
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Max severity Ni8mare flaw lets hackers hijack n8n servers
Jan
Max severity Ni8mare flaw lets hackers hijack n8n servers
Cybercrime
A maximum severity vulnerability dubbed “Ni8mare” permits a ways-off, unauthenticated attackers to take adjust over within the neighborhood deployed cases of the N8N workflow automation platform.
The safety subject is diagnosed as CVE-2026-21858 and has a 10 out of 10 severity bag. In preserving with researchers at knowledge security company Cyera, there are bigger than 100,000 vulnerable n8n servers.
n8n is an launch-provide workflow automation instrument that enables users to glue applications, APIs, and services into complicated workflows through a visible editor. It’s a ways essentially aged to automate tasks and supports integrations with AI and grand language model (LLM) services.
It has over 50,000 weekly downloads on npm and higher than 100 million pulls on Docker Hub. It’s a ways a trendy instrument within the AI relate, where it’s aged to orchestrate LLM calls, fabricate AI agents and RAG pipelines, and automate knowledge ingestion and retrieval.
Ni8mare predominant points
The Ni8mare vulnerability affords an attacker bag entry to to files on the underlying server by executing certain bag-essentially based workflows.
“A vulnerable workflow could grant access to an unauthenticated remote attacker. This could result in exposure of sensitive information stored on the system and may enable further compromise depending on deployment configuration and workflow usage,” n8n builders direct.
Cyera researchers stumbled on the Ni8mare vulnerability (CVE-2026-21858) and reported it to n8n on November 9, 2025. They direct that the security subject is a bellow material-form confusion within the potential n8n parses knowledge.
n8n uses two solutions to direction of incoming knowledge in step with the ‘bellow material-form’ header configured in a webhook, the element that triggers events in a workflow by listening for explicit messages.
When the webhook inquire is marked as multipart/bag-knowledge, n8n treats it as a file upload and uses a uncommon upload parser that saves files in randomly generated temporary areas.
“This means users can’t control where files end up, which protects against path traversal attacks.”
On the other hand, for all other bellow material styles, n8n uses its typical parser as a replacement.
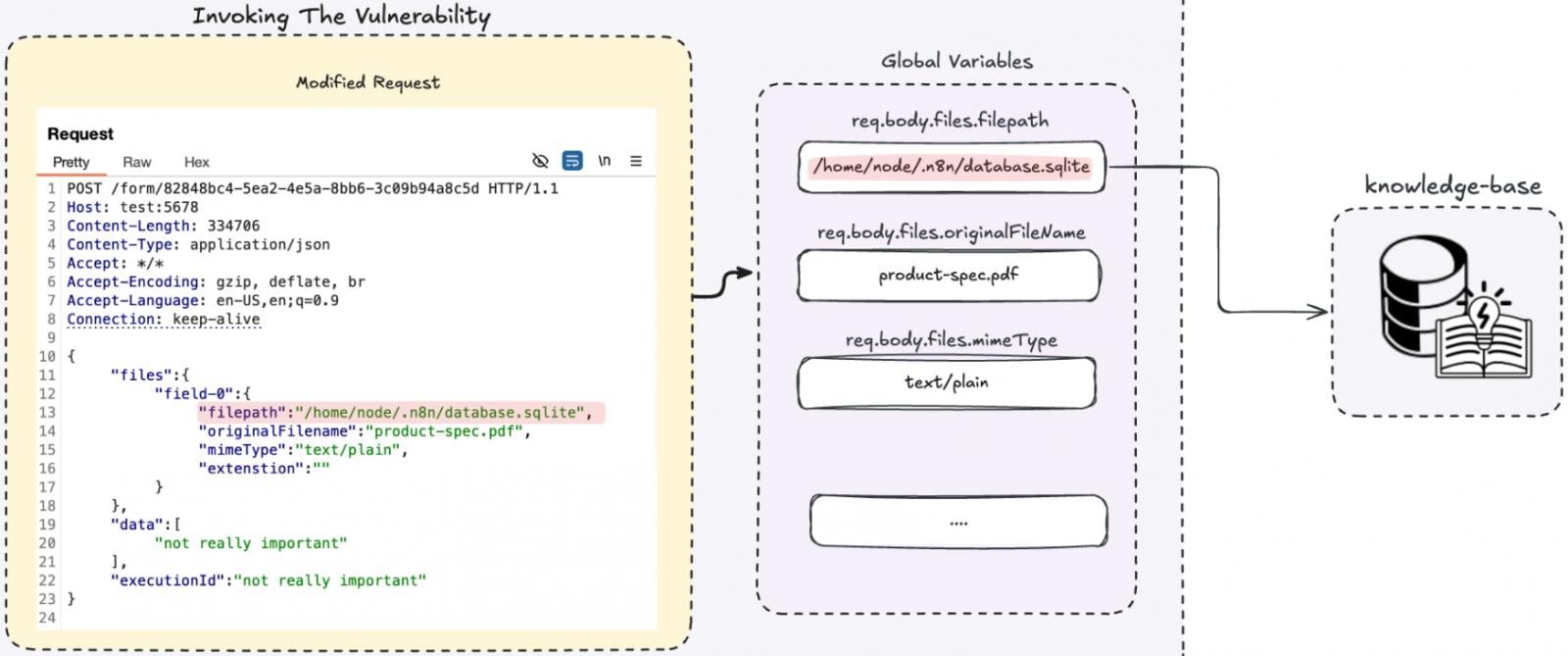
Cyera stumbled on that by surroundings a uncommon bellow material form, honest like utility/json, an attacker can bypass the upload parser.
On this downside, n8n nonetheless processes file-linked fields but does so without verifying that the inquire if truth be told contains a first price file upload. This enables the attacker to fully adjust the file metadata, including the file direction.
.jpg)
Offer: Cyera
“Since this function is called without verifying the content type is multipart/form-data, we control the entire req.body.files object. That means we control the filepath parameter – so instead of copying an uploaded file, we can copy any local file from the system,” explains Cyera.
This enables discovering out arbitrary files from an n8n instance, which is willing to repeat secrets and ways by including inside files into the workflow’s knowledge horrible.
Cyera says this could well well very nicely be abused to repeat secrets and ways kept on the instance, inject nonetheless files into workflows, forge session cookies to bypass authentication, and even enact arbitrary commands.
Offer: Cyera
Cyera emphasizes that n8n normally stores API keys, OAuth tokens, database credentials, cloud storage bag entry to, CI/CD secrets and ways, and industry knowledge, making it a central automation hub.
n8n builders direct that there could be no such thing as a loyal workaround available for Ni8mare, but one mitigation is to restrict or disable publicly accessible webhook and bag endpoints.
The suggested movement is to update to n8n version 1.121.0 or a extra recent one.
Cybercrime Secrets and ways Security Cheat Sheet: From Sprawl to Regulate
Whether or no longer you’re cleaning up vulnerable keys or surroundings guardrails for AI-generated code, this e-book helps your crew fabricate securely from the commence.
Web the cheat sheet and take the guesswork out of secrets and ways management.
Recent Posts
- Bond Rees Launches Cohabitation Investigation Provider to Reinforce Just and Monetary Cases
- Dwelling Republicans originate push to withhold Clintons in contempt of Congress over Epstein probe
- FBI’s Washington Submit Investigation Reveals How Your Printer Can Snitch on You
- Dignitas publicizes emergency subs following FBI and IgNar visa disorders
- We ran excessive-stage US civil war simulations. Minnesota is exactly how they birth | Claire Finkelstein
Recent Comments
Categories
Recent Posts





