
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > WinRAR course traversal flaw peaceable exploited by a massive amount of hackers

Jan
WinRAR course traversal flaw peaceable exploited by a massive amount of hackers
OSINT

Quite a lot of probability actors, both affirm-backed and financially motivated, are exploiting the CVE-2025-8088 high-severity vulnerability in WinRAR for initial entry and to bring diversified malicious payloads.
The safety subject is a course traversal flaw that leverages Alternate Data Streams (ADS) to jot down malicious files to arbitrary areas. Attackers earn exploited this in the previous to plant malware in the Home windows Startup folder, for persistence someday of reboots.
Researchers at cybersecurity company ESET chanced on the vulnerability and reported in early August 2025 that the Russia-aligned community RomCom had been exploiting it in zero-day attacks.
In a file on the present time, the Google Possibility Intelligence Crew (GTIG) says that exploitation started as early as July 18, 2025, and continues to this day from both affirm-backed espionage actors and decrease-tier, financially motivated cybercriminals.
“The exploit chain in overall entails concealing the malicious file for the length of the ADS of a decoy file contained in the archive.
“While the user typically views a decoy document, such as a PDF, within the archive, there are also malicious ADS entries, some containing a hidden payload while others are dummy data,” Google researchers indicate.
When opened, WinRAR extracts the ADS payload utilizing directory traversal, in overall shedding LNK, HTA, BAT, CMD, or script files that secure on user login.
Amongst the affirm-backed probability actors that Google researchers seen exploiting CVE-2025-8088 are:
- UNC4895 (RomCom/CIGAR) delivering NESTPACKER (Snipbot) through the use of spearphishing to Ukrainian armed forces units.
- APT44 (FROZENBARENTS) utilizing malicious LNK files and Ukrainian-language decoys for practice-on downloads.
- TEMP.Armageddon (CARPATHIAN) shedding HTA downloaders into Startup folders (job ongoing into 2026).
- Turla (SUMMIT) delivering the STOCKSTAY malware suite utilizing Ukrainian military topics.
- China-linked actors utilizing the exploit to deploy POISONIVY, dropped as a BAT file that downloads extra payloads.
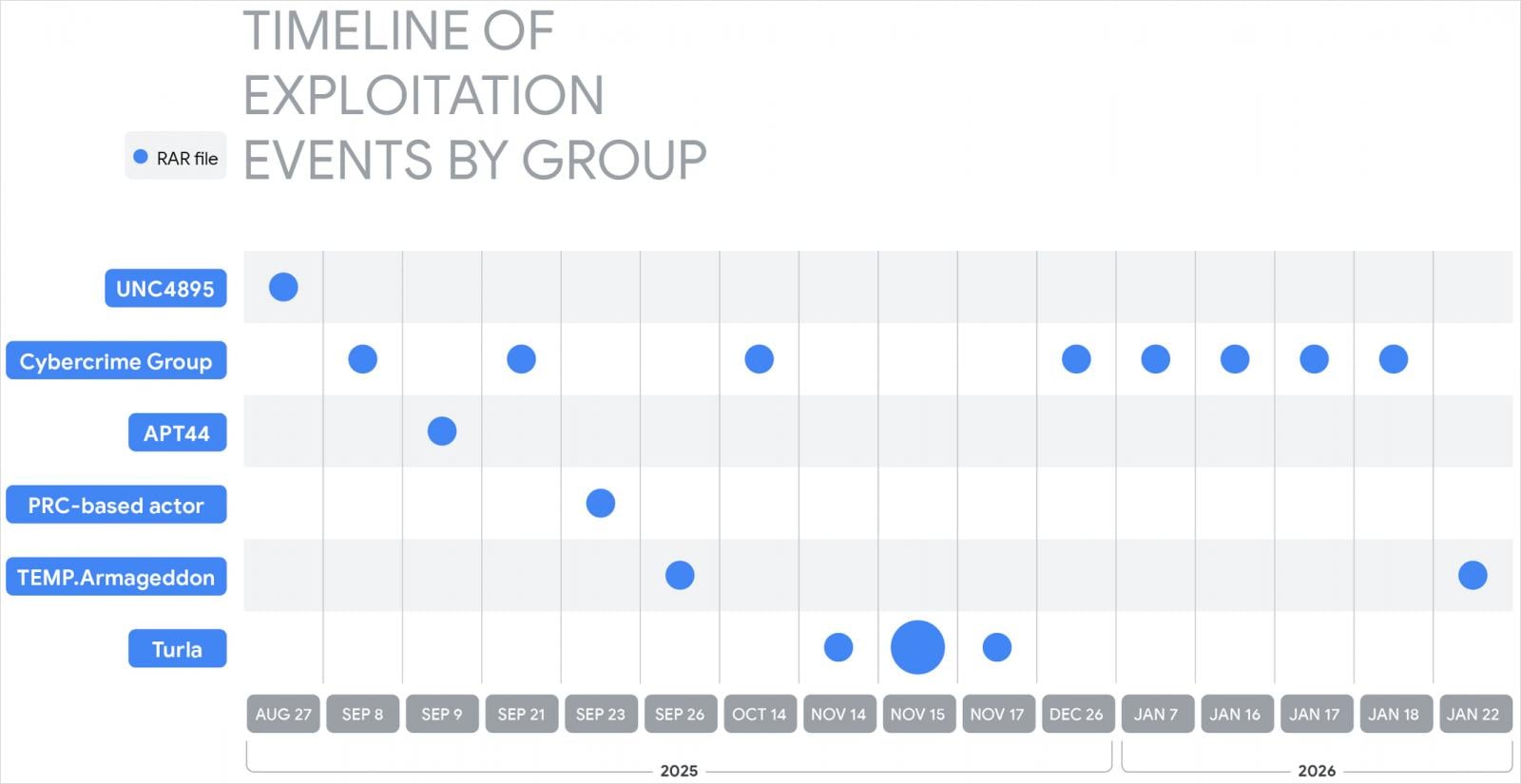
Source: Google
Google moreover seen financially motivated actors exploiting the WinRAR course-traversal flaw to distribute commodity remote entry tools and files stealers a lot like XWorm and AsyncRAT, Telegram bot-controlled backdoors, and malicious banking extensions for the Chrome browser.
All these probability actors are believed to earn sourced working exploits from for sprint supreme suppliers, a lot like one utilizing the alias “zeroplayer,” who advertised a WinRAR exploit closing July.
The identical probability actor has moreover marketed just a few high-price exploits closing year, along side alleged zero-days for Microsoft Place of job sandbox lunge, company VPN RCE, Home windows native privilege escalation, and bypasses for security solutions (EDR, antivirus), promoting them for costs between $80,000 and $300,000.
Google feedback that this reflects the commoditization of exploit pattern, which is major in the cyberattacks lifecycle, decreasing the friction and complexity for attackers and enabling them to kind out unpatched systems in a short time.
OSINT The 2026 CISO Funds Benchmark
It be funds season! Over 300 CISOs and security leaders earn shared how they’re planning, spending, and prioritizing for the year forward. This file compiles their insights, allowing readers to benchmark suggestions, identify rising tendencies, and overview their priorities as they head into 2026.
Be taught the intention top leaders are turning investment into measurable impact.
Recent Posts
- Trump’s FBI says ‘Epstein’ penal advanced postcard to pedophile Larry Nassar is FAKE
- Epstein’s brother’s wild converse that Trump authorized his homicide is unearthed in DOJ files
- Informant steered FBI that Jeffrey Epstein had a ‘non-public hacker’
- Fireblocks CEO says North Korea-linked job recruitment scam centered LinkedIn profiles
- How Criminal Millions Sprinted Via Binance, OKX, and Thoroughly different High Crypto Exchanges
Recent Comments
Categories
Recent Posts





