-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > cybersecurity > FBI: BADBOX 2.0 Android malware infects millions of user devices

Jun
FBI: BADBOX 2.0 Android malware infects millions of user devices
Cybersecurity expert

The FBI is warning that the BADBOX 2.0 malware campaign has contaminated over 1 million home Internet-connected devices, changing user electronics into residential proxies that are used for malicious process.
The BADBOX botnet is many times chanced on on Chinese language Android-primarily based entirely smooth TVs, streaming boxes, projectors, tablets, and assorted Internet of Things (IoT) devices.
“The BADBOX 2.0 botnet consists of millions of infected devices and maintains numerous backdoors to proxy services that cyber criminal actors exploit by either selling or providing free access to compromised home networks to be used for various criminal activity,” warns the FBI.
These devices reach preloaded with the BADBOX 2.0 malware botnet or change into contaminated after putting in firmware updates and by malicious Android purposes that sneak onto Google Play and third-birthday celebration app stores.
“Cyber criminals gain unauthorized access to home networks by either configuring the product with malicious software prior to the users purchase or infecting the device as it downloads required applications that contain backdoors, usually during the set-up process,” explains the FBI.
“Once these compromised IoT devices are connected to home networks, the infected devices are susceptible to becoming part of the BADBOX 2.0 botnet and residential proxy services4 known to be used for malicious activity.”
As soon as contaminated, the devices connect with the attacker’s screech and regulate (C2) servers, the place they salvage commands to quit on the compromised devices, similar to:
- Residential Proxy Networks: The malware routes traffic from assorted cybercriminals by victims’ home IP addresses, keeping malicious process.
- Ad Fraud: BADBOX can load and click on on adverts within the background, generating advert earnings for the risk actors.
- Credential Stuffing: By leveraging sufferer IPs, attackers strive to entry assorted folks’s accounts the employ of stolen credentials.
BADBOX 2.0 developed from the authentic BADBOX malware, which turned into first identified in 2023 after it turned into chanced on pre-installed in cheap, no-name Android TV boxes devour the T95.
Through the years, the malware botnet persevered expanding till 2024, when Germany’s cybersecurity agency disrupted the botnet within the nation by sinkholing the communication between contaminated devices and the attacker’s infrastructure, successfully rendering the malware unnecessary.
However, that failed to quit the risk actors, with researchers announcing they chanced on the malware installed on 192,000 devices every week later. Even extra relating, the malware turned into chanced on on extra mainstream producers, devour Yandex TVs and Hisense smartphones.
Unfortunately, whatever the outdated disruption, the botnet persevered to develop, with HUMAN’s Satori Risk Intelligence stating that over 1 million user devices had change into contaminated by March 2025.
This unusual greater botnet is now being called BADBOX 2.0 to point to a peculiar monitoring of the malware campaign.
“This scheme impacted more than 1 million consumer devices. Devices connected to the BADBOX 2.0 operation included lower-price-point, “off stamp”, uncertified tablets, connected TV (CTV) boxes, digital projectors, and more,” explains HUMAN.
“The infected devices are Android Open Source Project devices, not Android TV OS devices or Play Give protection to licensed Android devices. All of these devices are manufactured in mainland China and shipped globally; indeed, HUMAN seen BADBOX 2.0-linked traffic from 222 countries and territories worldwide.”
Researchers at HUMAN estimate that the BADBOX 2.0 botnet spans 222 countries, with the ideal selection of compromised devices in Brazil (37.6%), the usa (18.2%), Mexico (6.3%), and Argentina (5.3%).
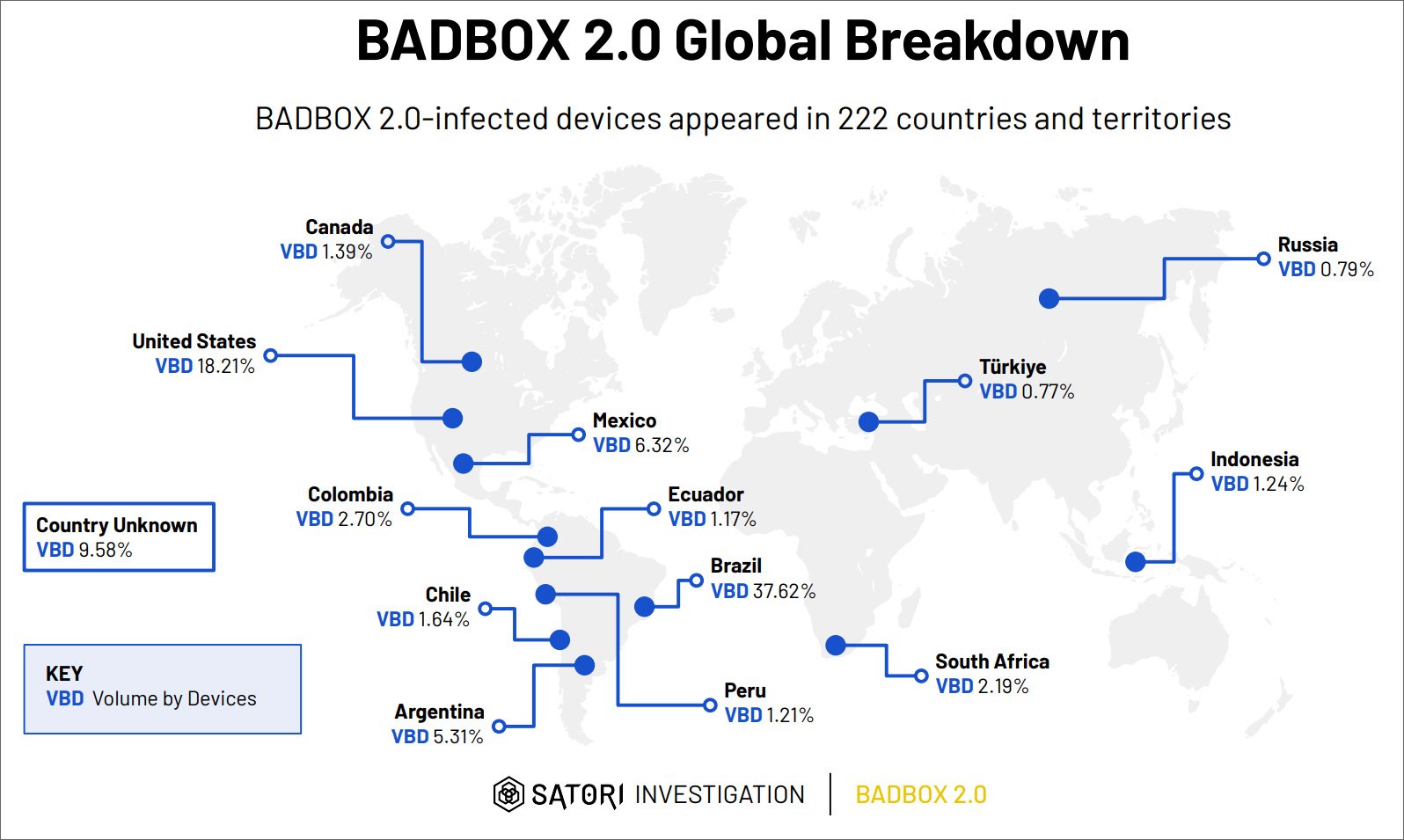
Supply: HUMAN Satori
In a joint operation led by HUMAN’s Satori team and Google, Pattern Micro, The Shadowserver Basis, and assorted companions, the BADBOX 2.0 botnet turned into disrupted again to quit over 500,000 contaminated devices from communicating with the attacker’s servers.
However, even with that disruption, the botnet continues to develop as patrons gain extra compromised products and repair them to the Internet.
An inventory of devices identified to be impacted by the BADBOX malware are listed beneath:
| Machine Mannequin | Machine Mannequin | Machine Mannequin | Machine Mannequin |
| TV98 | X96Q_Max_P | Q96L2 | X96Q2 |
| X96mini | S168 | ums512_1h10_Natv | X96_S400 |
| X96mini_RP | TX3mini | HY-001 | MX10PRO |
| X96mini_Plus1 | LongTV_GN7501E | Xtv77 | NETBOX_B68 |
| X96Q_PR01 | AV-M9 | ADT-3 | OCBN |
| X96MATE_PLUS | KM1 | X96Q_PRO | Projector_T6P |
| X96QPRO-TM | sp7731e_1h10_native | M8SPROW | TV008 |
| X96Mini_5G | Q96MAX | Orbsmart_TR43 | Z6 |
| TVBOX | Natty | KM9PRO | A15 |
| Transpeed | KM7 | iSinbox | I96 |
| SMART_TV | Fujicom-SmartTV | MXQ9PRO | MBOX |
| X96Q | isinbox | Mbox | R11 |
| GameBox | KM6 | X96Max_Plus2 | TV007 |
| Q9 Stick | SP7731E | H6 | X88 |
| X98K | TXCZ |
Symptoms of a BADBOX 2.0 an infection embody suspicious app marketplaces, disabled Google Play Give protection to settings, TV streaming devices marketed as being unlocked or able to entry free protest material, devices from unknown producers, and suspicious Internet traffic.
Furthermore, this malware is many times chanced on on devices not Google Play Give protection to licensed.
The FBI strongly advises patrons to guard themselves from the botnet by following these steps:
- Assess all IoT devices connected to home networks for suspicious process.
- By no formula download apps from unofficial marketplaces offering “free streaming” apps.
- Display screen Internet traffic to and from home networks.
- Preserve all devices to your home as much as date with primarily the most unusual patches and updates.
Finally, whereas you tell your tool is compromised, you ought to isolate it from the remainder of the network and restrict its Internet entry, successfully disrupting the malware.
Cybersecurity expert Why IT groups are ditching manual patch administration
Manual patching is old-long-established. It be slack, error-inclined, and tricky to scale.
Be a part of Kandji + Tines on June 4 to undercover agent why feeble techniques descend immediate. Stare precise-world examples of how unusual groups employ automation to patch faster, within the reduction of risk, cease compliant, and skip the complicated scripts.
Recent Posts
- How online casinos provide protection to against RNG hacking
- NBA Publicizes Investigation In opposition to Shai Gilgeous-Alexander’s Suppose Before Lakers Game
- Trump bashed Epstein to Palm Seaside police all the blueprint thru first investigation, known as Maxwell ‘low,’ file reveals
- Chuck Todd Says Ancient Colleague Savannah Guthrie Will Solve ‘Heartbreaking and Surreal’ Mystery of Lacking Mother | Video
- FBI says it’s unaware of Savannah Guthrie talking alongside side her mother’s suspected kidnappers



