
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > SmarterMail auth bypass flaw now exploited to hijack admin accounts

Jan
SmarterMail auth bypass flaw now exploited to hijack admin accounts
Scam detection

Hackers started exploiting an authentication bypass vulnerability in SmarterTools’ SmarterMail e-mail server and collaboration tool that permits resetting admin passwords.
An authentication bypass vulnerability in SmarterTools SmarterMail, which permits unauthenticated attackers to reset the machine administrator password and to find elephantine privileges, is now actively exploited within the wild.
The grief resides within the force-reset-password API endpoint, which is deliberately uncovered without authentication.
Researchers at cybersecurity company watchTowr reported the grief on January 8, and SmarterMail launched a repair on January 15 without an identifier being assigned.
After the grief used to be addressed, the researchers stumbled on evidence that threat actors began to put it to use right two days later. This means that hackers reverse-engineered the patch and stumbled on a skill to leverage the flaw.
SmarterMail is a self-hosted Dwelling windows e-mail server and collaboration platform developed by SmarterTools that provides SMTP/IMAP/POP e-mail, webmail, calendars, contacts, and in trend groupware points.
It is most ceaselessly susceptible by managed service suppliers (MSPs), small and medium-sized businesses, and web web hosting suppliers offering e-mail products and services. SmarterTools claims that its products possess 15 million users in 120 worldwide locations.
The CVE-less flaw arises from the API endpoint ‘force-reset-password’ accepting attacker-controlled JSON input, including a ‘IsSysAdmin’ bool type property, which, if pickle to ‘right,’ forces the backend to type the machine administrator password reset common sense.
Then one more time, the mechanism doesn’t to find any security controls or check the aged password, despite the ‘OldPassword’ arena being repeat within the count on, watchTowr researchers stumbled on.
As a outcome, someone who knows or guesses an admin username could presumably presumably even pickle a brand modern password and hijack the narrative.
The researchers repeat that the flaw impacts most challenging admin-level accounts, no longer in trend users.
With admin-level to find entry to, attackers can slither OS commands, thus getting elephantine faraway code execution on the host.
watchTowr researchers possess created a proof-of-understanding exploit that demonstrates SYSTEM-level shell to find entry to.
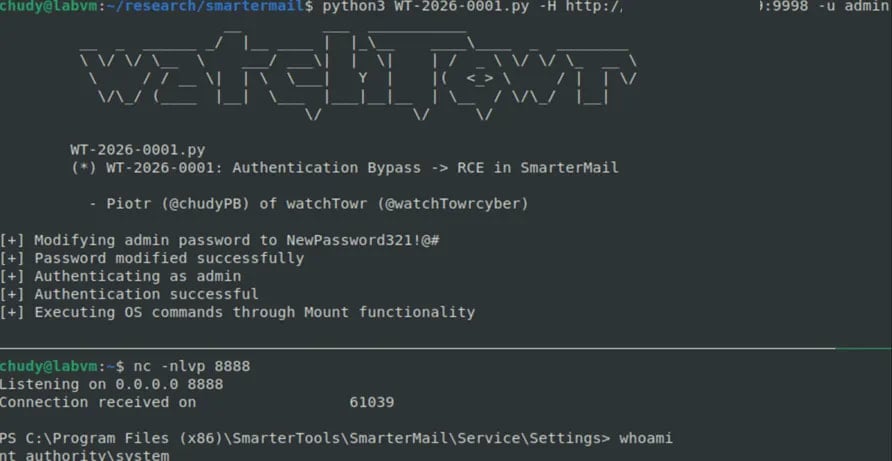
Source: watchTowr
The researchers learned that the vulnerability used to be being exploited within the wild from an anonymous user, who said that somebody used to be resetting administrator passwords.
To support their claims, the tipster pointed watchTowr researchers to a forum post describing a identical say.
Examining the shared logs published that these assaults targeted the ‘force-reset-password’ endpoint, supporting the conclusion that the grief is within the intervening time under active exploitation.
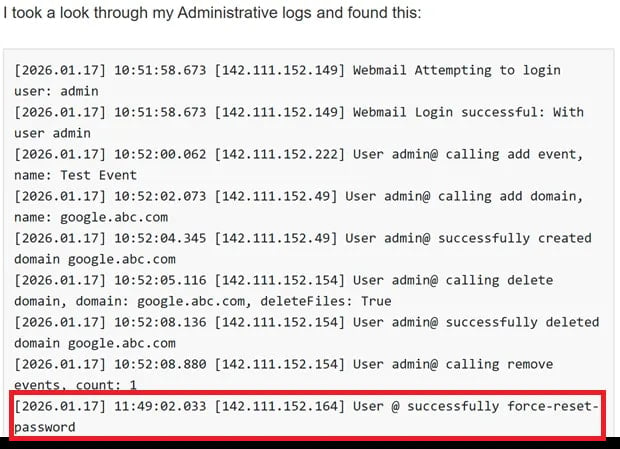
Source: watchTowr
Two weeks earlier, watchTowr stumbled on a serious pre-auth RCE flaw in SmarterMail, tracked as CVE-2025-52691, which led to the discovery of the latest grief.
Users of SmarterMail are suggested to upgrade to the latest version of the utility, Blueprint 9511, launched on January 15, that addresses both points.
Update 1/23 – The vulnerability has got the identifier CVE-2026-23760, rated “critical” (CVSS to find: 9.3).
Additionally, Huntress researchers possess also published a narrative with their observations on the in-the-wild exploitation exercise.
Scam detection The 2026 CISO Funds Benchmark
It be funds season! Over 300 CISOs and security leaders possess shared how they’re planning, spending, and prioritizing for the year forward. This narrative compiles their insights, allowing readers to benchmark systems, title rising trends, and compare their priorities as they head into 2026.
Learn the formula high leaders are turning investment into measurable affect.
Recent Posts
- Trump’s FBI says ‘Epstein’ penal advanced postcard to pedophile Larry Nassar is FAKE
- Epstein’s brother’s wild converse that Trump authorized his homicide is unearthed in DOJ files
- Informant steered FBI that Jeffrey Epstein had a ‘non-public hacker’
- Fireblocks CEO says North Korea-linked job recruitment scam centered LinkedIn profiles
- How Criminal Millions Sprinted Via Binance, OKX, and Thoroughly different High Crypto Exchanges
Recent Comments
Categories
Recent Posts





