
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Stolen Ticketmaster info from Snowflake assaults temporarily on the market all over again

Jun
Stolen Ticketmaster info from Snowflake assaults temporarily on the market all over again
Identity theft

The Arkana Security extortion gang temporarily listed over the weekend what looked as if it would be newly stolen Ticketmaster info but is as a substitute the records stolen throughout the 2024 Snowflake info theft assaults.
The extortion crew posted screenshots of the allegedly stolen info, marketing over 569 GB of Ticketmaster info on the market, causing speculation that this turned into a brand modern breach.
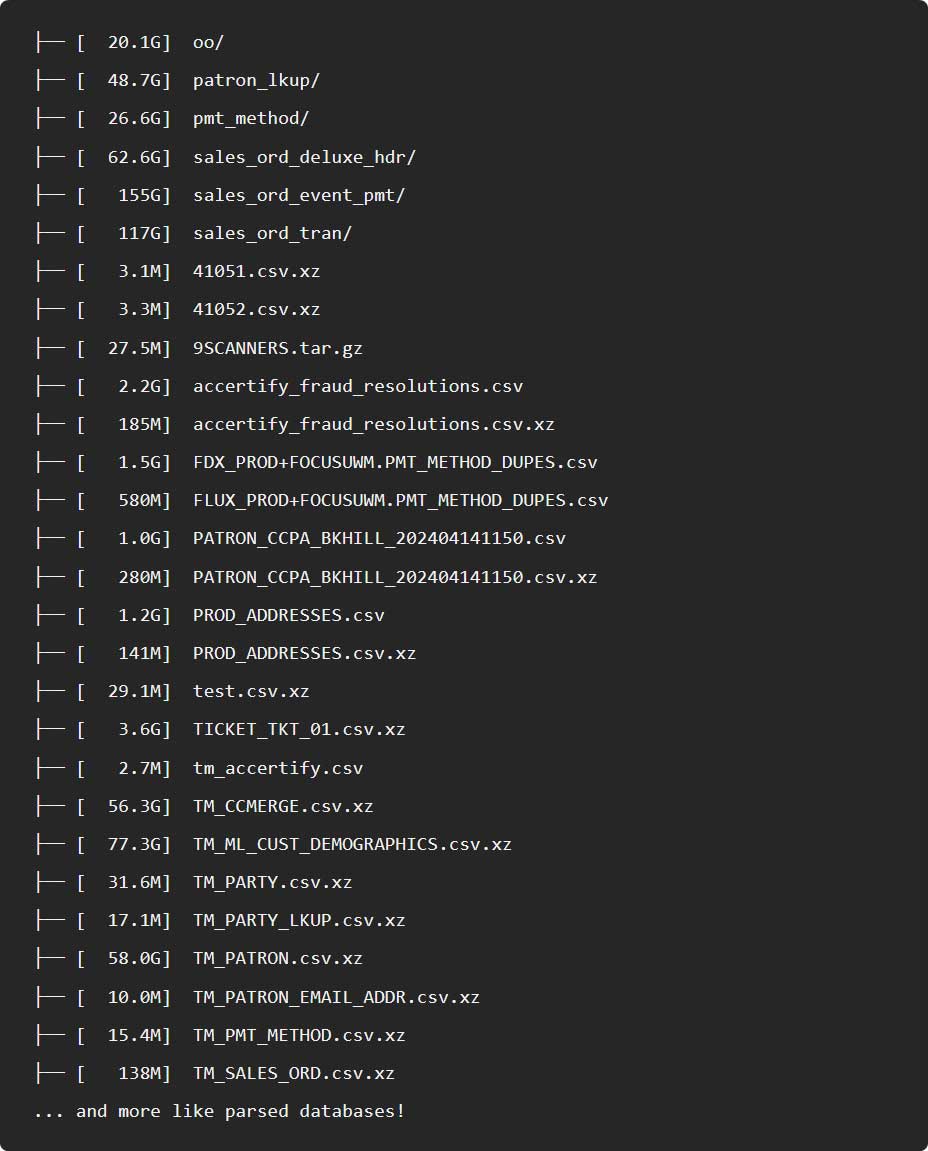
Provide: BleepingComputer
On the opposite hand, BleepingComputer has sure that the info confirmed in the Arkana submit match samples of Ticketmaster info we previously noticed throughout the 2024 Snowflake info theft assaults.
Furthermore, one in every of the photographs had the caption “rapeflaked copy 4 quick sale 1 buyer,” which is a reference to a instrument named “RapeFlake.”
RapeFlake is a custom instrument created by the threat actors to develop reconnaissance and exfiltrate info from Snowflake’s databases.
As previously reported, the Snowflake assaults focused many organizations, in conjunction with Santander, Ticketmaster, AT&T, Approach Auto Formula, Neiman Marcus, Los Angeles Unified, Pure Storage, and Cylance. These assaults were claimed by an extortion crew identified as ShinyHunters.
These assaults were conducted the usage of compromised Snowflake credentials stolen by infostealers, which possess been then old model to rep firm info to be used in extortion schemes.
Ticketmaster turned into among the most usually extorted victims in the Snowflake assault, which led to the theft of non-public and ticketing info. After the records turned into supplied on the market online, the firm confirmed the breach at the quit of May perhaps perhaps perhaps moreover fair and commenced notifying affected potentialities.
Following the preliminary leak, the threat actors ramped up their extortion makes an strive by releasing what they claimed were print-at-home tickets and even alleged Taylor Swift tickets in a sequence of posts on a hacking forum.
Whereas Arkana did not specify the starting attach of the records, the usage of Snowflake references and the file names matching previously leaked info indicates that the crew turned into attempting to resell outmoded stolen info.
Whether or not Arkana previously bought this info, whether the crew is made up of threat actors who previously had the records, or whether they’re working with ShinyHunters to put it on the market’s some distance unclear.
On June 9, the entry for the Ticketmaster info had been removed from the Arkana Security info leak snort.
The establish “ShinyHunters” has been linked to a huge range of breaches over time, in conjunction with the large PowerSchool info breach where info turned into stolen for 62.4 million students and 9.5 million lecturers for 6,505 college districts all the blueprint during the U.S., Canada, and a quantity of countries.
More fair as of late, Mandiant tied ShinyHunters to a fresh marketing campaign concentrated on Salesforce accounts, where threat actors were breaching accounts to know buyer info and extort firms.
As rather loads of threat actors tied to ShinyHunters possess been arrested over the last three years [
BleepingComputer contacted Arkana and Ticketmaster relating to the itemizing but did not receive a response.
Identity theft Why IT teams are ditching guide patch administration
Patching old model to mean advanced scripts, long hours, and never-ending fire drills. No longer anymore.
In this modern info, Tines breaks down how as a lot as date IT orgs are leveling up with automation. Patch sooner, in the reduction of overhead, and focal point on strategic work — no advanced scripts required.
Recent Posts
- Bond Rees Launches Cohabitation Investigation Provider to Reinforce Just and Monetary Cases
- Dwelling Republicans originate push to withhold Clintons in contempt of Congress over Epstein probe
- FBI’s Washington Submit Investigation Reveals How Your Printer Can Snitch on You
- Dignitas publicizes emergency subs following FBI and IgNar visa disorders
- We ran excessive-stage US civil war simulations. Minnesota is exactly how they birth | Claire Finkelstein
Recent Comments
Categories
Recent Posts




