
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > APT28 hackers employ Label chats to beginning out novel malware assaults on Ukraine

Jun
APT28 hackers employ Label chats to beginning out novel malware assaults on Ukraine
Private eye

The Russian voice-subsidized threat group APT28 is the employ of Label chats to goal govt targets in Ukraine with two previously undocumented malware families named BeardShell and SlimAgent.
To be particular, here is now now not a safety challenge in Label. As an different, threat actors are extra recurrently the employ of the messaging platform as portion of their phishing assaults because of its increased usage by governments worldwide.
The assaults were first found by Ukraine’s Computer and Emergency Response (CERT-UA) in March 2024, even supposing exiguous facts concerning the infection vector were uncovered at the time.
Over a year later, in Also can 2025, ESET notified CERT-UA of unauthorized uncover admission to to a gov.ua electronic mail account, prompting a novel incident response.
At some stage on this novel investigation, CERT-UA found that messages sent by procedure of the encrypted messenger app Label were used to suppose a malicious chronicle to targets (Акт.doc), which makes employ of macros to load a memory-resident backdoor called Covenant.
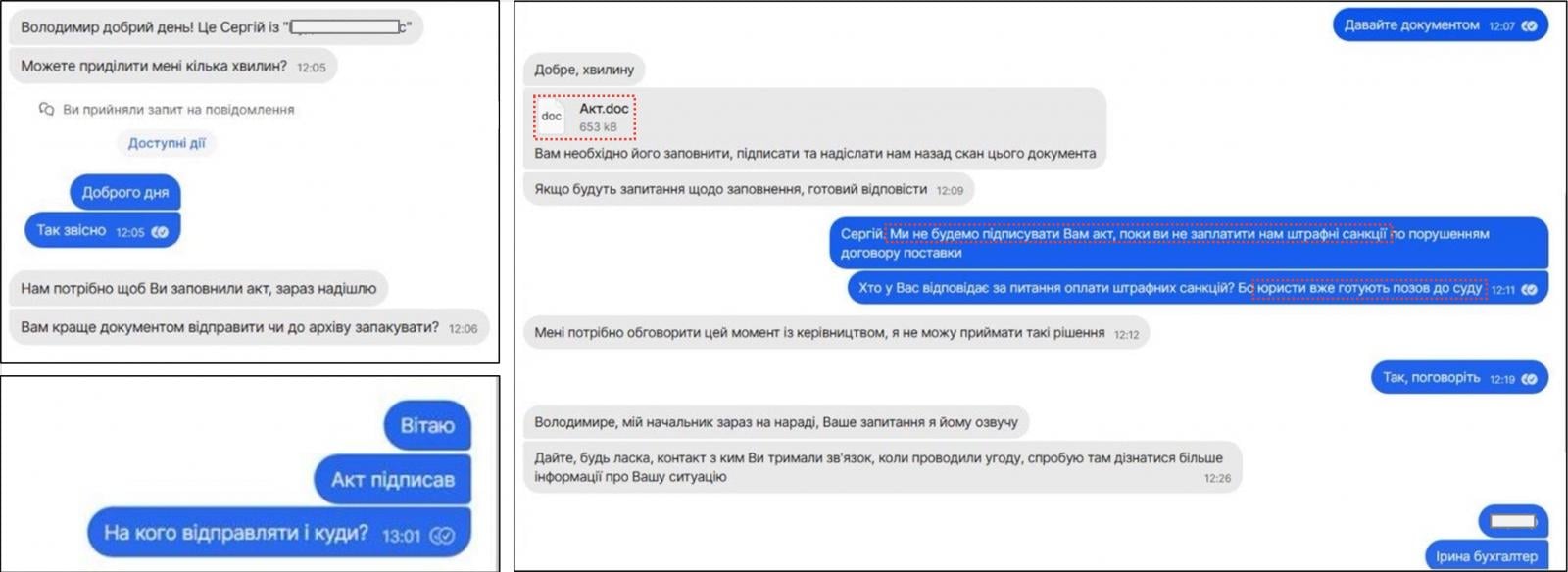
Supply: CERT-UA
Covenant acts as a malware loader, downloading a DLL (PlaySndSrv.dll) and a shellcode-ridden WAV file (pattern-03.wav) that hundreds BeardShell, a previously undocumented C++ malware.
For every the loader and the predominant malware payload, persistence is secured by procedure of COM-hijacking in the Dwelling windows registry.
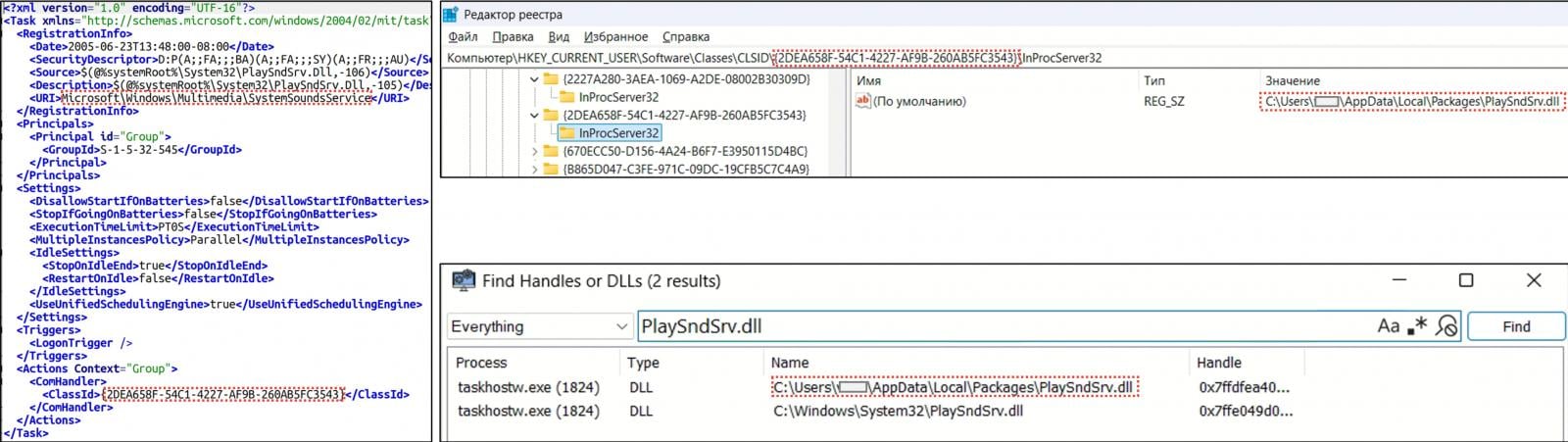
Supply: CERT-UA
BeardShell’s predominant performance is to download PowerShell scripts, decrypt them the employ of ‘chacha20-poly1305’, and enact them. The execution results are exfiltrated to the show-and-motivate a watch on (C2) server, the communication with which is facilitated by Icedrive API.
In the 2024 assaults, CERT-UA moreover spotted a screenshot grabber named SlimAgent, which captures screenshots the employ of an array of Dwelling windows API capabilities (EnumDisplayMonitors, CreateCompatibleDC, CreateCompatibleBitmap, BitBlt, GdipSaveImageToStream).
These photos are encrypted the employ of AES and RSA, and saved regionally, presumably to be exfiltrated by a separate payload/instrument to APT28’s C2 server.
CERT-UA attributes this advise to APT28, which they display screen as UAC-0001, and recommends that most likely targets video show network interactions with app.koofr.derive and api.icedrive.derive.
APT28 has a lengthy historical past of targeting Ukraine to boot to diversified key organizations in the U.S. and Europe, basically for cyberespionage.
They’re belief to be one of Russia’s most superior threat groups, exposed by Volexity in November 2024 for the employ of a novel “nearest neighbor” methodology, which remotely breached targets by exploiting nearby Wi-Fi networks.
In 2025, Label grew to radically change central to cyberattacks linked to Russia and Ukraine.
The favored communications platform has been abused in spear-phishing assaults that abused the platform’s tool-linking characteristic to hijack accounts and in Darkish Crystal RAT distribution towards key targets in Ukraine.
At some level, representatives of Ukraine’s govt expressed disappointment that Label allegedly stopped participating with them in their effort to dam Russian assaults. Ukrainian officials later voiced frustration over Label’s lack of cooperation in blockading Russian operations.
However, Label president Meredith Whittaker met that claim with surprise, asserting the platform has never shared communication recordsdata with Ukraine or any diversified govt.
Private eye Why IT groups are ditching manual patch management
Patching used to imply advanced scripts, lengthy hours, and never-ending fire drills. No longer anymore.
In this novel recordsdata, Tines breaks down how contemporary IT orgs are leveling up with automation. Patch faster, minimize overhead, and middle of attention on strategic work — no advanced scripts required.
Recent Posts
- Broker who supplied malware to the FBI space for sentencing
- High college senior going through extra than 300 prison fees in alleged sextortion map focusing on minors: reports
- 12 Delivery air Energy Tools You Can also objective accrued Appreciate In Your Garage Sooner than Spring Will get Right here
- How the FBI tracked down a Maryland man allegedly in the support of a secret-filming YouTube channel
- Hackers Raise The Fear About Discord’s Most recent Age-Verification Accomplice



