
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Hackers abuse Microsoft ClickOnce and AWS services for stealthy assaults

Jun
Hackers abuse Microsoft ClickOnce and AWS services for stealthy assaults
Internet investigation

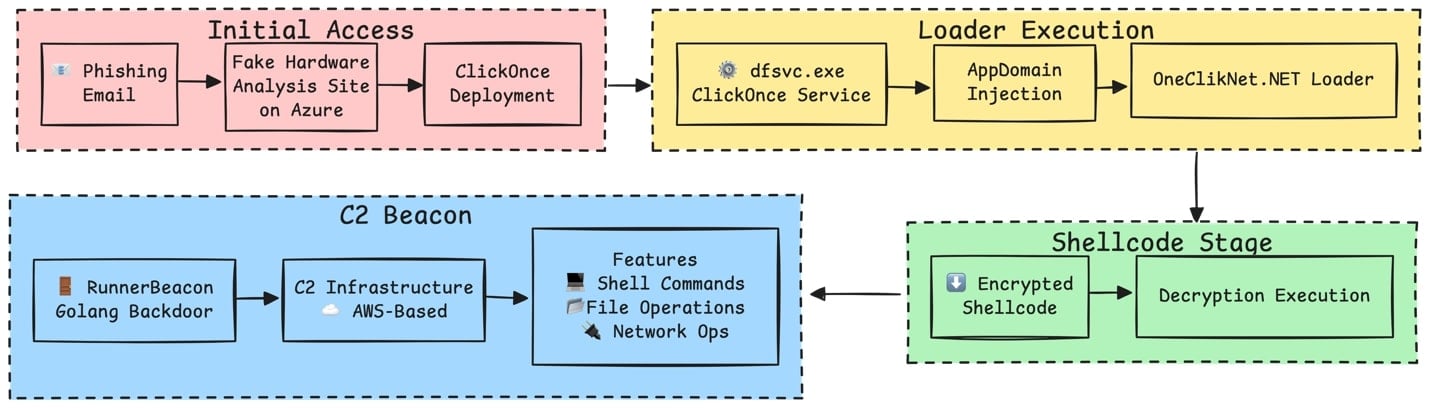
A worldly malicious advertising campaign that researchers name OneClik has been leveraging Microsoft’s ClickOnce instrument deployment system and custom Golang backdoors to compromise organizations for the duration of the vitality, oil, and gas sectors.
The hackers depend on legitimate AWS cloud services (AWS, Cloudfront, API Gateway, Lambda) to abet the state and abet an eye on (C2) infrastructure hidden.
ClickOnce is a deployment technology from Microsoft that enables developers to fabricate self-updating Dwelling windows-primarily based completely mostly capabilities, reducing particular person interaction to a minimum.
Safety researchers at cybersecurity firm Trellix analyzed three variants of the advertising campaign (v1a, BPI-MDM, and v1d), all of them deploying “a stylish Golanguage backdoor” called RunnerBeacon by the usage of a .NET-primarily based completely mostly loader tracked as OneClikNet.
In step with them, every model of the OneClik advertising campaign evolved with superior ways and C2 obfuscation, strong anti-diagnosis, and sandbox evasion tactics.
Whereas operational indicators mark China-affiliated risk actors, the researchers are cautious in making an attribution.
Abusing Microsoft’s ClickOnce deployment system
OneClik assaults combine legitimate tools with custom malware and cloud and venture tooling, which permits the risk actor to evade detection of the operation.
It begins with a phishing electronic mail with a link to a unsuitable hardware diagnosis place of residing hosted in the Azure ecosystem that delivers a .APPLICATION file (ClickOnce manifest) disguised as a legitimate system.
Trellix researchers converse that the attacker extinct ClickOnce apps as a shipping mechanism for malicious payloads with out triggering the actual person story abet an eye on mechanism.
“ClickOnce apps launch below the Deployment Carrier (dfsvc.exe), enabling attackers to proxy execution of malicious payloads by this depended on host.
Because ClickOnce capabilities scoot with particular person-stage privileges (no particular person story abet an eye on required), they offer an though-provoking shipping mechanism for risk actors aiming to book clear of privilege escalation,” the researchers present.
offer: Trellix
After execution, the ClickOnce loader runs malicious payloads by hijacking how the .NET application loads assemblies, a map called AppDomainManager injection.
In the case of OneClik, this allowed the risk actor to use a legitimate .NET executable, much like ZSATray.exe, umt.exe, or ied.exe, to load one thing else than the favored dependencies.
“With the loader in place of residing, payload execution proceeds below dfsvc.exe, mixing with benign ClickOnce activities,” Trellix researchers converse.
To veil the operation for a long length, the risk actor leveraged legitimate AWS services, which made C2 communication seem as popular cloud usage as it blended with risk free CDN web site traffic.
In the OneClik v1a variant, the beacon contacted a Cloudfront distribution area and an API Gateway endpoint. In the v1d it extinct an AWS Lambda aim URL because the HTTP callback tackle.
“By “hiding in the cloud,” attackers exploit the high believe and availability of AWS: defenders must decrypt SSL or denylist complete AWS domains to undercover agent this web site traffic, which is in overall impractical,” Trellix researchers give an explanation for.
Go-primarily based completely mostly RunnerBeacon backdoor
An diagnosis of the Golang-primarily based completely mostly RunnerBeacon backdoor showed that its C2 protocol encrypted all web site traffic using the RC4 ride cipher algorithm and serialized records using MessagePack.
It components a modular message protocol with extra than one message forms, among them BeaconData, FileRequest, CommandRequest, SOCKSRequest, and FileUpload.
One of the predominant programs the backdoor makes use of to hinder diagnosis, the researchers found an “obfuscate_and_sleep” routine and randomized “jitter” in beacon intervals.
The researchers additionally noticed high-stage commands that allow the risk actor to:
- create shell commands (CreateProcessW)
- numerate processes
- scoot file operations (directory checklist, add, download)
- create network-linked responsibilities (port scanning)
- place a SOCKS5 tunnel to proxy records web site traffic
Extra RunnerBeacon capabilities embody superior operations like direction of injection and environment the stage for privilege escalation.
Trellix says that RunnerBeacon’s form is analogous to known Go-primarily based completely mostly Cobalt Strike beacons like these in the Geacon family.
Attributable to the similarities in the keep of commands and the usage of substandard-protocol C2, they are saying that “RunnerBeacon might possibly possibly properly be an evolved fork or privately modified variant of Geacon, tailored for stealthier, and cloud-pleasant operations”
Cautious attribution
Although the OneClik advertising campaign modified into once found now not too long in the past, at the starting of March, a variant of the RunnerBeacon loader modified into once identified in September 2023 at a firm in the Center East in the oil and gas sector.
The shipping map might possibly possibly now not make certain nonetheless the variant’s code is virtually a much like the analyzed module from the OneClik operation.
The clues pointing to exercise linked to a China-affiliated speak actor embody ways, tactics, and procedures viewed in other campaigns attributed to Chinese language risk actors.
Trellix highlights that the .NET AppDomainManager injection map has been extinct in extra than one cyberattacks attributed to Chinese language risk actors. The an analogous goes for the map extinct to deploy the encrypted payload.
Additionally, outdated China-linked campaigns level to a preference for cloud-primarily based completely mostly staging using services from Alibaba and Amazon.
Nonetheless, these overlaps are now not ample to attribute the OneClik assaults to a selected risk actor.
The picture from Trellix choices a comprehensive checklist of indicators of compromise for all components in the OneClik advertising campaign, ranging from phishing lures and malware loaders to configuration information, backdoor binaries, legitimate executables, domains, and configuration parameters.
Internet investigation Why IT groups are ditching book patch administration
Patching extinct to mean advanced scripts, long hours, and diverse fire drills. Now not anymore.
In this original book, Tines breaks down how popular IT orgs are leveling up with automation. Patch sooner, decrease overhead, and level of curiosity on strategic work — no advanced scripts required.
Recent Posts
- Bond Rees Launches Cohabitation Investigation Provider to Reinforce Just and Monetary Cases
- Dwelling Republicans originate push to withhold Clintons in contempt of Congress over Epstein probe
- FBI’s Washington Submit Investigation Reveals How Your Printer Can Snitch on You
- Dignitas publicizes emergency subs following FBI and IgNar visa disorders
- We ran excessive-stage US civil war simulations. Minnesota is exactly how they birth | Claire Finkelstein
Recent Comments
Categories
Recent Posts




