
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > cybersecurity > Chinese Mustang Panda hackers deploy infostealers by technique of CoolClient backdoor

Jan
Chinese Mustang Panda hackers deploy infostealers by technique of CoolClient backdoor
Identity theft

The Chinese espionage threat team Mustang Panda has up up to now its CoolClient backdoor to a brand sleek variant that can design shut login records from browsers and video show the clipboard.
In step with Kaspersky researchers, the malware has moreover been feeble to deploy a beforehand unseen rootkit. On the other hand, a technical prognosis will seemingly be equipped in a future checklist.
CoolClient has been connected with Mustang Panda since 2022, deployed as a secondary backdoor alongside PlugX and LuminousMoth.
The up up to now malware version has been seen in assaults concentrated on government entities in Myanmar, Mongolia, Malaysia, Russia, and Pakistan and were deployed by technique of legitimate utility from Sangfor, a Chinese company specialised in cybersecurity, cloud computing, and IT infrastructure merchandise.
Beforehand, CoolClient operators launched the malware by technique of DLL aspect-loading by abusing signed binaries from Bitdefender, VLC Media Player, and Ulead PhotoImpact.
Kaspersky researchers converse that the CoolClient backdoor gathers particulars about the compromised machine and its users, esteem computer title, version of the running machine, RAM, network records, and the descriptions and variations of loaded driver modules.
CoolClient uses encrypted .DAT recordsdata in a multi-stage execution and achieves persistence by technique of Registry adjustments, the addition of sleek Home windows providers, and scheduled duties. It moreover helps UAC bypassing and privilege escalation.
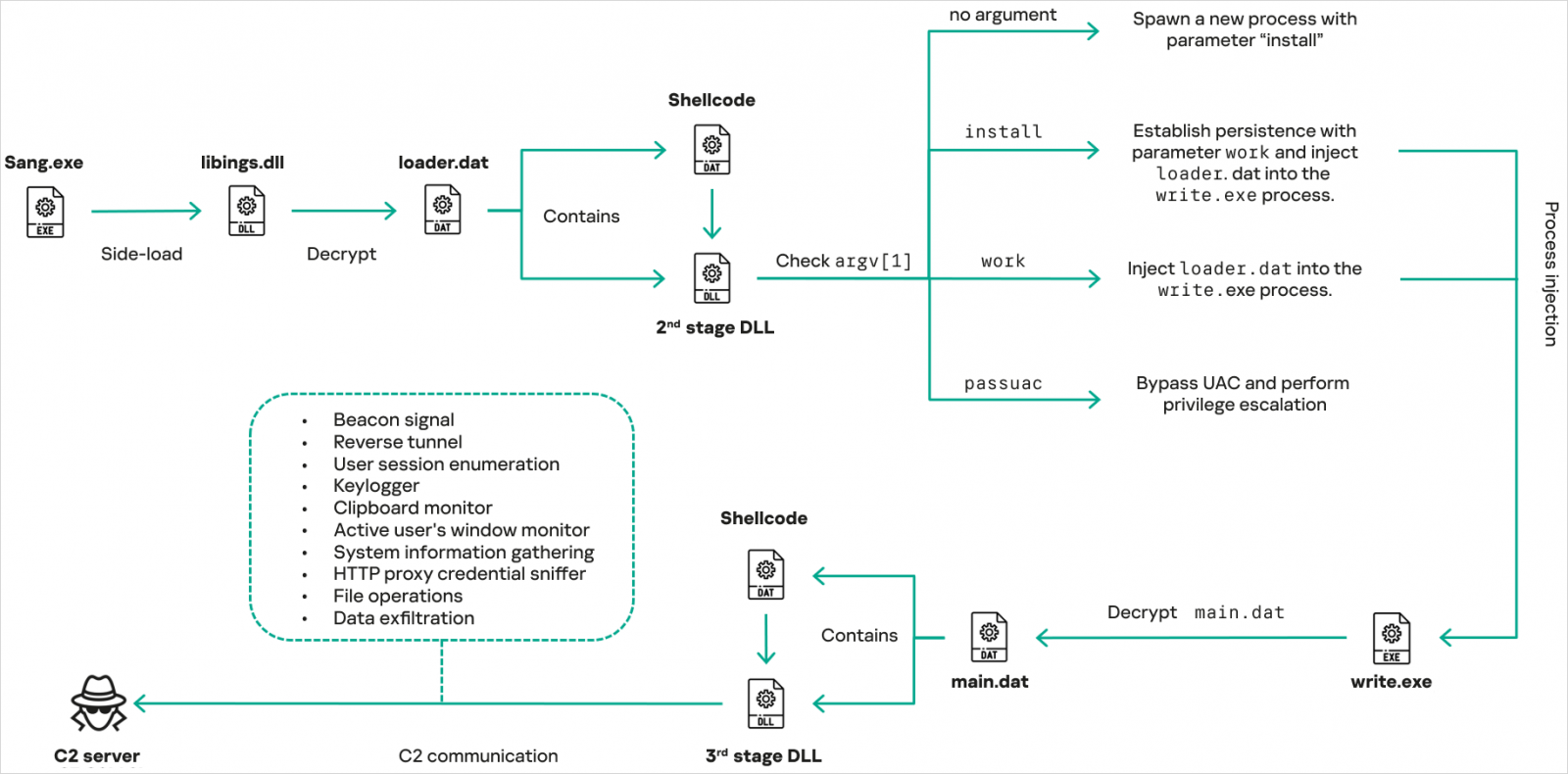
Source: Kaspersky
CoolClient’s core aspects are integrated in a DLL embedded in a file known as predominant.dat. “When launched, it first checks whether the keylogger, clipboard stealer, and HTTP proxy credential sniffer are enabled,” the researchers converse.
Original CoolClient capabilities
The malware’s core functions, including machine and user profiling, file operations, keylogging, TCP tunneling, reverse-proxying, and in-memory execution of dynamically fetched plugins, will seemingly be found in both passe and sleek variations, but are sophisticated in potentially the newest variants.
What’s completely sleek in potentially the most up to the moment CoolClient is a clipboard monitoring module, the skill to manufacture active window title monitoring, and HTTP proxy credential sniffing that relies on raw packet inspection and headers extraction.
Additionally, the plugin ecosystem has been expanded with a dedicated faraway shell plugin, a carrier management plugin, and a extra succesful file management plugin.
The carrier management plugin enables the operators to enumerate, set apart, delivery, cease, delete, and alter the startup configuration of Home windows providers, whereas the file management plugin affords prolonged file operations, including power enumeration, file search, ZIP compression, network power mapping, and file execution.
Faraway shell performance is implemented by technique of a separate plugin that spawns a hidden cmd.exe process and redirects its customary enter and output thru pipes, enabling interactive say execution over the say-and-assign a watch on (C2) channel.
A novelty in CoolClient’s operation is the deployment of infostealers to salvage login records from browsers. Kaspersky documented three optimistic families concentrated on Chrome (variant A), Edge (variant B), and a extra versatile variant C that targets any Chromium-basically based browser.
Source: Kaspersky
One more critical operational shift is that browser records theft and doc exfiltration now leverage hardcoded API tokens for legitimate public providers esteem Google Force or Pixeldrain to evade detection.
Mustang Panda continues to conform its toolset and operational traits. Last month, Kaspersky reported about a sleek kernel-mode loader that deployed a variant of the ToneShell backdoor on government systems.
Earlier this month, Taiwan’s National Safety Bureau ranked Mustang Panda among the many most prolific and excessive-quantity threats concentrated on its serious infrastructure.
Identity theft Secrets Safety Cheat Sheet: From Sprawl to Tackle watch over
Whether or no longer you are cleaning up passe keys or surroundings guardrails for AI-generated code, this records helps your personnel fabricate securely from the delivery.
Get hold of the cheat sheet and design shut the guesswork out of secrets and tactics management.
Recent Posts
- Trump’s FBI says ‘Epstein’ penal advanced postcard to pedophile Larry Nassar is FAKE
- Epstein’s brother’s wild converse that Trump authorized his homicide is unearthed in DOJ files
- Informant steered FBI that Jeffrey Epstein had a ‘non-public hacker’
- Fireblocks CEO says North Korea-linked job recruitment scam centered LinkedIn profiles
- How Criminal Millions Sprinted Via Binance, OKX, and Thoroughly different High Crypto Exchanges
Recent Comments
Categories
Recent Posts





