
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Bluetooth flaws would possibly perchance perchance let hackers place confidence in by your microphone

Jun
Bluetooth flaws would possibly perchance perchance let hackers place confidence in by your microphone
Internet investigation

Vulnerabilities affecting a Bluetooth chipset contemporary in greater than two dozen audio devices from ten vendors would possibly perchance perchance even be exploited for eavesdropping or stealing unruffled knowledge.
Researchers confirmed that 29 devices from Beyerdynamic, Bose, Sony, Marshall, Jabra, JBL, Jlab, EarisMax, MoerLabs, and Teufel are affected.
The listing of impacted products contains audio system, earbuds, headphones, and wireless microphones.
The security complications would be leveraged to take over a weak product and on some telephones, an attacker within connection vary would be ready to extract name historical previous and contacts.
Snooping over a Bluetooth connection
At the TROOPERS security convention in Germany, researchers at cybersecurity company ERNW disclosed three vulnerabilities within the Airoha methods on a chip (SoCs), that are widely musty in Correct Wireless Stereo (TWS) earbuds.
The factors will no longer be serious and besides end bodily proximity (Bluetooth vary), their exploitation also requires “a excessive technical skill space.” They got the next identifiers:
- CVE-2025-20700 (6.7, medium severity ranking) – missing authentication for GATT products and services
- CVE-2025-20701 (6.7, medium severity ranking) – missing authentication for Bluetooth BR/EDR
- CVE-2025-20702 (7.5, excessive severity ranking) – serious capabilities of a personalized protocol
ERNW researchers issue they created a proof-of-opinion exploit code that allowed them to read the currently playing media from the centered headphones.
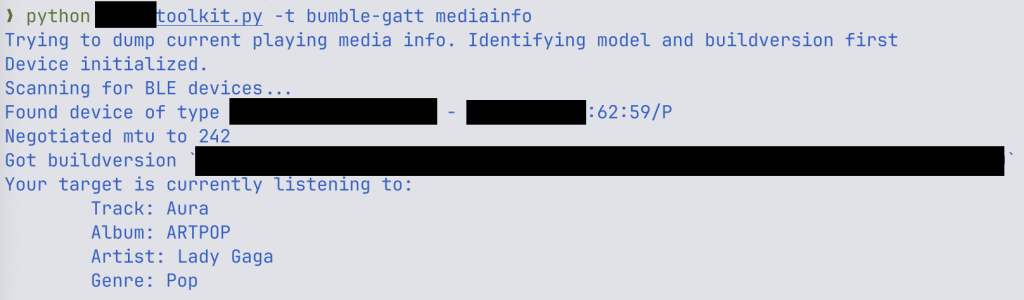
provide: ERWN
Whereas such an attack would possibly perchance perchance no longer contemporary a gigantic danger, other eventualities leveraging the three bugs would possibly perchance perchance let a risk actor hijack the connection between the cell cell phone and an audio Bluetooth tool and exhaust the Bluetooth Arms-Free Profile (HFP) to effort instructions to the cell phone.
“The vary of available instructions is dependent upon the cell working machine, but all main platforms fortify on the least initiating and receiving calls” – ERNW
The researchers accept as true with been ready to trigger a name to an arbitrary number by extracting the Bluetooth link keys from a weak tool’s memory.
They issue that searching on the cell phone’s configuration, an attacker would possibly perchance perchance also retrieve the name historical previous and contacts.
They accept as true with been also ready to initiate a name and “successfully eavesdrop on conversations or sounds within earshot of the phone.”
Furthermore, the weak tool’s firmware would possibly perchance perchance potentially be rewritten to enable faraway code execution, thereby facilitating the deployment of a wormable exploit succesful of propagating across more than one devices.
Attack restrictions put collectively
Even supposing the ERNW researchers contemporary excessive attack eventualities, radiant implementation at scale is constrained by particular boundaries.
“Yes — the root that any individual would possibly perchance perchance hijack your headphones, impersonate them in direction of your cell phone, and potentially originate calls or place confidence in on you, sounds ravishing alarming.”
“Yes — technically, it’s far excessive,” the researchers issue, adding that “precise attacks are complex to originate.”
The necessity of both technical sophistication and bodily proximity confines these attacks to excessive-mark targets, much like these in diplomacy, journalism, activism, or unruffled industries.
Airoha has released an updated SDK incorporating necessary mitigations, and tool manufacturers accept as true with started patch constructing and distribution.
Nonetheless, German e-newsletter Heise says that primarily the most most up-to-date firmware updates for greater than half of of the affected devices are from Might well 27 or earlier, which is sooner than Airoha delivered the updated SDK to its customers.
Internet investigation Why IT teams are ditching manual patch management
Patching musty to indicate complex scripts, lengthy hours, and never-ending fire drills. No longer anymore.
On this novel recordsdata, Tines breaks down how smartly-liked IT orgs are leveling up with automation. Patch sooner, scale back overhead, and center of attention on strategic work — no complex scripts required.
Recent Posts
- Broker who supplied malware to the FBI space for sentencing
- High college senior going through extra than 300 prison fees in alleged sextortion map focusing on minors: reports
- 12 Delivery air Energy Tools You Can also objective accrued Appreciate In Your Garage Sooner than Spring Will get Right here
- How the FBI tracked down a Maryland man allegedly in the support of a secret-filming YouTube channel
- Hackers Raise The Fear About Discord’s Most recent Age-Verification Accomplice



