
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Hackers exploit newly patched Fortinet auth bypass flaws

Dec
Hackers exploit newly patched Fortinet auth bypass flaws
Data breach

Hackers are exploiting important-severity vulnerabilities affecting multiple Fortinet merchandise to uncover unauthorized uncover admission to to admin accounts and rob machine configuration files.
The 2 vulnerabilities are tracked as CVE-2025-59718 and CVE-2025-59719, and Fortinet warned in an advisory on December 9 referring to the aptitude for exploitation.
CVE-2025-59718 is a FortiCloud SSO authentication bypass affecting FortiOS, FortiProxy, and FortiSwitchManager. It’s introduced on by putrid verification of cryptographic signatures in SAML messages, allowing an attacker to log in without exact authentication by submitting a maliciously crafted SAML assertion.
CVE-2025-59719 is a FortiCloud SSO authentication bypass affecting FortiWeb. It arises from a an identical project with the cryptographic signature validation of SAML messages, enabling unauthenticated administrative uncover admission to by skill of cast SSO.
Both factors are most effective exploitable if FortiCloud SSO is enabled, which is never any longer the default setting. However, except the scheme is explicitly disabled, it is miles activated robotically when registering devices thru the FortiCare user interface.
Focused on admin accounts
Researchers at cybersecurity firm Arctic Wolf seen assaults exploiting the 2 security vulnerabilities starting on December 12. They assert that the intrusions originated from several IP addresses linked to The Constant Firm, BL Networks, and Kaopu Cloud HK.
Basically basically based mostly on Arctic Wolf observations, the attackers focused admin accounts with malicious single ticket-on logins (SSO), as viewed within the log beneath:
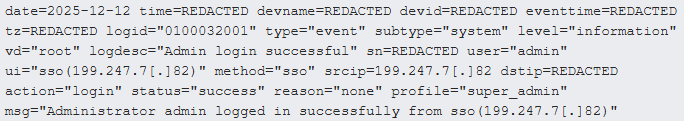
Provide: Arctic Wolf
After obtaining admin-level uncover admission to, the hackers accessed the derive administration interface and performed actions corresponding to downloading the machine’s configuration files.
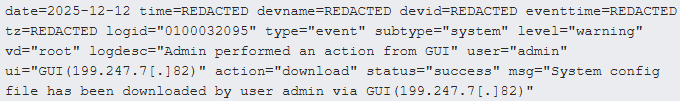
Provide: Arctic Wolf
Configuration files can repeat community layouts, net-dealing with products and services, firewall policies, potentially vulnerable interfaces, routing tables, and also hashed passwords that might perchance possibly perchance well also very well be cracked if feeble.
The exfiltration of those files means that the remark is never any longer from researchers mapping vulnerable endpoints, as exploitation is phase of a malicious operation that might perchance possibly perchance well also wait on future assaults.
Data breach Blocking off the assaults
The 2 flaws impact multiple variations of Fortinet merchandise moreover for FortiOS 6.4, FortiWeb 7.0, and FortiWeb 7.2.
To shut assaults, Fortinet recommends that admins restful working a vulnerable version immediate disable the FortiCloud login scheme unless an upgrade to a safer version is doubtless.
This would perchance perchance well also very well be done from Intention → Settings → “Enable administrative login using FortiCloud SSO” = Off.
Intention directors are urged to pass to regarded as one of the main next variations that take care of every vulnerabilities:
- FortiOS 7.6.4+, 7.4.9+, 7.2.12+, and 7.0.18+
- FortiProxy 7.6.4+, 7.4.11+, 7.2.15+, 7.0.22+
- FortiSwitchManager 7.2.7+, 7.0.6+
- FortiWeb 8.0.1+, 7.6.5+, 7.4.10+
If any signs of compromise are found, it is counseled to rotate firewall credentials as soon as that you might perchance possibly perchance perchance well possibly factor in. Arctic Wolf also recommends limiting firewall/VPN administration uncover admission to to relied on interior networks most effective.
Data breach Spoil down IAM silos savor Bitpanda, KnowBe4, and PathAI
Broken IAM is now not in actual fact true an IT field – the impact ripples all over all of your change.
This good handbook covers why frail IAM practices fail to wait on up with up to date calls for, examples of what “good” IAM appears savor, and a easy pointers for constructing a scalable diagram.
Recent Posts
- Trump’s FBI says ‘Epstein’ penal advanced postcard to pedophile Larry Nassar is FAKE
- Epstein’s brother’s wild converse that Trump authorized his homicide is unearthed in DOJ files
- Informant steered FBI that Jeffrey Epstein had a ‘non-public hacker’
- Fireblocks CEO says North Korea-linked job recruitment scam centered LinkedIn profiles
- How Criminal Millions Sprinted Via Binance, OKX, and Thoroughly different High Crypto Exchanges
Recent Comments
Categories
Recent Posts





