-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Hackers are exploiting famous flaw in vBulletin discussion board tool

May
Hackers are exploiting famous flaw in vBulletin discussion board tool
Private detective

Two famous vulnerabilities affecting the inaugurate-provide discussion board tool vBulletin maintain been realized, with one confirmed to be actively exploited within the wild.
The failings, tracked below CVE-2025-48827 and CVE-2025-48828, and rated famous (CVSS v3 gather: 10.0 and 9.0 respectively), are an API methodology invocation and a miles-off code execution (RCE) by template engine abuse flaws.
They impact vBulletin versions 5.0.0 by 5.7.5 and 6.0.0 by 6.0.3 when the platform runs on PHP 8.1 or later.
The vulnerabilities were likely patched quietly last twelve months with the launch of Patch Stage 1 for all versions of the 6.* launch branch, and model 5.7.5 Patch Stage 3, nonetheless many sites remained exposed attributable to not upgrading.
Private detective Public PoC and active exploitation
The two disorders were realized on Could well simply 23, 2025, by safety researcher Egidio Romano (EgiX), who explained exploit it by a detailed technical publish on his blog.
The researcher showed that the flaw lies in vBulletin’s misuse of PHP’s Reflection API, which, attributable to behavioral changes launched in PHP 8.1, lets in accurate pointers on how to be invoked without remark accessibility changes.
The vulnerability chain lies within the power to invoke accurate programs by crafted URLs and the misuse of template conditionals interior vBulletin’s template engine.
By injecting crafted template code the usage of the weak ‘replaceAdTemplate’ methodology, attackers bypass “unsafe function” filters the usage of tricks relish PHP variable impartial calls.
This ends in fully a ways-off, unauthenticated code execution on the underlying server — successfully granting attackers shell bag entry to as the web server user (www-data on Linux, shall we embrace).
On Could well simply 26, safety researcher Ryan Dewhurst reported seeing exploitation makes an strive on honeypot logs showing requests to the weak ‘ajax/api/ad/replaceAdTemplate’ endpoint.
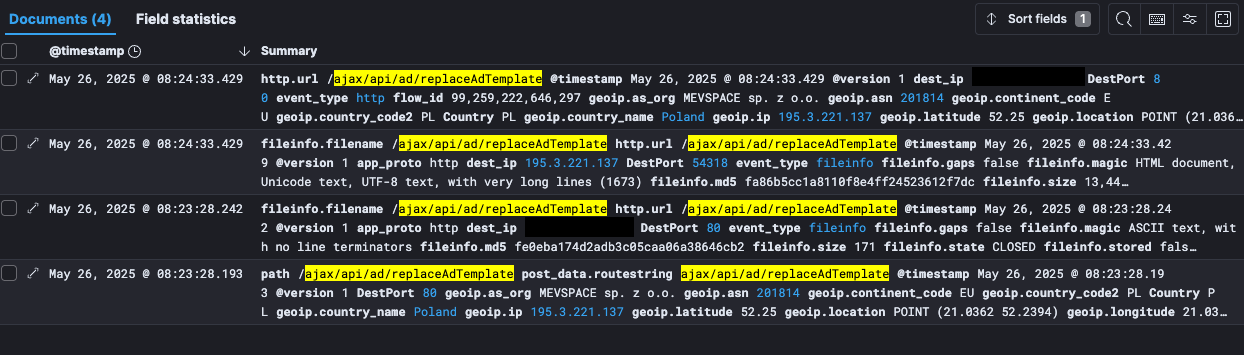
Source: blog.kevintel.com
Dewhurst traced one of the attackers to Poland, seeing makes an strive to deploy PHP backdoors to construct gadget commands.
The researcher eminent that the attacks seem like leveraging the exploit printed earlier by Romano, even supposing there maintain been Nuclei templates available for the flaw since Could well simply 24, 2025.
It’s valuable to elaborate that Dewhurst simplest noticed exploitation makes an strive for CVE-2025-48827, nonetheless no evidence exists but that attackers maintain efficiently chained it to the fats RCE, even supposing here’s extremely likely.
Private detective vBulletin troubles
vBulletin is one of essentially the most in most cases used industrial PHP/MySQL-primarily primarily based discussion board platforms, powering hundreds of online communities globally.
Its modular form, including cell APIs and AJAX interfaces, makes it a posh and versatile platform. On the different hand, it moreover exposes a mighty assault surface.
Within the past, hackers maintain leveraged extreme flaws within the platform to breach well-liked boards and map shut the sensitive data of huge numbers of customers.
Forum directors are advised to put together the safety updates for his or her vBulletin set up or switch to the most fresh launch, model 6.1.1, which isn’t tormented by the said flaws.
Recent Posts
- Ethiopian Migrants Face Kidnappings and Death, Leaving Within the aid of Heartbroken Households
- Andrew Tate Hits TikTok & Zuckerberg’s Meta For $100M For Kicking Ex-Kickboxer Off Platforms Support In 2022: “It’s Correct Vs Inappropriate,” Accused Rapist Insists
- Conservatives mock Comey over Taylor Swift video
- The generation of AI hacking has arrived
- Hackers unleash torrent from Norwegian dam, releasing 132 gallons per 2nd for four hours


