
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Scattered Spider is running a VMware ESXi hacking spree

Jul
Scattered Spider is running a VMware ESXi hacking spree
Internet investigation

Scattered Spider hackers had been aggressively focusing on virtualized environments by attacking VMware ESXi hypervisors at U.S. companies in the retail, airline, transportation, and insurance sectors.
Per the Google Threat Intelligence Neighborhood (GITG), the attackers lend a hand the utilization of their long-established ways that form no longer comprise vulnerability exploits however count on completely accomplished social engineering “to bypass even mature security programs.”
A Scattered Spider attack
The researchers recount that the gang starts an attack by impersonating an worker in a name to the IT lend a hand desk. The risk actor’s motive is to persuade the agent to swap the worker’s Active Listing password and thus set preliminary access.
This allows Scattered Spider to scan the community gadgets for IT documentation that can maybe well provide high-cost targets, fancy the names of domain or VMware vSphere administrators, and security groups that can provide administrative permissions over the digital ambiance.
At the identical time, they scan for privileged access administration (PAM) solutions that can maybe well moreover lend a hand sensitive data in point of fact helpful for shifting to purposeful community resources.
“Armed with the name of a specific, high-value administrator, they make additional calls to the help desk. This time, they impersonate the privileged user and request a password reset, allowing them to seize control of a privileged account” – Google Threat Intelligence Neighborhood
The hackers then work their technique to set access to the firm’s VMware vCenter Server Appliance (vCSA) – a digital machine that enables managing VMware vSphere environments, which includes the ESXi hypervisor for managing your total digital machines on a physical server.
This stage of access permits them to enable SSH connections on ESXi hosts and reset the inspiration passwords. Extra, they stop a so-known as “disk-swap” attack to extract the severe NTDS.dit database for the Active Listing.
A disk-swap attack occurs when the risk actors powers off a Domain Controller digital machine (VM) and dettaches its digital disk most effective to join it to but another, unmonitored VM they alter. After copying the sensitive data (e.g NTDS.dit file), they revert the technique and vitality on the domain controller machine.
It’s mandatory to show that the stage of alter Scattered Spider obtains on the digital infrastructure permits them to manage every resources on hand, including the backup machines, that are wiped of backup jobs, snaphots, and repositories.
In the remaining share of the attack Scattered Spider leverages their SSH access to lift and deploy ransomware binaries to encrypt all VM data detected in the datastores.
Per their observations, GTIG researchers recount that a Scattered Spider attack has five clear phases that allow hackers to toddle from low-stage access to taking whole alter over the hypervisor.
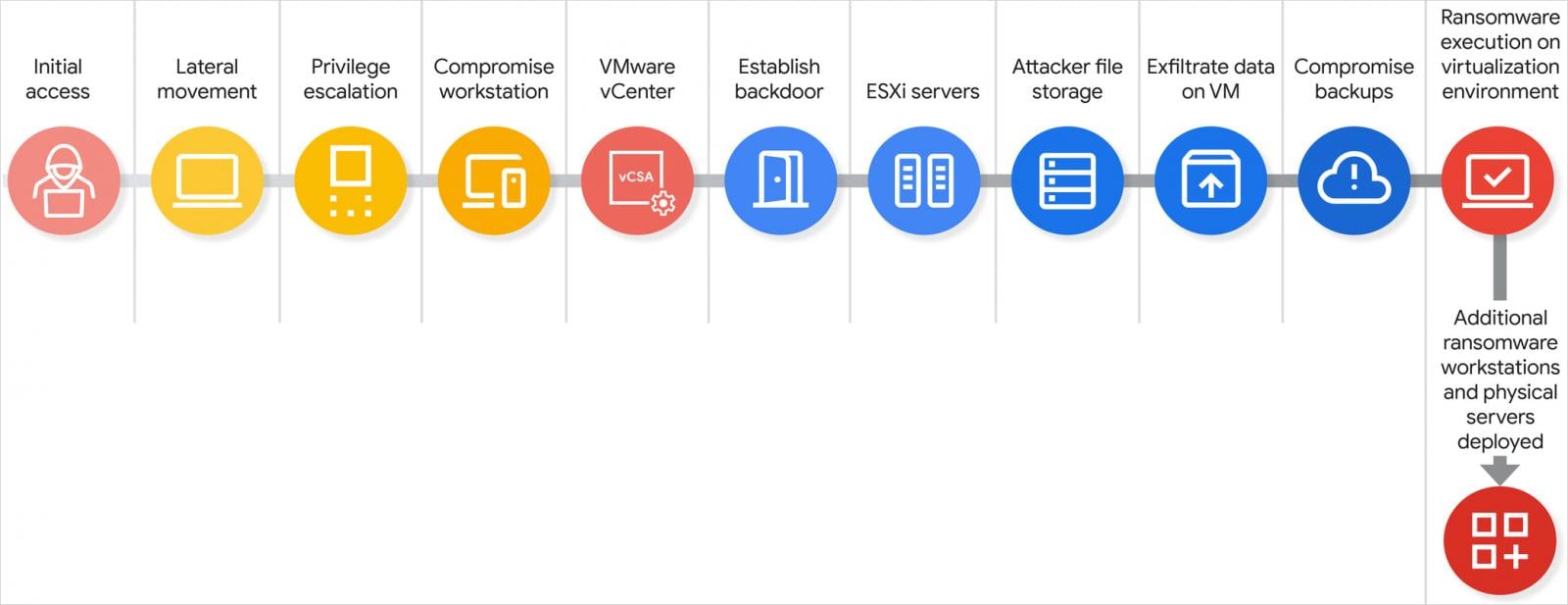
Offer: Google
A Scattered Spider attack chain, whole from preliminary access to data exfiltration and ransomware deployment, may per chance maybe well moreover happen in lawful about a hours.
Even without exploiting any tool vulnerabilities, the risk actor manages to set “an unparalleled stage of alter over a whole virtualized ambiance, allowing them to bypass many old in-guest security controls,” a Google consultant quick BleepingComputer.
While focusing on ESXi hypervisors will not be any longer new (considered in Scattered Spider high-profile breaches fancy the 2023 MGM Motels attack) GTIG notes that they’re seeing extra ransomware groups adopting this tactic and search data from the topic to grow.
One reason in the lend a hand of this may per chance be that adversaries comprise noticed that VMware infrastructure is typically poorly understood by organizations and, in consequence, no longer as robustly defended.
To lend a hand organizations supply protection to against these attacks, Google published a technical put up describing the stages of a Scattered Spider attack, explaining why it’s efficient, and providing actions that a firm can elevate to detect the breach at an earlier share.
The proposed measures may per chance maybe also be summarized in three predominant pillars:
- Lock down vSphere with execInstalledOnly, VM encryption, and disabled SSH. Steer optimistic of disclose AD joins on ESXi, delete orphaned VMs, and build in force strict MFA and access insurance policies. Continuously video show for config drift.
- Instruct phishing-resistant MFA all the draw in which thru VPN, AD, and vCenter. Isolate Tier 0 resources (DCs, backups, PAM) and steer optimistic of web web hosting them on the identical infrastructure they valid. Assign in thoughts separate cloud IdPs to crash AD dependency.
- Centralize logs in a SIEM and alert on key behaviors, similar to admin neighborhood adjustments, vCenter logins, and SSH enablement. Instruct immutable, air-gapped backups and test restoration against hypervisor-layer attacks.
Scattered Spider (moreover acknowledged as UNC3944, Octo Tempest, 0ktapus) is a financially motivated risk neighborhood specialized in social engineering to a stage that it’ll impersonate firm workers the utilization of the valid vocabulary and accent.
It has lately upped its process with attacks on colossal UK retail companies, airline and transportation entities, and insurance companies.
Even supposing the UK’s Nationwide Crime Company arrested four suspected participants of the neighborhood, the malicious process, originating from varied clusters, has no longer subsided.
Internet investigation The Board Yarn Deck CISOs In actual fact Instruct
CISOs know that getting board aquire-in starts with a favorable, strategic gape of how cloud security drives swap cost.
This free, editable board file deck helps security leaders show risk, affect, and priorities in optimistic swap terms. Flip security updates into foremost conversations and quicker determination-making in the boardroom.
Recent Posts
- Broker who supplied malware to the FBI space for sentencing
- High college senior going through extra than 300 prison fees in alleged sextortion map focusing on minors: reports
- 12 Delivery air Energy Tools You Can also objective accrued Appreciate In Your Garage Sooner than Spring Will get Right here
- How the FBI tracked down a Maryland man allegedly in the support of a secret-filming YouTube channel
- Hackers Raise The Fear About Discord’s Most recent Age-Verification Accomplice



