
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Konni hackers purpose blockchain engineers with AI-built malware

Jan
Konni hackers purpose blockchain engineers with AI-built malware
Identity theft

The North Korean hacker team Konni (Opal Sleet, TA406) is the articulate of AI-generated PowerShell malware to purpose builders and engineers in the blockchain sector.
Believed to be related with APT37 and Kimsuky articulate clusters, Konni has been enthralling since at the very least 2014 and has been considered concentrated on organizations in South Korea, Russia, Ukraine, and varied countries in Europe.
In accordance with samples analyzed by Take a look at Point researchers, the risk actor’s most modern campaign specializes in targets in the Asia-Pacific state, as the malware used to be submitted from Japan, Australia, and India.
The assault begins with the sufferer receiving a Discord-hosted link that delivers a ZIP archive containing a PDF entice and a malicious LNK shortcut file.
The LNK runs an embedded PowerShell loader that extracts a DOCX document and a CAB archive containing a PowerShell backdoor, two batch files, and a UAC bypass executable.
Launching the shortcut file causes the DOCX to inaugurate and to fabricate one batch file integrated in the cupboard file.
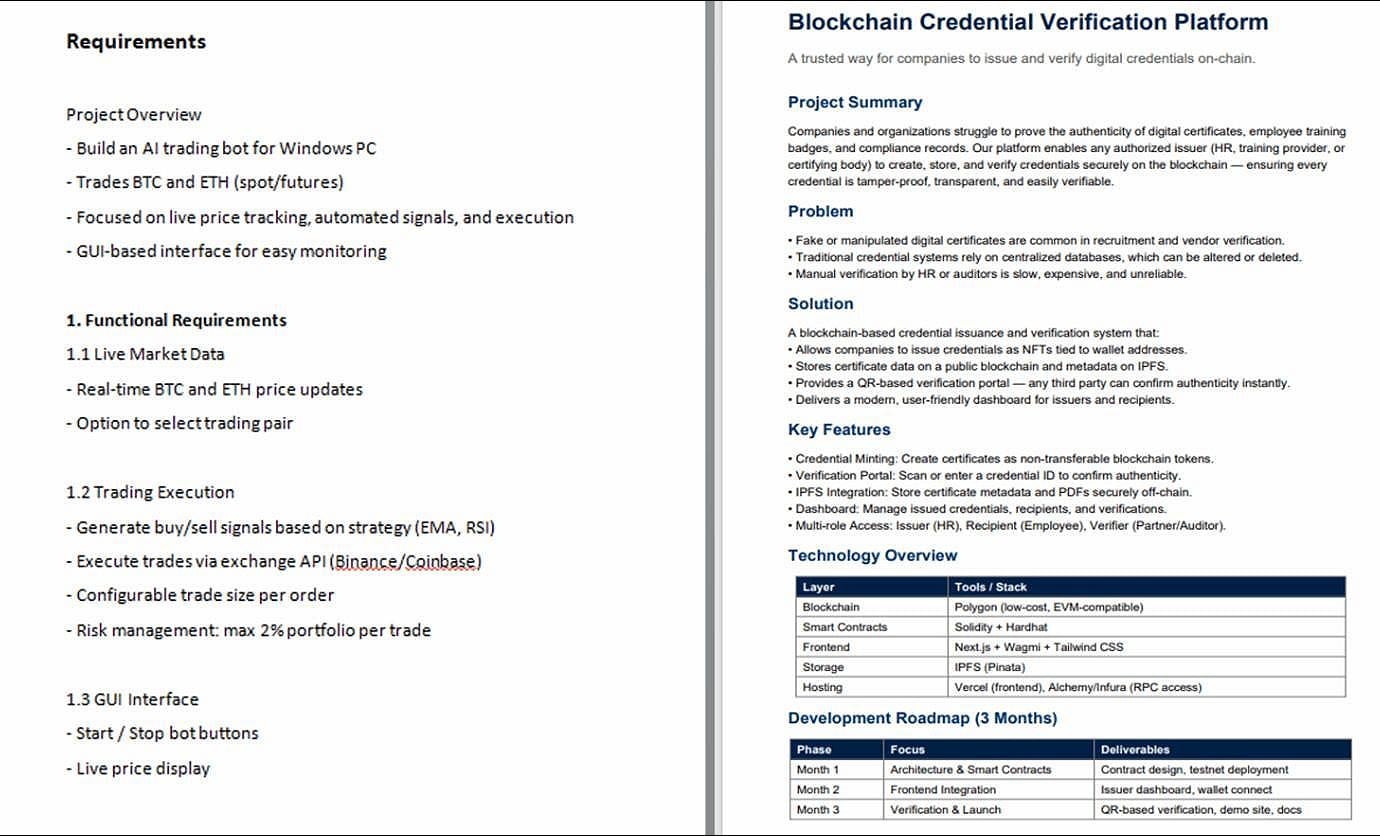
Offer: Take a look at Point
The entice DOCX document suggests that the hackers want to compromise style environments, which would per chance also provide them “access to sensitive assets, including infrastructure, API credentials, wallet access, and ultimately cryptocurrency holdings.”
The first batch file creates a staging itemizing for the backdoor and the 2d batch file, and creates an hourly scheduled project masquerading as a OneDrive startup project.
This project reads an XOR-encrypted PowerShell script from disk and decrypts it for in-memory execution. At closing, it deletes itself to wipe the indicators of infection.
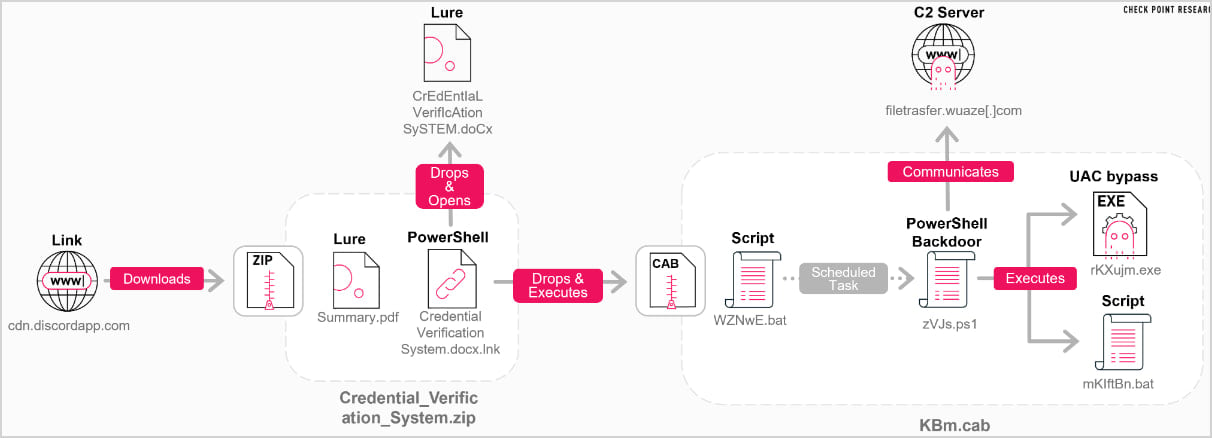
Offer: Take a look at Point
Identity theft AI-generated backdoor
The PowerShell backdoor itself is carefully obfuscated the articulate of arithmetic-based string encoding, runtime string reconstruction, and execution of the closing common sense through ‘Invoke-Expression.’
The researchers tell that the PowerShell malware “strongly indicates AI-assisted development rather than traditional operator-authored malware.”
The evidence leading to this conclusion contains the particular, structured documentation at the dwell of the script, which is strange for malware style; its modular, pleasing format; and the presence of a “# <– your permanent mission UUID” comment.
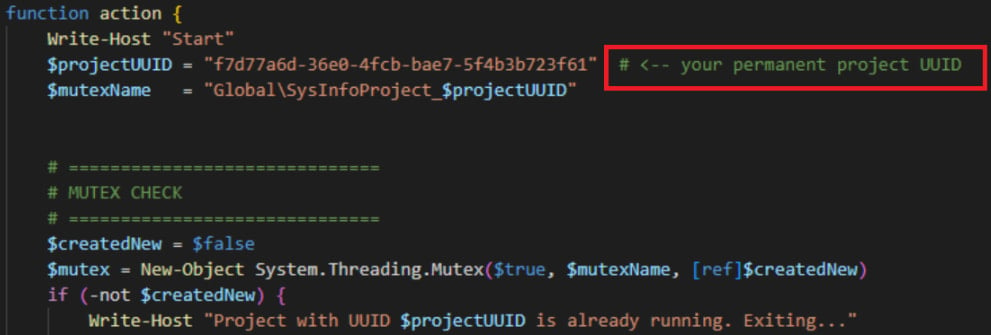
Offer: Take a look at Point
“This phrasing is highly characteristic of LLM-generated code, where the model explicitly instructs a human user on how to customize a placeholder value,” explains Take a look at Point.
“Such comments are commonly observed in AI-produced scripts and tutorials.”
Before execution, the malware performs hardware, system, and user articulate assessments to be sure it is not working in prognosis environments, and then generates a streak host ID.
Subsequent, reckoning on what execution privileges it has on the compromised host, it follows a separate course of action as proven in the next plot.
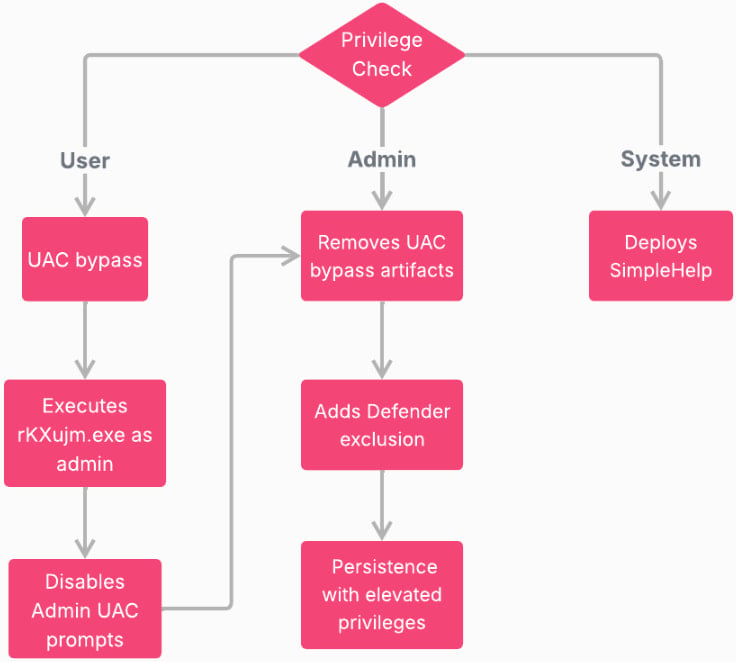
Offer: Take a look at Point
Once the backdoor is utterly working on the contaminated system, it periodically contacts the converse-and-contend with watch over (C2) server to send traditional host metadata and polls the server at randomized intervals.
If the C2 response contains PowerShell code, it turns it staunch into a script block and executes it asynchronously through background jobs.
Take a look at Point attributes these attacks to the Konni risk actor according to earlier launcher formats, entice filename and script title overlaps, and commonalities in the execution chain structure with earlier attacks.
The researchers bear printed indicators of compromise (IoCs) related with this contemporary campaign to aid defenders provide protection to their resources.
Identity theft Secrets and recommendations Security Cheat Sheet: From Sprawl to Retain an eye on
Whether you furthermore mght shall be cleaning up aged keys or atmosphere guardrails for AI-generated code, this guide helps your team invent securely from the open up.
Earn the cheat sheet and rob the guesswork out of secrets management.
Recent Posts
- Trump’s FBI says ‘Epstein’ penal advanced postcard to pedophile Larry Nassar is FAKE
- Epstein’s brother’s wild converse that Trump authorized his homicide is unearthed in DOJ files
- Informant steered FBI that Jeffrey Epstein had a ‘non-public hacker’
- Fireblocks CEO says North Korea-linked job recruitment scam centered LinkedIn profiles
- How Criminal Millions Sprinted Via Binance, OKX, and Thoroughly different High Crypto Exchanges
Recent Comments
Categories
Recent Posts





