
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Canada Goose investigating as hackers leak 600K buyer data

Feb
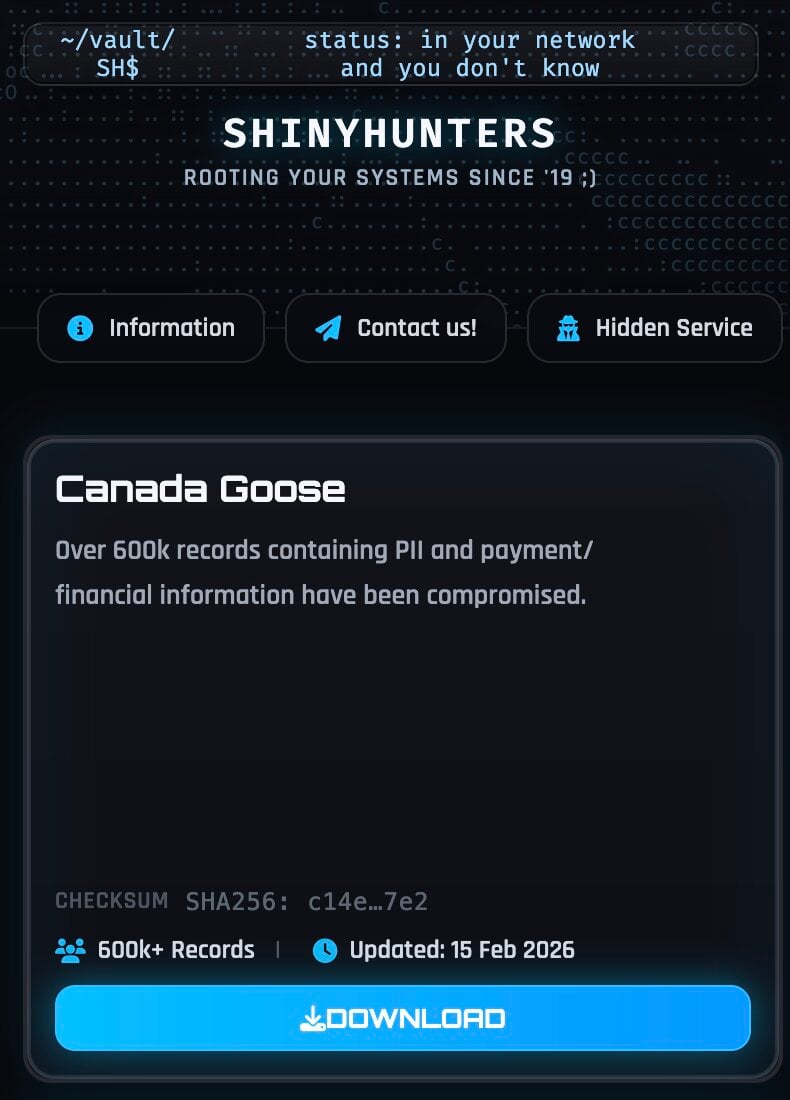
Canada Goose investigating as hackers leak 600K buyer data
Private eye

ShinyHunters, a infamous files extortion community, claims to acquire stolen more than 600,000 Canada Goose buyer data containing within most and price-associated files.
Canada Goose urged BleepingComputer the dataset appears to be like to recount to previous buyer transactions and that it has no longer stumbled on evidence of a breach of its acquire systems.
Based in 1957, Canada Goose is a Toronto-essentially based totally performance luxurious outerwear trace with a world retail footprint and nearly 4,000 workers.
Private eye Canada Goose sees no evidence of breach
“Canada Goose is aware that a historical dataset relating to past customer transactions has recently been published online,” the firm urged BleepingComputer.
“At this time, we have no indication of any breach of our own systems. We are currently reviewing the newly released dataset to assess its accuracy and scope and will take any further steps as may be appropriate. To be clear, our review shows no evidence that unmasked financial data was involved. Canada Goose remains committed to protecting customer information.”
Private eye 1.67 GB dataset contains detailed uncover data
ShinyHunters added Canada Goose to its files leak spot this week, claiming the archive contains more than 600,000 buyer data.
(BleepingComputer)
Samples reviewed by BleepingComputer worth that the 1.67 GB dataset, released in JSON format, contains detailed e-commerce uncover data, collectively with buyer names, email addresses, cell phone numbers, billing and start addresses, IP addresses, and uncover histories.
The guidelines additionally contains partial price card files equivalent to card trace, the final four digits of card numbers, and in some cases the main six digits (BIN), along with price authorization metadata.
While the dataset does no longer appear to acquire elephantine price card numbers, the uncovered files could well silent be conventional for centered phishing, social engineering, and fraud.
The data additionally encompass acquire historical previous, instrument and browser files, and uncover values, doubtlessly allowing attackers to profile excessive-trace possibilities.
Private eye Hackers teach hyperlink to most modern SSO attacks
ShinyHunters has no longer too lengthy previously been linked to a wave of social-engineering attacks focused on single worth-on (SSO) accounts and cloud environments.
When asked whether or no longer the Canada Goose files used to be obtained thru these intrusions, the community urged BleepingComputer the dataset used to be unrelated, claiming it originated from a third-occasion price processor breach and dates support to August 2025.
BleepingComputer has no longer independently verified the recount.
The dataset’s schema (specifically, area names admire checkout_id, shipping_lines, cart_token, cancel_reason, etc.), nevertheless, intently resembles e-commerce checkout exports recurrently associated to hosted storefront and price processing platforms, which could just support worth how the suggestions can acquire originated from a third-occasion carrier provider.
Private eye Who is ShinyHunters?
ShinyHunters is a prolific files extortion community known for stealing and leaking huge volumes of buyer files from main producers and online companies and products.
The community has been linked to quite diverse excessive-profile breaches and data theft incidents in most modern years, frequently focused on e-commerce platforms, SaaS companies and products, and cloud environments.
In most modern reporting, safety researchers acquire tied the community to vishing and social-engineering campaigns conventional to maintain fetch admission to to company accounts and cloud files.
Stolen files is in total conventional for extortion, equipped on underground forums, or published on the community’s leak spot when victims refuse to pay.
It’s no longer but known how many Canada Goose possibilities will be affected or whether or no longer contributors will be notified. The firm says it is continuing to review the dataset to search out out its accuracy and scope.
Private eye The future of IT infrastructure is here
Popular IT infrastructure moves sooner than manual workflows can handle.
On this novel Tines files, be taught how your group of workers can carve hidden manual delays, enhance reliability thru computerized response, and maintain and scale radiant workflows on top of instruments you already use.
Recent Posts
- Canada Goose investigating as hackers leak 600K buyer data
- Housebreaking thought in missing Guthrie case ‘ridiculously uncommon’ says legislation enforcement offer
- ‘Attain the Valid Thing’: Savannah Guthrie’s Decided Plea as FBI Says Found Glove Likely Matches Suspect’s Gloves
- FBI: DNA from glove advance Guthrie home appears to be like to compare glove feeble by suspect
- Congress needs to benefit Americans do sense of what occurred in Minneapolis




