FBI says it’s unaware of Savannah Guthrie talking alongside side her mother’s suspected kidnappers
Data breach Skip to Main Utter Nationwide News Data breach Savannah Guthrie talked about the family became “at an hour of desperation” in a video launched Monday, apt hours sooner than a purported ransom closing date interestingly way by her mother’s abductors. On this instruct supplied by NBCUniversal, Savannah Guthrie, appropriate, her mother Nancy enlighten, […]

Feb
New: Savannah Guthrie Pleads for Wait on As Investigation Extends to Residence of Her Sister, Annie
Digital forensics We’re over a week into the investigation into the mysterious disappearance of Arizona resident Nancy Guthrie, and if the authorities are any nearer to checking out where she is, what happened to her, who took her, and loads others., than they were when they started, that’s now not one thing they’ve shared with […]

Feb
Savannah Guthrie pleads for public’s relieve as compare her missing mother continues
OSINT Tv host Savannah Guthrie issued a determined plea for anybody who may possibly possibly know one thing about her missing mother to contact regulation enforcement on Monday, as the compare Nancy Guthrie entered its ninth day. “We need your relieve,” talked about Savannah Guthrie, eight days after her mother become first reported missing. Investigators […]

Feb
Defective Bunny’s Expose Became Anticipated To Provoke. Did It?
Internet investigation Please enable JS and disable any advert blocker Learn More

Feb
Artificial intelligence experts work with police officers to hunt down clues in Nancy Guthrie ransom point out
Cyber investigation A fundamental deadline dwelling by Nancy Guthrie’s kidnappers handed without her return Monday night, with the FBI asserting it’s a long way no longer attentive to any verbal substitute between the abductors and the Guthrie family and has no longer known any suspects in the case. In a ransom point out, the purported […]
Ghislaine Maxwell pleads the Fifth in Dwelling Oversight Epstein investigation
Online fraud The congressional investigation into convicted intercourse offender Jeffrey Epstein hit its newest snag Monday morning when Epstein’s longtime accomplice, Ghislaine Maxwell, declined to reply questions in a sworn deposition. Maxwell, now serving a 20-year sentence for her segment in Epstein’s intercourse trafficking scheme, invoked her Fifth Amendment accurate over video from a detention […]

Feb
Watch Nancy Guthrie enters 2d week
Private investigator The quest for Nancy Guthrie has entered its 2d week as investigators possess yet to establish suspects tied to the disappearance of the 84-year-venerable. The FBI and the Pima County Sheriff’s Department are co-main the probe into Guthrie’s abrupt absence. She used to be remaining viewed at her home diagram Tucson…Be taught More

Feb
South Korea’s FSS Launches AI-Powered Crackdown on Crypto Market Manipulation
Internet investigation Internet investigation TLDR: FSS targets whale shopping and selling, cage methods, and racehorse schemes in deliberate 2026 market investigations AI-powered programs will analyze odd impress surges inner seconds to title manipulation patterns Digital Asset Common Act preparatory team established to toughen segment-2 digital asset legislation Contemporary licensing manuals developed for digital asset provider […]
Feb
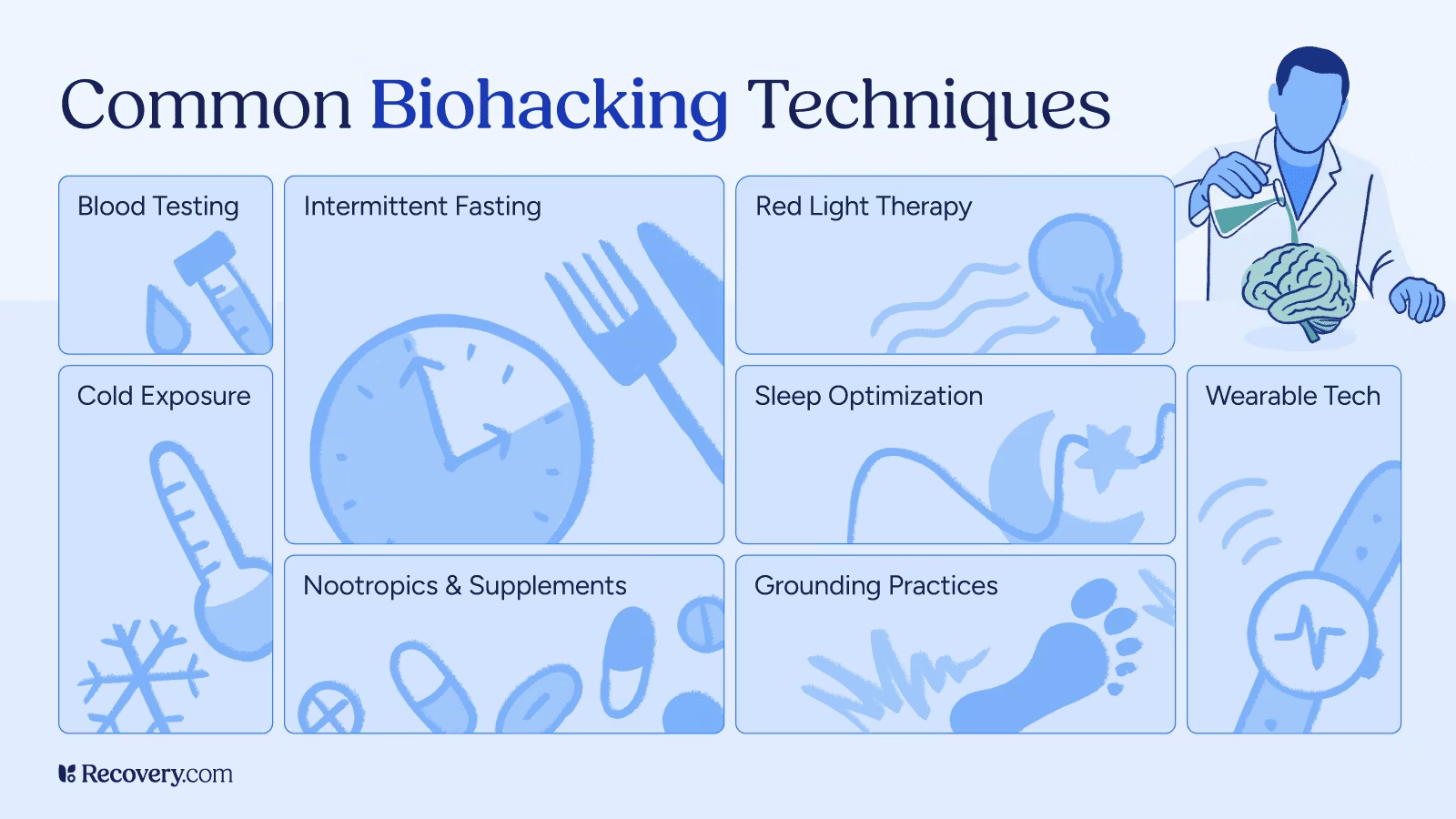
Biohacking Implants: When Human Optimization Becomes Too Unhealthy
Internet investigation Image supply: restoration.com Key takeaways: Biohacking has gone mainstream: What started with successfully being trackers and sleep apps now involves hardware implants, with 67% of American citizens in a most up-to-date survey figuring out as biohackers. Grinder biohacking goes previous monitoring: Grinders implant magnets, NFC and RFID chips, and varied devices straight into […]
Recent Posts
- Olympic snowboarder turned drug lord ‘captured by FBI’
- Damaged-down Olympic snowboarder accused of trafficking capsules by map of California arrested
- Quit as a provider: Microsoft unlocks BitLocker for feds
- Hackers Allegedly Steal Get entry to Tokens, Confidential Paperwork From European Location Company
- FBI investigates suspicious breach of its networks

