
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Scania confirms insurance claim knowledge breach in extortion are trying

Jun
Scania confirms insurance claim knowledge breach in extortion are trying
Private investigator

Car broad Scania confirmed it suffered a cybersecurity incident the build likelihood actors feeble compromised credentials to breach its Monetary Services systems and map shut insurance claim paperwork.
Scania told BleepingComputer that the attackers emailed several Scania workers, threatening to leak the strategies online unless their demands had been met.
Scania is a serious Swedish manufacturer of heavy trucks, buses, and industrial and marine engines and is a member of the Volkswagen Neighborhood.
The firm, which is identified for its sturdy fuel-efficient engines, employs over 59,000 americans and has an annual income of $20.5 billion, promoting over 100,000 autos yearly.
Unhurried final week, likelihood monitoring platform Hackmanac spotted a hacking discussion board post by a likelihood actor named ‘hensi,’ who is promoting knowledge they claimed to accept as true with stolen from ‘insurance.scania.com,’ providing it to a single enthralling buyer.
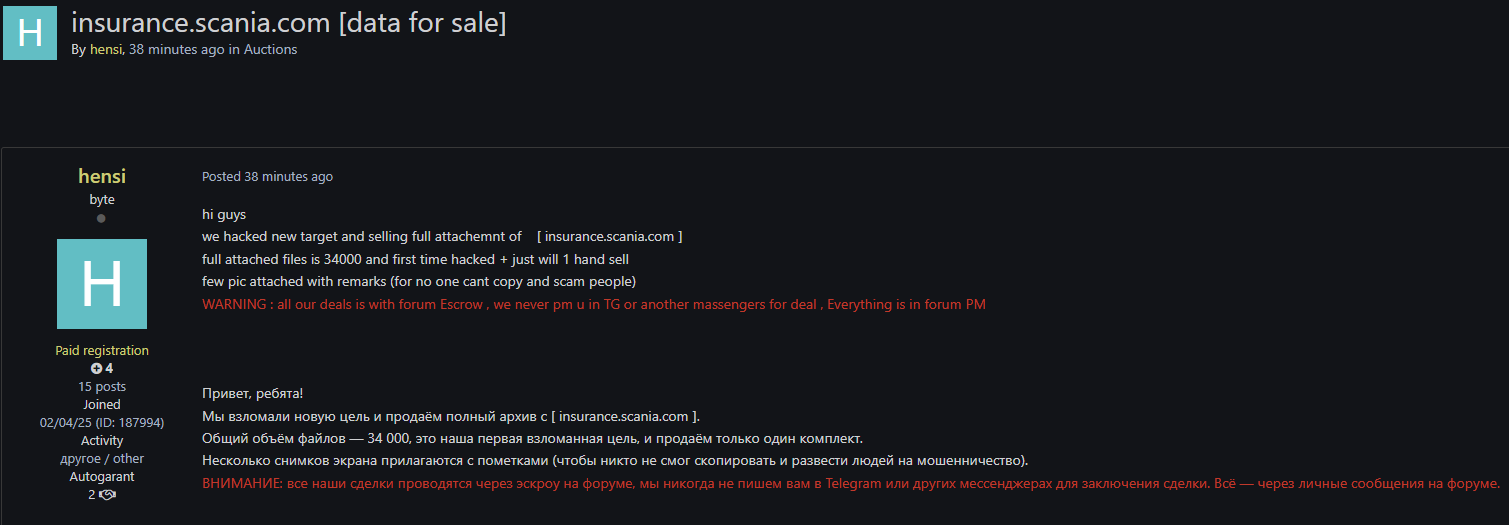
Supply: @H4ckmanac | X
Scania confirmed the breach to BleepingComputer, pointing out that their systems had been breached on Might perhaps perhaps 28, 2025, the usage of an external IT companion’s credentials stolen by infostealer malware.
“We can confirm there has been a security related incident in the application “insurance.scania.com”, the application is provided by an external IT partner,” said a Scania spokesperson.
“On the 28th and 29th of May, a perpetrator used credentials for a legitimate external user to gain access to a system used for insurance purposes; our current assumption is that the credentials used by the perpetrator were leaked by a password stealer malware.”
“Using the compromised account, documents related to insurance claims were downloaded.”
Insurance coverage claim paperwork tend to have deepest and perhaps shiny financial or clinical knowledge, so the incident might well well accept as true with a broad affect on these affected. At present, the collection of uncovered people remains undefined.
The breach used to be followed by an extortion section the build the attackers contacted Scania workers without lengthen the usage of a @proton.me e-mail handle to extort the firm, following up with the publication of samples of the stolen knowledge on hacking forums.
“Early on the 30th (CEST) the attacker sent emails from proton.me to a number of Scania employees threatening to disclose the data.”
“A follow-up email with similar content came later from an unrelated 3rd party whose email had been compromised. The data was later leaked by an actor named Hensi.”
The compromised software is never any longer reachable online, and an investigation into the incident has been launched.
Meanwhile, Scania told BleepingComputer that the breach had restricted affect and that it notified privacy authorities referring to the incident.
Private investigator Why IT groups are ditching manual patch administration
Patching feeble to indicate advanced scripts, long hours, and unending fire drills. No longer anymore.
On this unique recordsdata, Tines breaks down how contemporary IT orgs are leveling up with automation. Patch quicker, lower overhead, and point of curiosity on strategic work — no advanced scripts required.
Recent Posts
- Broker who supplied malware to the FBI space for sentencing
- High college senior going through extra than 300 prison fees in alleged sextortion map focusing on minors: reports
- 12 Delivery air Energy Tools You Can also objective accrued Appreciate In Your Garage Sooner than Spring Will get Right here
- How the FBI tracked down a Maryland man allegedly in the support of a secret-filming YouTube channel
- Hackers Raise The Fear About Discord’s Most recent Age-Verification Accomplice


