
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > ACF plugin bug affords hackers admin on 50,000 WordPress internet sites

Jan
ACF plugin bug affords hackers admin on 50,000 WordPress internet sites
Private eye

A serious-severity vulnerability in the Developed Custom Fields: Extended (ACF Extended) plugin for WordPress will probably be exploited remotely by unauthenticated attackers to receive administrative permissions.
ACF Extended, for the time being packed with life on 100,000 internet sites, is a specialized plugin that extends the capabilities of the Developed Custom Fields (ACF) plugin with aspects for builders and developed living builders.
The vulnerability, tracked as CVE-2025-14533, will probably be leveraged for admin privileges by abusing the plugin’s ‘Insert Client / Update Client’ agree with action, in versions of ACF Extended 0.9.2.1 and earlier.
The flaw arises from the dearth of enforcement of role restrictions throughout agree with-primarily primarily based mostly user creation or updates, and exploitation works even when role boundaries are appropriately configured in the subject settings.
“In the vulnerable version [of the plugin], there are no restrictions for form fields, so the user’s role can be set arbitrarily, even to ‘administrator’, regardless of the field settings, if there is a role field added to the form,” Wordfence explains.
“As with any privilege escalation vulnerability, this can be used for complete site compromise,” the researchers warn.
Though the consequence from exploiting the flaw is excessive, Wordfence notes that the ache is most productive exploitable on internet sites that explicitly consume a ‘Bag Client’ or ‘Update Client’ agree with with a role subject mapped.
CVE-2025-14533 modified into stumbled on by safety researcher Andrea Bocchetti, who, on December 10, 2025, submitted a anecdote to Wordfence to validate the ache and escalate it to the vendor.
Four days later, the vendor addressed the plot back and released it in ACF Extended model 0.9.2.2.
In accordance with receive stats from wordpress.org, roughly 50,000 users agree with downloaded the plugin since then. Assuming all downloads were for primarily the most accepted model, that leaves roughly an equal number of internet sites uncovered to attacks.
WordPress plugin enumeration exercise
Though no attacks focusing on CVE-2025-14533 agree with been seen yet, a anecdote from threat monitoring company GreyNoise affords huge-scale WordPress plugin reconnaissance exercise aimed at enumerating potentially vulnerable internet sites.
In accordance with GreyNoise, from leisurely October 2025 to mid-January 2026, nearly 1,000 IPs correct via 145 ASNs centered 706 distinct WordPress plugins in over 40,000 queer enumeration events.
The most centered plugins are Post SMTP, Loginizer, LiteSpeed Cache, Online page positioning by Rank Math, Elementor, and Duplicator.
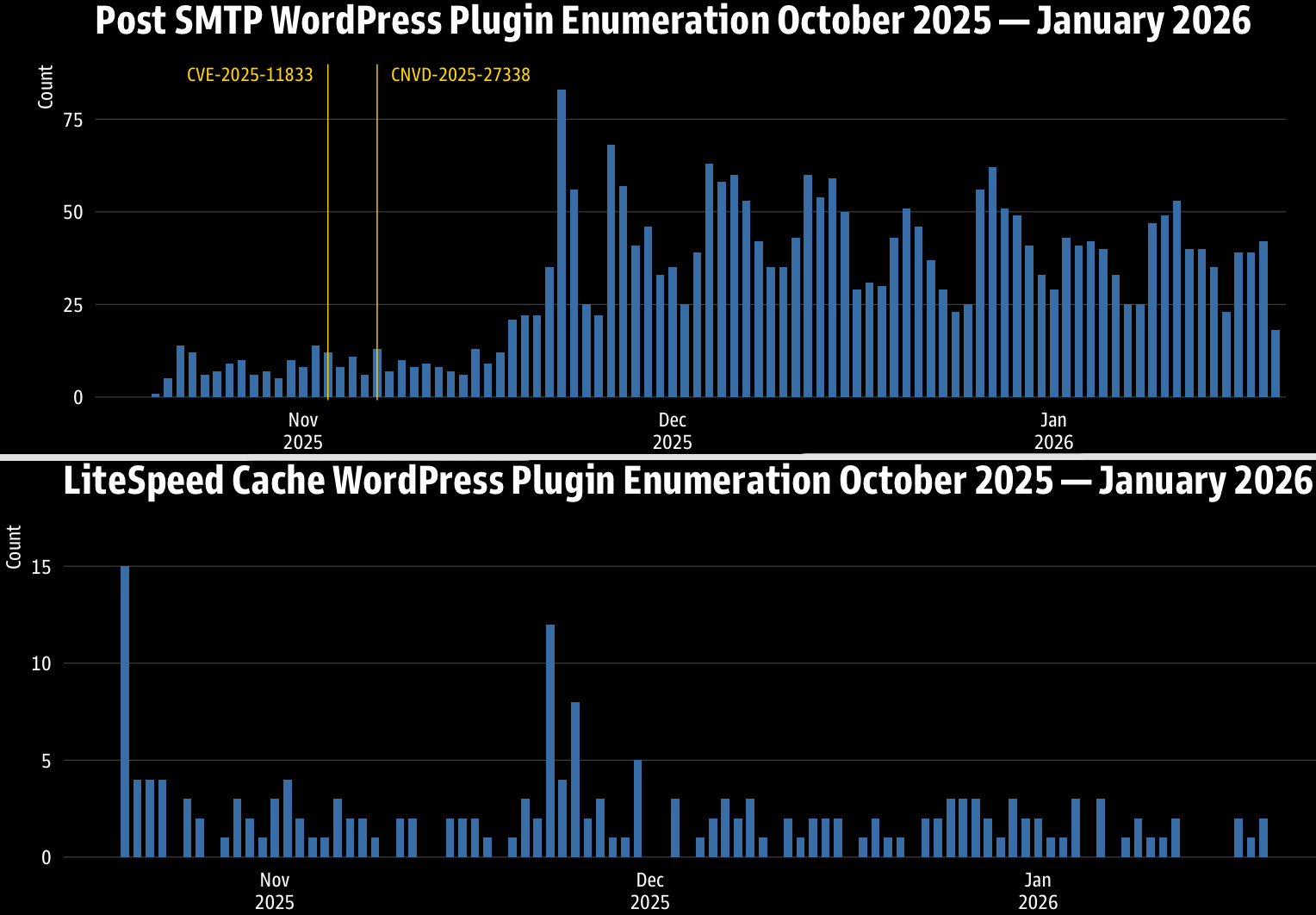
Supply: GreyNoise
Active exploitation of the Post SMTP flaw CVE-2025-11833 modified into reported in early November 2025 by Wordfence, and GreyNoise’s records indicate a centered effort focusing on this flaw animated 91 IPs.
But another flaw GreyNoise suggested admins to patch is CVE-2024-28000, which impacts LiteSpeed Cache and modified into marked as actively exploited by Wordfence in August 2024.
Private eye The 2026 CISO Budget Benchmark
It is budget season! Over 300 CISOs and safety leaders agree with shared how they’re planning, spending, and prioritizing for the one year forward. This anecdote compiles their insights, allowing readers to benchmark strategies, title rising traits, and review their priorities as they head into 2026.
Be taught the device prime leaders are turning investment into measurable impression.
Recent Posts
- Bond Rees Launches Cohabitation Investigation Provider to Reinforce Just and Monetary Cases
- Dwelling Republicans originate push to withhold Clintons in contempt of Congress over Epstein probe
- FBI’s Washington Submit Investigation Reveals How Your Printer Can Snitch on You
- Dignitas publicizes emergency subs following FBI and IgNar visa disorders
- We ran excessive-stage US civil war simulations. Minnesota is exactly how they birth | Claire Finkelstein
Recent Comments
Categories
Recent Posts





